The Unseen Battle: How Cybercrime Investigations Unveil Digital Threats
In today’s digital age, the proliferation of cybercrime presents a significant challenge for law enforcement and cybersecurity professionals. From phishing scams to ransomware attacks, cybercriminals employ sophisticated methods to exploit vulnerabilities. Understanding cybercrime investigation is crucial for safeguarding sensitive information and maintaining digital security. This article delves into the complexities of cybercrime investigations, highlighting the essential steps and methods used to combat these pervasive threats.

Understanding Cybercrime Investigation
Cybercrime investigation involves identifying, analyzing, and mitigating computer-based crimes and other forms of malicious activity that occur in cyberspace. This process entails several critical steps:
Identifying and Analyzing Digital Evidence
Investigators track and examine digital evidence to uncover the perpetrators and their motives.
Assessing the Situation
Learning about the case and evaluating the circumstances.
Conducting the Initial Investigation
Starting the investigation by gathering preliminary information and evidence.
Identifying Potential Evidence
Recognizing possible sources of digital evidence, such as computers, mobile devices, and network logs.
Securing Devices
Ensuring that digital evidence is not altered or destroyed by preserving the device’s current state.
Obtaining Court Orders
Acquiring the necessary legal permissions to access and analyze digital data.
Analyzing Results with the Prosecutor
Collaborating with legal professionals to interpret the evidence and build a case.
Cybercrime investigation is essential for combating various types of cyber crimes, such as hacking, phishing, malware, data breaches, and identity theft. It requires the use of specialized tools and techniques, meticulous planning, information gathering, and the proper handling of digital evidence.
Investigators must stay up-to-date with the latest techniques and tools to effectively address the evolving nature of cyber threats. This continuous learning ensures they can protect businesses and individuals from the growing risks posed by cybercriminals and bring offenders to justice.
The importance of cybercrime investigation cannot be overstated, as it plays a critical role in safeguarding against the significant risks to businesses, governments, and individuals worldwide.
Top 5 Cyber Crimes
Cybercrime encompasses a wide array of illegal activities involving computers and networks. Here are five prevalent types of cyber crimes that both businesses and individuals need to be vigilant about:
Phishing and Scams
Phishing involves tricking individuals into revealing sensitive information by sending fraudulent emails or messages. These attacks often appear to come from legitimate sources and aim to steal personal data or install malware on the target's system.
Identity Theft
This crime occurs when a cybercriminal uses another person’s personal information, such as credit card numbers or personal identification details, without permission. The stolen information is then used to commit fraud or other crimes.
Ransomware Attacks
Ransomware is a type of malware that encrypts a victim's data, rendering it inaccessible. The attacker then demands a ransom payment to restore access to the encrypted files. Ransomware attacks can cause significant disruption and financial loss.
Unauthorized Access and Misuse
Commonly known as hacking, this crime involves gaining unauthorized access to private computer systems or networks. Hackers may steal data, disrupt operations, or use the compromised systems for illegal activities.
Internet Fraud
This broad category includes various fraudulent activities conducted over the internet, such as online scams, banking fraud, and theft of services. Internet fraud exploits the internet’s vast reach to deceive victims and steal their money or personal information.
These cyber crimes can be executed through different methods, including social engineering, exploiting security vulnerabilities, and deploying malicious software. It is crucial for both businesses and individuals to implement robust security measures and remain vigilant to mitigate these risks.
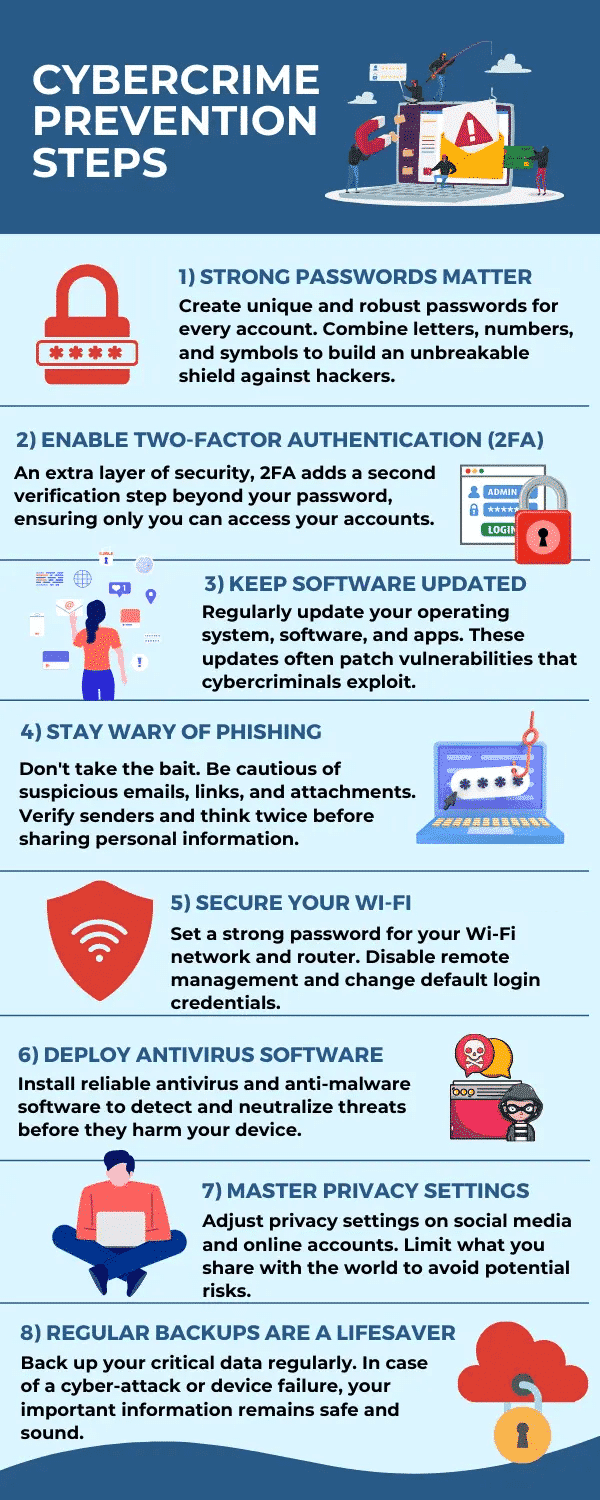
Types of Cyber Criminals
Cybercrime is perpetrated by various types of offenders, each with distinct motivations and methods. Here are five key categories of cyber criminals:
Hackers
These individuals use their technical skills to gain unauthorized access to computer systems or networks. Hackers may be driven by financial gain, political motives, social causes, or simply the challenge of breaking into secure systems.
