Microsoft pins MOVEit Transfer vulnerability on Cl0p
Microsoft said the recent attack that exploited the MOVEit Transfer 0-day vulnerability was likely carried out by the Cl0p ransomware group.
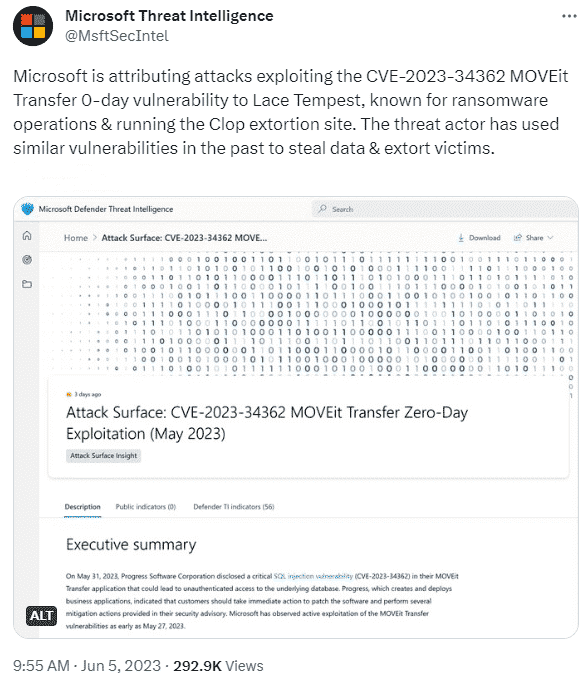
The researchers said, "Microsoft is attributing attacks exploiting the CVE-2023-34362 MOVEit Transfer 0-day vulnerability to Lace Tempest, known for ransomware operations & running the Clop extortion site," the researchers said.
MOVEit Transfer is hosted file transfer software developed by U.S. developer Ipswitch. The 0-day vulnerability affects MOVEit Transfer's servers, allowing an attacker to access and download data stored there.
The vulnerability has already affected major companies through third-party attacks. For example, British Airways (BA) said an attack on its payroll service provider, Zellis, affected the company's employees.
BA said in a statement that they had learned that they were one of the companies affected by the Zellis cybersecurity incident, which occurred through one of their third-party vendors, MOVEit.
Cl0p, a ransomware group presumably linked to Russia, confirmed Microsoft's attribution of the exploit to Reuters' Raphael Satter and said more victims would appear on the group's blog.
Earlier this year, Cl0p made headlines after successfully exploiting Fortra's GoAnywhere vulnerability, a zero-day exploit. The group compromised a number of companies, including Shell, Hatch Bank, Bombardier, Stanford University, Rubrik, Saks Fifth Avenue and more.
"Microsoft strongly urges organizations affected by the CVE-2023-34362 MOVEit Transfer vulnerability to apply security patches and perform mitigation actions provided by Progress in their security advisory," the Microsoft team said.
Cl0p ransomware has been around since 2019 - a long time in the ever-changing ransomware landscape. The group has also been at the forefront of the ransomware world, with estimated spending reaching $500 million in November 2021.
That same year, Ukrainian law enforcement conducted a major crackdown on the group, arresting several individuals and dismantling the group's server IT infrastructure. The arrests ultimately forced the group to cease operations between November 2021 and February 2022. However, the group has been steadily recovering since then.
銆怰esources銆戔棌The Achilles heel of AI startups: no shortage of money, but a lack of training data
【Web Intelligence Monitoring】●Advantages of open source intelligence
【Artificial Intelligence】●Advanced tips for using ChatGPT-4
銆怰esources銆戔棌The 27 most popular AI Tools in 2023
銆怤etwork Security銆戔棌9 popular malicious Chrome extensions
【News】●AI-generated fake image of Pentagon explosion goes viral on Twitter
【Open Source Intelligence】●10 core professional competencies for intelligence analysts
銆怬pen Source Intelligence銆戔棌5 Hacking Forums Accessible by Web Browsers



