Mastermind of Twitter 2020 cyberattack pleads guilty and gets 70 years in prison
A British man has pleaded guilty to the July 2020 Twitter attack that stole numerous high-profile accounts and defrauded other users of the platform.
Joseph James O'Connor, who goes by the online alias PlugwalkJoe, pleaded guilty to wrongdoing in cyberstalking and multiple incidents involving computer hacking, including the July 2020 hack of Twitter, the U.S. Department of Justice (DoJ) said.
The 23-year-old hacker was extradited from Spain on April 26 after the Spanish National Court granted the Justice Department transfer of O'Connor to the United States in February.
The massive hack, which occurred on July 15, 2020, involved O'Connor and his co-conspirators stealing 130 Twitter accounts that included those of Barack Obama, Bill Gates and Elon Musk and running a cryptocurrency scam through them, netting $120,000 in a matter of hours.
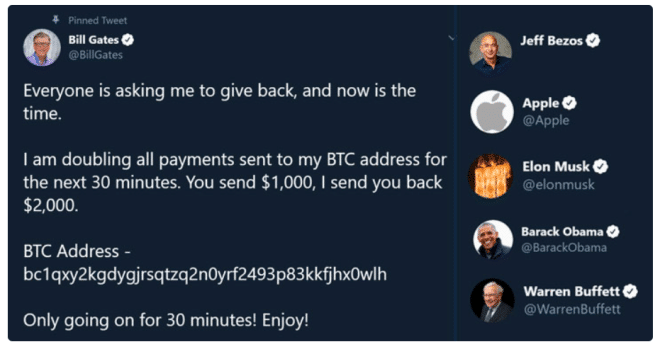
The attack was carried out by gaining access to the Twitter backend through social engineering techniques and then using that entry point to steal accounts and in some cases sell account access to others.
O'Connor is one of four people accused of carrying out the Twitter hack. Nima Fazeli and Graham Ivan Clark were arrested in the same month, while O'Connor was arrested a year later in July 2021 in the town of Estepona by Spanish authorities.
Mason Sheppard has not yet been arrested, according to the BBC's Joe Tidy. Clark was sentenced to three years in prison after pleading guilty to 30 felony charges in March 2021.
In addition to the Twitter incident, the defendant was also charged with criminal hacking of TikTok and Snapchat user accounts, and stalking a teenage victim online.
This required the attackers to conduct SIM-swap attacks on two victims to gain illegal access to their Snapchat and TikTok accounts, respectively, as well as make false emergency calls to law enforcement about a third victim, claiming the other was about to shoot someone.
The SIM card exchange occurs when the fraudster contacts a telecommunications service provider in the victim's name to port the target's cell phone number to a SIM card under their control, resulting in the victim's calls and messages being routed to a malicious device under the attacker's control.
The miscreants then used control of the victim's cell phone number to steal the victim's bank accounts and other services, often through the use of call- or SMS-based two-factor authentication.
O'Connor and his co-conspirators are then accused of stealing $794,000 from a New York City cryptocurrency company between March and May 2019 using SIM card swapping techniques.
After stealing the cryptocurrency, O'Connor and his co-conspirators laundered it through dozens of transfers and transactions, and used a cryptocurrency exchange service to convert some of it into bitcoin. A portion of the stolen cryptocurrency was deposited into O'Connor's private account.
The Justice Department has now seized approximately $794,000 of his stolen funds. O'Connor is scheduled to be sentenced on June 23rd, and IMO the maximum sentence for all charges is over 70 years.
銆怰esources銆戔棌The 27 most popular AI Tools in 2023
【Web Intelligence Monitoring】●Advantages of open source intelligence
【Open Source Intelligence】●10 core professional competencies for intelligence analysts
銆怤ews銆戔棌Access control giant hit by ransom attack, NATO, Alibaba, Thales and others affected
【Dark Web】●5 Awesome Dark Web Links



