OSINT for Lawful Interception
What is Lawful intercept?
Lawful intercept is a framework between countries Law enforcement and mobile carriers that is used to tap into telecom subscribers payload, it can be SMS, voice or Data records. It is important sometimes to listen to call records and communication traces of few suspects since it’s a matter of national security.
So there should be framework and protocol in place between law agency and mobile operator so make this happen, ETSI sets standards for this just like for any other network element, using this standard mean LI system from any vendor should work with any operator in the country and provide the accurate information without the knowledge of the tracking party.
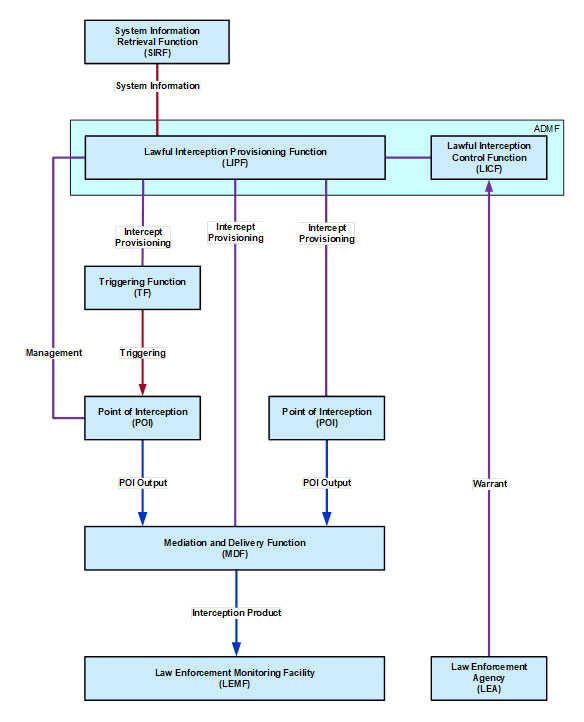
History of Lawful Interception
A couple of decades ago, switched networks were all we had, so interception had to be done on site, directly connecting some cables to the lines that were object to the wiretapping. Either at the objective’s end, or at the switching board/central. But since all communication have gone digital and “fly around” the cables in the form of digital packets of information, the way calls or other types of communications are intercepted has changed substantially. Now, just knowing the endpoints (mostly IPs) of the call, it is relatively easy to intercept the corresponding packets and reconstruct what both parties are saying through the gateway the operator provides. In Europe, implementing the means for lawful interception is required by the European Council Resolution from 1995 which allows for lawful interception systems to prevent crime, including fraud and terrorism.
Most countries have laws in place so that their telecommunications companies have to have the possibility to wiretap individual citizen, as long as there is a court order or some other legal document authorizing the operation. For this, the telecommunication operators provide gateways that have been standardized by different organizations as, for example, ETSI (European Telecommunications Standards Institute). And this means that equipment manufacturers are also involved in this.
Why Lawful Interception?
Lawful interception is a very important tool for law enforcement agencies (LEAs) and other government agencies all over the world for investigating and prosecuting criminal activities and terrorist operations.
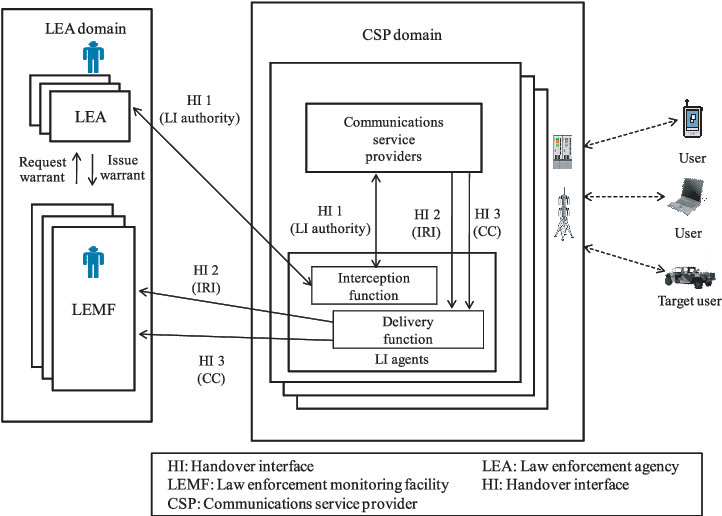
As we have already mentioned, there is a certain amount of standardization promoted by ETSI, in order to allow different countries to use compatible technologies and gateways, in case it is necessary for international operations. Besides LI, there is also LD (lawful disclosure). This means that not all the data that has been gathered may be used. Or, even more complicated, transmitted to another country. For this to happen, both countries must have a prior agreement signed for cross-border data exchange in criminal matters. Finally, there is the concept of RD (retained data) which defines what data can be stored and for how long. As you can see, LI is a heavily regulated affair in order to provide a secure framework to not allow an illegitimate use of the interception facilities or gateways.
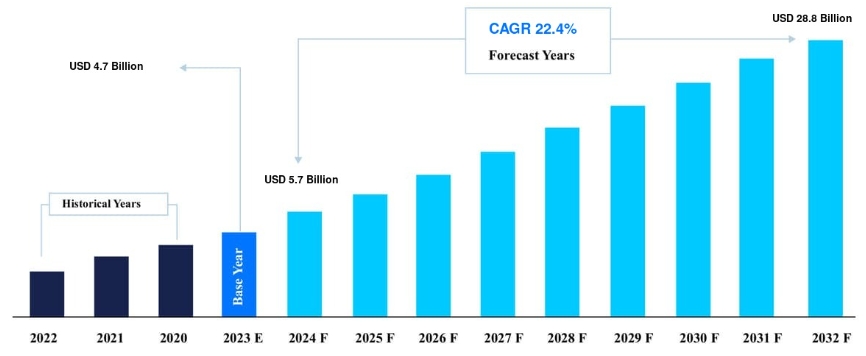
Lawful Interception Market Overview
The global lawful interception market size was valued at USD 4.7 billion in 2023 and is projected to reach USD 28.8 billion by 2032, growing at a CAGR of 22.4% during the forecast period (2024- 2032). Factors such as the rising number of criminal activities and a significant increase in interception warrants are driving the lawful interception market growth.
