Open Source Intelligence: How to find anyone's email address
Google Dorks
· “@example.com” site:example.com — search for all emails on a given domain.
· HR “email” site:example.com filetype:csv | filetype:xls | filetype:xlsx — find HR contact lists on a given domain.
· site:example.com intext:@gmail.com filetype:xls — extract email IDs from Google on a given domain.
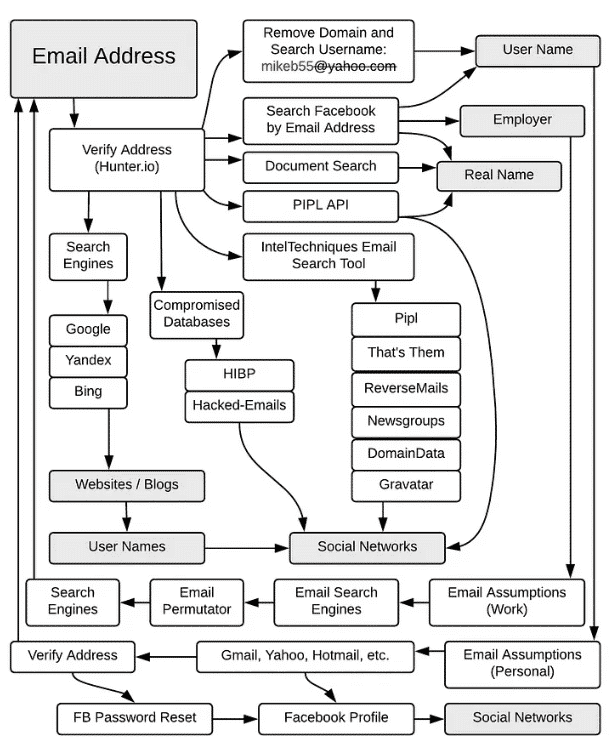
Email tools
· Hunter — performs fast scan of the domain name for email addresses and reveals its common pattern.
· Email permutator — generates permutations of up to three domains at which target is likely to have an email address. Supports multiple variables input to generate custom results.
· Proofy — allows bulk email validation which is useful when you generated a list of emails using a permutation tool and want to check all of them at once.
· Verifalia — validates single email addresses for free without registration. To use bulk validation you have to sign up.
Browser plugins
· Prophet — reveals more about people. It uses an advanced engine to predict the most likely email mix for a given person based on name, company, and other social data. Prophet then validates the generated emails to ensure they are correct and deliverable.
· OSINT browser extension — includes many useful links, including links for email search and verification. Compatible with Firefox and Chrome.
· LinkedIn Sales Navigator — chrome plugin that displays associated Twitter accounts and rich LinkedIn profile data directly in Gmail.
Compromised Databases
Data breaches have become a big problem, and recently we've been seeing more and more data dumps. Security researcher Troy Hunt collected the published data, stripped the passwords, assigned the emails to the breaches they were involved in, and uploaded them to haveibeenpwned.com. While the fact of the breach itself may not be as important, what is important is that via email you may be able to get a list of services that the person used or at least used.
Another option is to use dehashed.com. For free accounts, it works similar to Troy Hunt's site, but for valid subscriptions it will display the password in clear text or as a password hash. From an open source intelligence perspective, we need it to search if it has been used on some other site - another way to find out which services the person uses or at least has used. A search by password or its hash value will not only show which site it was used on, but also the email address associated with it. Thus, we can obtain the email of the target, which we would otherwise not have access to. It is important to note that if the password is not unique, we may get false positives because others may also use it.
【Dark Web】●5 Awesome Dark Web Links
銆怤etwork Security銆戔棌9 popular malicious Chrome extensions
銆怰esources銆戔棌The Achilles heel of AI startups: no shortage of money, but a lack of training data
【News】●AI-generated fake image of Pentagon explosion goes viral on Twitter
銆怬pen Source Intelligence銆戔棌5 Hacking Forums Accessible by Web Browsers
銆怰esources銆戔棌The 27 most popular AI Tools in 2023



