History of the Dark Web
Related: What is the dark web?
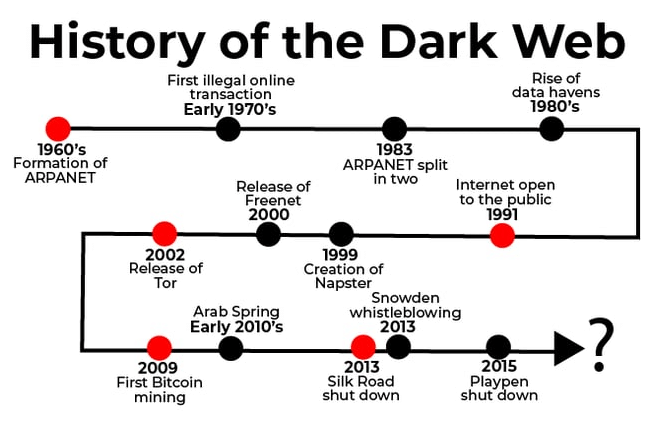
The dark web itself was not actually created; it is simply a part of the Internet.
The concept of anonymous online communication networks is at the heart of the Dark Web, dating back to the creation of ARPANET in the 1960s.
The Internet was released to the world around 1983 and quickly became popular as the world began to become more and more connected. As the Internet grew in popularity, so did the question of where all the data should be stored. The response came in the form of a "data haven".
Data havens function similarly to tax havens in that large amounts of data can be exported to countries with lax laws so that it does not fall into the hands of their own governments. The rise of data havens indicates a growing concern for online privacy, a concern later shared by users of the dark web.
In 2000, Freenet was released, a free software that allowed you to share files, browse and post "freesites" anonymously.
In 2002, Tor, a private Internet browsing network, was finally released to the world, and Tor changed the face of the Internet forever. By creating an environment where people could browse freely and anonymously online, the creators of Tor opened the door to the underbelly of the Internet.
The history of the dark web is filled with government influence. "Onion Routing" - the core principle that allows Tor to maintain its users' anonymity - was developed and funded by the U.S. federal government in the mid-1990s.
Onion Routing was created to protect individuals in the intelligence community by allowing them to communicate anonymously. It also helped protect whistleblowers, allowed citizens and journalists living under oppressive regimes to think and express themselves freely, and kept many others out of harm's way by protecting their anonymity. Even today, it continues to serve the same purpose for many people around the world.
Onion Routing was originally developed at the U.S. Naval Research Laboratory by scientists Paul Syverson, David Goldschlag and Michael Reed. Development of the project continued through the Defense Advanced Research Projects Agency (DARPA) until the U.S. Navy received a patent for Onion Routing in 1998.
Although the creators of Tor had good intentions, they could not have known that their invention would have a widespread impact on criminal activity.
In 2009, Bitcoin was released.
Before the invention of cryptocurrency, illegal transactions on the dark web were difficult to complete because customers could be located thousands of miles away and neither party wanted to risk using credit cards or PayPal to make transactions because they would leave a paper trail.
Cryptocurrency, a form of digital currency that facilitates anonymous transactions, is the answer to this long-standing problem. While different forms of cryptocurrency have been developed since the 1990s, it wasn't until 2009 that an offering called Bitcoin was perpetuated.
The first bitcoin was "mined" by a man named Satoshi Nakamoto, effectively starting a revolution in illegal online transactions. Bitcoin solved a problem that previous versions of cryptocurrency could not - it had a special accounting ledger that prevented users from copying funds.
As the problem of anonymous transactions was solved, illegal sales on the dark web proliferated.
Although the Dark Web witnessed an increase in illegal transactions during the 2010s, it served a benevolent purpose during the Arab Spring in late 2010.
The release of the Tor browser made it easier for users and activists who needed it during this time to access it. tor not only protects people's online identities, but also allows them to access critical resources, social media, and blocked websites.
After Silk Road was seized, many similar sites followed and still do to this day. As long as the need for anonymity exists online, the dark web will exist.
【Open Source Intelligence】●10 core professional competencies for intelligence analysts
【Dark Web】●5 Awesome Dark Web Links
銆怰esources銆戔棌The Achilles heel of AI startups: no shortage of money, but a lack of training data
【Web Intelligence Monitoring】●Advantages of open source intelligence
銆怬pen Source Intelligence銆戔棌5 Hacking Forums Accessible by Web Browsers