Lawful Interception Market Drivers
Rising Number of Criminal Activities
The rise in the number of criminal and terrorist activities across the globe has fostered the need for technologically advanced crime detection methods and favorable lawful interception regulations. Lawful interception is used by law enforcement and intelligence agencies to analyze the communication data of suspects to fight and control crimes, such as terrorism, domestic crimes, and cybercrimes. On issuance of a warrant by the legal body, the network operators and service providers relay the intercepted data of the suspect to intelligence agencies and LEAs. The monitoring centers analyze the forensic telecommunication data from SPs and ISPs to derive general intelligence for law enforcement agencies about the suspect's organizations, activities, and associations to track and monitor criminal activities. Such factors drive market growth.
Significant Increase in Interception Warrants
There has been a significant increase in the number of warrants issued for executing lawful interception in the past two decades. The number of warrants issued for lawful interception has drastically increased in countries like Germany. Moreover, certain changes in the communication pattern have led to an increase in the number of interceptions carried out on mobile connections. In addition, the rapid increase in mobile/smartphone users has resulted in the exploitation of communication networks, which has been the prime reason for the increase in the number of interceptions carried out on telecom networks. The number of warrants issued for lawful interception is estimated to increase owing to the current scenario and recent technological changes.
Encryption
Obviously, as in all technology races, the “bad guys” also learn and try to keep their activities hidden from the authorities. But even without considering malicious or criminal actors, data privacy concerns have moved more and more communications systems to end-to-end encryption. And this leaves Law Enforcement Agencies in the dark as to what the contents of a certain communication are. However, there are ways of circumventing this. First of all is the technical information about the parties communicating, as well as the metadata that the information stream carries, which can also give many clues about the involved parties.
And, finally, there are certain techniques that Law Enforcement can use to get to the messages or voice communications, using one or several workarounds. These are, obviously secret, but in some reports there is talk about that around 100% of communications can be “opened” successfully, to know the contents, despite using encryption. The adoption of 5G in the near future will complicate things further, as this technology has security integrated by design. So LEAs will have to overcome the hurdles in order to keep up their work in an efficient way.
OSINT Tools for Lawful Interception
Lawful interception is crucial for law enforcement agencies (LEAs) to legally monitor and analyze digital communications. As online activities increasingly move toward encrypted platforms, specialized OSINT tools become essential for accessing and interpreting relevant data.
Knowlesys Intelligence System
A leading solution for lawful interception, Knowlesys helps link real-world identities to social media profiles, mobile apps, and deep/dark web activity. Its ability to decrypt and analyze encrypted communications makes it indispensable for LEAs.
Hunchly
Hunchly is an evidence-capturing tool for investigators, automatically archiving web pages, including hidden or encrypted information. It ensures accurate and tamper-proof records of online activities, allowing LEAs to follow digital trails while preserving vital evidence for legal proceedings.
Maltego
A data-mapping tool, Maltego specializes in link analysis. It visualizes relationships between different types of data, from IP addresses to social media accounts. Maltego allows LEAs to efficiently track communication patterns, detect associations, and uncover critical information concealed within encrypted networks or fragmented digital trails.
Shodan
Known as the "search engine for hackers," Shodan allows LEAs to search for internet-connected devices, which can be critical in cyber investigations. It scans open ports, services, and device metadata, helping uncover vulnerabilities and identify devices tied to criminal activities.
These tools provide robust support to lawful interception efforts, enabling investigators to operate effectively within legal boundaries while countering encryption challenges. By automating the collection of complex digital data and analyzing encrypted or obfuscated communications, OSINT tools have become vital for modern LEAs to protect national security, investigate cybercrime, and combat organized crime across online platforms.
Future Trends and Innovations in Lawful Interception
The future of lawful interception is characterized by innovation and adaptation, particularly with advancements in technology such as AI and machine learning. These technologies incorporate deep learning algorithms, natural language processing, and predictive analytics, poised to become indispensable tools in the interception toolkit. Their implementation holds the promise of enhancing the accuracy and efficiency of interception operations while ensuring greater respect for privacy and civil liberties. Furthermore, numerous future trends and innovations are emerging in lawful interception, particularly with the integration of AI and machine learning. Below are some of the most highlighted ones:
Real-time Analysis
AI systems will analyze intercepted communications as they occur, using algorithms to identify suspicious content or keywords instantly. This enables swift responses to emerging threats.
Predictive Analytics
Machine learning models will forecast patterns of criminal behavior based on intercepted data, aiding in proactive crime prevention by staying ahead of evolving threats.
Anomaly Detection
AI algorithms will detect deviations from standard communication patterns within vast datasets, signaling potential security breaches or illicit activities. These systems improve over time by learning from data.
Enhanced Privacy Protections
AI techniques such as differential privacy will anonymize intercepted data, allowing for meaningful analysis while safeguarding individuals' privacy rights.
Automated Reporting and Compliance
AI systems will automate the generation of interception reports and ensure compliance with legal requirements, reducing the burden on human operators and minimizing the risk of oversight or error.