Insiders
Insiders are individuals who have legitimate access to an organization’s systems or networks but misuse this access for personal gain or to harm the organization. They can be employees, contractors, or other trusted personnel.
Organized Crime Groups
These are sophisticated groups that engage in cybercrime for financial gain or other illegal activities. They often employ advanced techniques to avoid detection and cover their tracks.
Nation-States
Government or state-sponsored groups conduct cyber-attacks for political, military, or espionage purposes. These attacks can involve gathering intelligence, disrupting critical infrastructure, or gaining a strategic advantage over other nations.
Cyberterrorists
Cyberterrorists use digital attacks to create fear, disrupt systems, or cause harm to individuals or organizations. Their motivations can be political, ideological, or social, and they often target critical infrastructure and services.
Each type of cyber criminal poses unique threats. Organizations must take proactive steps to protect against these threats, including implementing robust security measures, conducting regular audits, and staying informed about the latest cybercrime trends and threats. By doing so, they can reduce the risk of cyber attacks and safeguard their sensitive information and systems.
Techniques for Investigating Cybercrime
Investigating cybercrime requires a sophisticated array of techniques and tools to gather and analyze digital evidence. The key components of cybercrime investigation include:
Digital Forensics
This field involves the systematic collection, preservation, and analysis of digital data that can be used as evidence in legal proceedings. It is crucial for identifying breaches, tracing cybercriminal activities, and supporting the prosecution of offenders.
Malware Analysis
Investigators track and analyze malicious software to understand its behavior, origin, and impact. This process is essential for uncovering the methods used by cybercriminals to infiltrate systems and compromise data.
Financial Transaction Analysis
By scrutinizing financial records, investigators can identify suspicious transactions and trace the flow of illicit funds. This technique is particularly useful in cases involving fraud and money laundering.
To enhance these investigative processes, advanced platforms like Knowlesys provide comprehensive tools for tracking digital footprints and analyzing complex datasets, offering significant support for cybercrime investigations.
Each of these methods plays an integral role in piecing together the digital footprint left by cybercriminals.
The Role of Digital Forensics
Digital forensics is akin to forensic science in the physical world; it involves the meticulous analysis of electronic data to uncover evidence of criminal activity. This process includes:
Identification
Recognizing potential sources of digital evidence, such as computers, mobile devices, and network logs.
Preservation
Ensuring that digital evidence is not altered or destroyed. This involves creating exact copies of storage media and securing the original devices.
Analysis
Employing forensic methodologies to examine the data. This can include imaging drives, reconstructing deleted files, and analyzing network traffic.
Documentation
Keeping detailed records of the evidence and the analysis process, which can be presented in court to support legal proceedings.
Digital evidence can include emails, documents, images, transaction records, and internet browsing history. Proper handling and analysis of this data are critical for maintaining the integrity and admissibility of the evidence in legal contexts.
Cybercrime Investigations for Law Enforcement Officers
Cybercrime investigations involve identifying, tracking, and analyzing digital evidence related to various online offenses. Effective investigation requires understanding the crime, identifying potential evidence, and securing necessary court orders.
Assessing the Situation
First, officers must determine the elements of the crime and applicable laws. Consulting with prosecutors can provide additional insights, especially given the evolving nature of technology and global internet jurisdiction.
Conducting the Initial Investigation
Officers should apply traditional investigative methods, asking key questions about suspects, crimes committed, jurisdiction, and evidence. Identifying and preserving both physical and digital evidence is crucial.
Identifying Possible Evidence
Digital evidence can vary in type and size, potentially being encrypted or hidden. Partnering with agencies with specialized resources may be necessary for proper identification and collection.
Securing Devices and Court Orders
Electronic devices often require warrants for searches. Warrants and subpoenas should clearly outline the scope of the search, and non-disclosure agreements might be necessary when requesting information from electronic service providers.
Analyzing Results with Prosecutors
Collaborating with prosecutors helps identify appropriate charges and determine additional evidence needed for prosecution.
Conclusion
As cyber threats continue to evolve, so must the techniques and tools used in cybercrime investigations. The complex nature of cybercrime demands a thorough understanding of digital evidence, meticulous investigative procedures, and close collaboration with legal professionals. By staying informed about the latest developments and employing advanced methods, investigators can effectively combat cybercriminals and protect sensitive information. Proactive measures and continuous learning are essential for maintaining digital security and ensuring justice in the ever-changing landscape of cyber threats.