New browser file archiver can abuse ZIP domains to spread malware
A new "File Archivers in the Browser" phishing tool has been tested to abuse ZIP domain names to display fake WinRAR or Windows File Explorer windows in browsers to lure users into launching malicious files.
The ZIP domain name is one of eight new premium domain names (TLDs) launched by Google in May that users can use to host websites or email addresses. Since the domain names were released, there has been considerable discussion about whether they might pose a cybersecurity risk to users.
While some experts believe this concern is exaggerated, the main possible problem is that some websites automatically turn a string ending in '.zip' (such as setup.zip) into a clickable link that can be exploited by malware for attack and propagation.
Now, security researcher mr.d0x has developed a rather deceptive phishing toolkit. The toolkit can be used to embed a fake WinRar window directly into the browser when opening a .zip domain, making it appear as if the user has opened a ZIP archive.
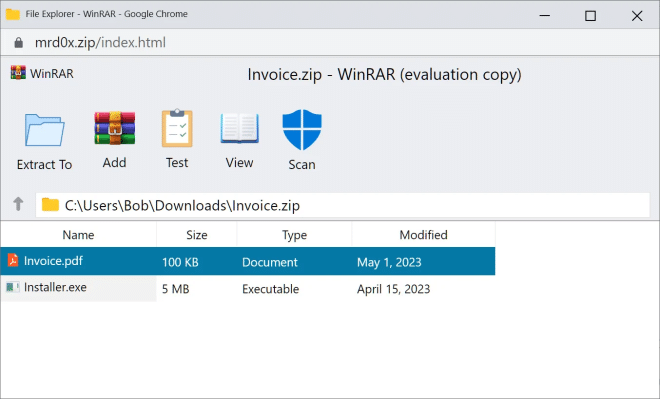
The fake window is so realistic that it even contains a fake security scan button which, when clicked, indicates that the file has been scanned and no threats have been detected.
Although the toolkit still displays the browser address bar, it may still trick some users into thinking it is a legitimate WinRar archive. In addition, the toolkit can be further improved with CSS and HTML.
Phishing Toolkit Abuse
mr.d0x believes that the phishing toolkit can be used for credential theft and to spread malware. For example, if a user double-clicks on a PDF in a fake WinRar window, he or she may be redirected to another page that requires account credentials to view the file.
The toolkit can also be used to spread malware by displaying a PDF file that downloads an .exe with a similar name when clicked. For example, a fake archive window might display the document.pdf file, but download the document.pdf.exe malware when clicked.
Since Windows does not display file extensions by default, users will only see a PDF file in their download folder and may double-click to open it without realizing it is an executable file.
Of particular note is that when Windows searches for a file, if it does not find it, it will attempt to open the searched string in the browser. If the string is a legitimate domain name, then the corresponding website will be opened.
Obviously, if a zip domain name with the same name as a regular file is registered, the operating system will automatically open the site in the browser if the user performs a search in Windows. If the site hosts the "File Archivers in the Browser" phishing toolkit, it can trick the user into thinking that WinRar is displaying a real ZIP archive.
This technique illustrates how ZIP domains can be abused for phishing attacks. But no matter how clever it is, such attacks can be avoided if users can increase their security awareness and not click to open any suspicious files.
銆怰esources銆戔棌The Achilles heel of AI startups: no shortage of money, but a lack of training data
銆怰esources銆戔棌The 27 most popular AI Tools in 2023
【Open Source Intelligence】●10 core professional competencies for intelligence analysts
【Artificial Intelligence】●Advanced tips for using ChatGPT-4
【Web Intelligence Monitoring】●Advantages of open source intelligence
銆怤ews銆戔棌Access control giant hit by ransom attack, NATO, Alibaba, Thales and others affected



