How to use WindowSpy to monitor the behavior of target users?
WindowSpy is a powerful Cobalt Strike Beacon object file that can help a wide range of researchers to monitor the behavior of target users. The main goal of the tool is to trigger the monitoring function only on certain targets, such as browser login pages, sensitive files, vpn logins, etc. The aim is to increase the invisibility of users during surveillance by preventing the detection of repeated use of surveillance features (e.g. screenshots).
In addition, the tool can significantly save the red team researchers' time in sifting through user monitoring data.
WindowSpy:
https://github.com/CodeXTF2/WindowSpy
WindowSpy running mechanism
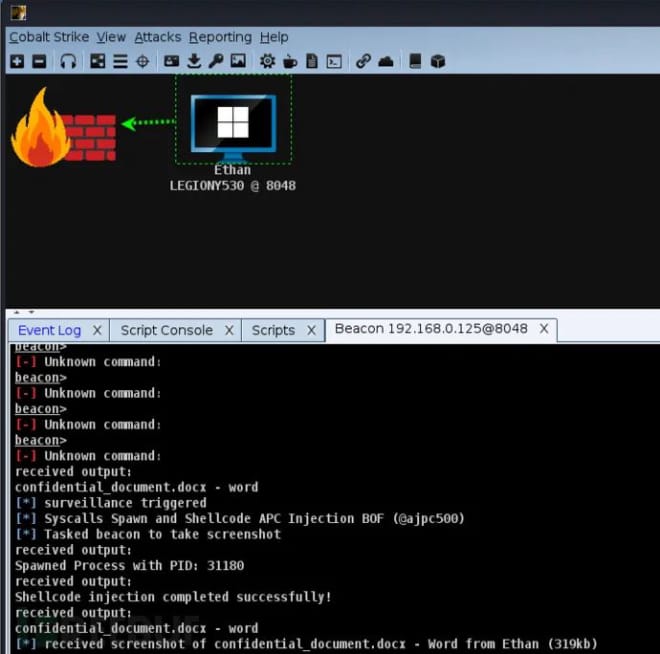
BOF runs automatically on the target every time a Beacon is detected and comes with a hard-coded list of strings that are commonly found in window titles such as login, admin, control panel, vpn, etc. We can customize this list and recompile it. It enumerates the visible windows and compares the titles with the string list. If it detects any of them, it will trigger the local aggressorscript function called spy() defined in WindowSpy.cn. By default, it will take a screenshot. We can customize this function as needed, such as keystroke logging, WireTap, webcam, etc.
The spy() function has 1 argument, $1 being the beacon id of the beacon that triggered it.
Installation
First, the project source code needs to be cloned locally using the following command:
git clone https://github.com/CodeXTF2/WindowSpy.git
Next, just load the WindowsSpy.cna script from the project into Cobalt Strike.
Building from source
1. Open the WindowSpy.sln solution file in Visual Studio
2. Build for target BOF (x64/x86)
Once loaded, the tool will automatically run whenever a Beacon is detected and trigger the corresponding action.
【News】●AI-generated fake image of Pentagon explosion goes viral on Twitter
【Open Source Intelligence】●10 core professional competencies for intelligence analysts
銆怬pen Source Intelligence銆戔棌5 Hacking Forums Accessible by Web Browsers
銆怰esources銆戔棌The Achilles heel of AI startups: no shortage of money, but a lack of training data
【Dark Web】●5 Awesome Dark Web Links
【Web Intelligence Monitoring】●Advantages of open source intelligence
銆怤etwork Security銆戔棌9 popular malicious Chrome extensions



