Millions of WordPress websites attacked by malware
In April 2023, tech media outlets such as Bleeping Computer and TechRadar began reporting that cyber attackers had exploited vulnerabilities to attack WordPress, gaining access through a combination of the popular plugins Elementor Pro Premium (web page builder) and WooCommerce (online storefront).
The vulnerability is reported to have a CVSS score of 8.8, but the official CVE number remains undetermined until May 2023. Sites running Elementor Pro 3.11.6 or earlier and with the WooCommerce plugin activated are advised to upgrade ElementorPro to at least 3.11.7 or risk an authenticated user achieving full control of the site by exploiting compromised access controls, the most serious of the OWASP Top 10 risks.
While reports of this vulnerability have been widely circulated on the Internet, this article will focus on the widespread and highly persistent malware injection campaign "Balada".
What is Balada?
Cybersecurity firm Sucuri has been tracking the Balada injection campaign since 2017, but only recently gave a name to the long-running campaign. Balada typically exploits known but unpatched WordPress plugins and other software vulnerabilities, among other things, to achieve an initial infection, which then spreads and remains persistent by executing a series of choreographed attack strategies, cross-site infections and installing backdoors.
Because Elementor Pro and WooCommerce compromise paths allow authenticated users to modify WordPress configurations, create administrator accounts or inject URL redirects into site pages or posts, Balada can steal database credentials, archived files, log data or under-protected valuable documents while establishing numerous command and control channels to achieve persistence.
Sucuri noted that Balada injection activity follows a defined monthly schedule, typically starting at the end of the week and ending around mid-week.
Balada primarily exploits Linux-based hosts, but Microsoft-based Web servers, such as IIS, are not immune.
Balada follows the practices used in other contemporary malware campaigns, using new registration domains consisting of random, unrelated words to entice victims to click and redirect them to sites that serve malicious loads.
These sites are often fronted with fake IT support services, cash reward notifications, or even secure authentication services like CAPTCHAs. The chart below summarizes the initial attack vectors Balada will seek to exploit, the services or plugins it will attempt to abuse, and some of the recognized persistent vectors. Once implanted, Balada will be very difficult to remove.
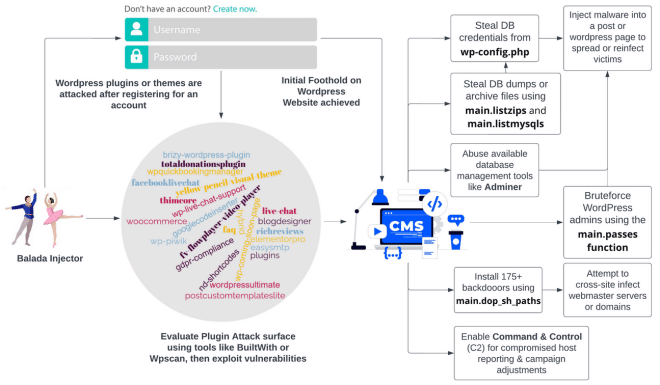
Identifying Balada Injections
Sucuri's research further confirms that Balada's primary malware routines are typically located in the " C:/Users/host/Desktop/balada/client/main.go" path on the infected device. A semi-maintained Virus Total collection highlights common file hashes, URLs and other indicators associated with the malware and infections provided by Balada.
Sucuri also repeatedly observed in the logs of compromised machines that, starting in late 2020, Balada leveraged an outdated but recurring user agent "Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/84.0.4147.125 Safari/537.36". Since 2017, Balada activity has been associated with over 100 unique domains. balada uses the " main.ex_domains" feature to store and reuse domains for future attacks during monthly infection campaigns.
Defensive Measures
For prevention of Balada infections, in addition to ensuring that web server hosts, web plugins, themes or related software are kept up to date, DNS security should be ensured through solutions such as Cisco Umbrella or DNSFilter. These can provide network-level or roaming client solutions to identify, block redirection attempts and DNS requests from known malicious sites.
Enterprises should also enforce strong password policies, privileged users must meet multi-factor authentication or other conditional access policies, and the creation of privileged accounts should be alerted to the appropriate teams. In addition enterprises should consider implementing or periodically evaluating the following:
路 Regularly audit Web applications for necessary plug-ins, themes or software and remove all unnecessary or unused software.
路 Conduct internal and routine penetration testing or similar assessments of Web applications to identify exploitable vulnerabilities before Balada.
路 Enable file integrity monitoring (FIM) for critical system files.
路 Strictly limit access to sensitive files such as wp-config, website backup data, log files or database archives, and ensure that data retention policies purge old versions of this data when no longer needed.
路 Disable unnecessary or insecure server services and protocols, such as FTP.
銆怬pen Source Intelligence銆戔棌5 Hacking Forums Accessible by Web Browsers
【Dark Web】●5 Awesome Dark Web Links
銆怰esources銆戔棌The 27 most popular AI Tools in 2023
銆怤ews銆戔棌Access control giant hit by ransom attack, NATO, Alibaba, Thales and others affected
【Artificial Intelligence】●Advanced tips for using ChatGPT-4
【Web Intelligence Monitoring】●Advantages of open source intelligence



