Attackers can unlock smartphones with fingerprint brute-force
Researchers have discovered an inexpensive attack technique that can be used to brute force fingerprints on smartphones to bypass user authentication and seize control of the device.
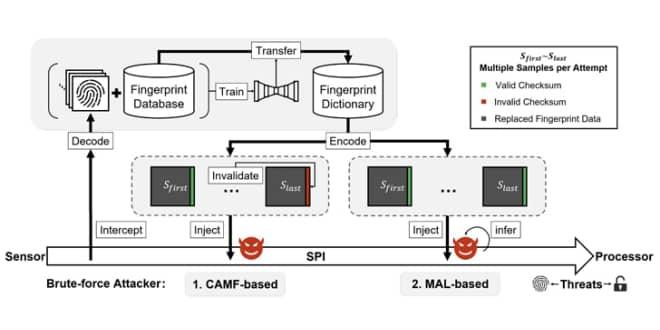
The method, dubbed BrutePrint, bypasses restrictions set in response to failed biometric authentication attempts by exploiting two zero-day vulnerabilities in the Smartphone Fingerprint Authentication (SFA) framework.
These flaws, Cancel-After-Match-Fail (CAMF) and Match-After-Lock (MAL), exploit a logic flaw in the authentication framework, which is caused by inadequate protection of fingerprint data on the fingerprint serial peripheral interface (SPI) to the sensor.
The result is "a hardware approach to do man-in-the-middle (MitM) attacks for fingerprint image hijacking," researchers Yu Chen and Yiling He said in a research paper. "BrutePrint acts as a middleman between fingerprint sensor and TEE [Trusted Execution Environment]."
Its core goal is to be able to perform unlimited fingerprint image submissions until a match occurs. However, it assumes that the threat actor already possesses the relevant target device.
In addition, it requires the adversary to have a fingerprint database and a setup consisting of a microcontroller board and an auto-answerer that can hijack the data sent by the fingerprint sensor to launch an attack for as low as $15.
The first of the two vulnerabilities that make this attack possible is CAMF, which allows to increase the fault tolerance of the system by invalidating the checksum of the fingerprint data, thus providing the attacker with unlimited attempts.
MAL, on the other hand, uses a side channel to infer a match of the fingerprint image on the target device, even if it goes into lockdown mode after multiple repeated login attempts.
The researchers explained that while the lock mode was further checked in Keyguard to disable unlocking, the authentication results were made by the TEE. Since successful authentication results are returned immediately when matching samples are met, it is possible that the side-channel attack could infer results from behaviors such as response time and number of images acquired.
In the experimental setup, BrutePrint was evaluated against 10 different smartphone models from Apple, Huawei, OnePlus, OPPO, Samsung, Xiaomi and vivo, with unlimited attempts on Android and HarmonyOS and 10 additional attempts on iOS devices.
The findings come as a group of academics detailed a hybrid side-channel that takes advantage of the "three-way tradeoff between execution speed (i.e., frequency), power consumption, and temperature" in modern system-on-chips (SoCs) and GPUs to conduct "browser-based pixel stealing and history sniffing attacks" against Chrome 108 and Safari 16.2.
The attack, called Hot Pixels, uses this behavior to launch a website fingerprinting attack and uses JavaScript code to obtain the user's browsing history. This is achieved by designing a computationally intensive SVG filter that leaks pixel colors by measuring rendering time and secretly collects information with up to 94% accuracy.
Apple, Google, AMD, Intel, Nvidia, and Qualcomm have acknowledged these problems. The researchers also recommend "prohibiting SVG filters from being applied to iframes or hyperlinks" and preventing unauthorized access to sensor readings.
BrutePrint and Hot Pixels also followed Google's lead in finding 10 security flaws in Intel's Trusted Domain Extensions ( TDX ) that could lead to arbitrary code execution, denial-of-service conditions and loss of integrity.
Relatedly, Intel CPUs were also found to be vulnerable to side-channel attacks that exploit execution time changes caused by changing EFLAGS registers during transient execution to decode data without relying on caches.
【Web Intelligence Monitoring】●Advantages of open source intelligence
銆怬pen Source Intelligence銆戔棌5 Hacking Forums Accessible by Web Browsers
【Open Source Intelligence】●10 core professional competencies for intelligence analysts
【Artificial Intelligence】●Advanced tips for using ChatGPT-4
【Dark Web】●5 Awesome Dark Web Links
【News】●AI-generated fake image of Pentagon explosion goes viral on Twitter



