OSINT for Counterterrorism
Open Source Intelligence (OSINT) plays a critical role in counterterrorism by providing intelligence agencies and security professionals with the tools to collect, analyze, and interpret vast amounts of publicly available data. This data can be vital in identifying and neutralizing potential terrorist threats, tracking terrorist networks, and understanding the motivations and tactics of terrorist organizations.

Case Studies in OSINT for Counterterrorism
OSINT has been around for many years and has been used by the military, specifically in Iraq. Taxi drivers in the city of Baghdad were known for picking up gossip and news as they drove passengers around the city. As U.S. security forces in the region were trying to maintain control of the city that was split between militias and terrorist groups, they would take advantage of taxi gossip in order to paint a picture of what was going on around the city. The more tech-savvy version of OSINT we see today was first seen during the Arab Spring and Syrian Civil War. The videos of protests that broke out around the Arab world in the early 2010s, were circulated online, which allowed people from every corner of the world to see what was going on during these uprisings. The large flow of information would carry on to the civil wars that would break out, specifically in Syria.
OSINT (Open Source Intelligence) plays a crucial role in counterterrorism, but it comes with several challenges
1. Data Overload: The sheer volume of data available from open sources can be overwhelming, making it difficult to identify relevant information quickly.
2. Data Accuracy and Reliability: Ensuring the accuracy and reliability of the data is critical. Misinformation or disinformation can lead to incorrect assessments and actions.
3. Language Barriers: Terrorist activities often span multiple countries and languages. OSINT tools must be capable of processing and understanding various languages and dialects .4. Timeliness: The speed at which data is collected and analyzed is crucial in counterterrorism. Delays can result in missed opportunities to prevent attacks.
5. Source Verification: Verifying the authenticity and credibility of sources is challenging, especially with the prevalence of fake news and propaganda.
6. Legal and Ethical Issues: There are significant legal and ethical considerations when collecting and using open-source data, particularly regarding privacy and surveillance.
7. Technological Adaptation: Terrorist groups often use sophisticated technologies and methods to evade detection. OSINT practitioners must continuously adapt to these evolving tactics.
8. Integration with Other Intelligence: OSINT must be effectively integrated with other intelligence sources (HUMINT, SIGINT, etc.) to provide a comprehensive picture.
These challenges require a combination of advanced tools, skilled analysts, and robust legal frameworks to effectively manage OSINT operations in counterterrorism. KIS(Knowlesys Intelligence System) can assist the government clients in addressing all these challenges effectively.
Scenarios of OSINT in Counterterrorism
OSINT is employed in various counterterrorism scenarios to prevent, mitigate, and
respond to terrorist threats. For example, during the planning phase of a
terrorist attack, intelligence agencies can monitor online forums, social media
platforms, and communication channels to identify and track potential threats.
OSINT tools enable the collection of crucial data, such as discussions around
specific targets, the procurement of weapons, or the coordination of terrorist
cells.
In another scenario, OSINT can be used post-attack to gather
intelligence on the perpetrators, their networks, and any subsequent threats. By
analyzing online communications and social media activity, agencies can identify
accomplices, disrupt follow-up attacks, and apprehend those responsible.
Additionally, OSINT can be employed in long-term strategies to monitor and
counter the spread of extremist ideologies, which often serve as the foundation
for terrorist activities.
Process in OSINT for Counterterrorism
The OSINT process in counterterrorism involves several steps:
Collection: Intelligence agencies first gather data
from various public sources, such as social media, forums, news outlets, and
databases. Tools like Knowlesys
Intelligence System and OSINT
Framework are used in this phase.
Analysis: Once data is collected, it is analyzed to
identify patterns, connections, and potential threats. Tools like Maltego help
visualize the relationships between data points.
Verification: The collected intelligence must be
verified for accuracy. This step often involves cross-referencing different data
sources to ensure the reliability of the information.
Action: Once verified, intelligence is shared with the
appropriate authorities to take preventive or responsive action, such as
disrupting terrorist activities, arresting suspects, or enhancing security
measures.
Theories that underpin OSINT in counterterrorism often focus on
information dominance and network analysis. By controlling and interpreting
large volumes of open-source data, intelligence agencies gain the upper hand in
identifying and neutralizing terror threats.
Benefits of OSINT in Counterterrorism
Terrorism can be defined as “the unlawful use of violence and intimidation, especially against citizens, in the pursuit of political aims”. Terrorism is a persistent issue throughout the world and as a country, we are constantly searching for tools to help us combat terrorism. Open Source Intelligence (OSINT) proves to assist in the process of collection, linguistic translation, and analysis of data. It was found that 80% of the information that proved to be crucial was publicly available and found on the internet. Social media is a way for terrorist groups to spread their ideology and recruit new members. It was found that from 2011 to 2016 56.27% of radicalization was done through social media as compared to 25% from 2005 to 2011.
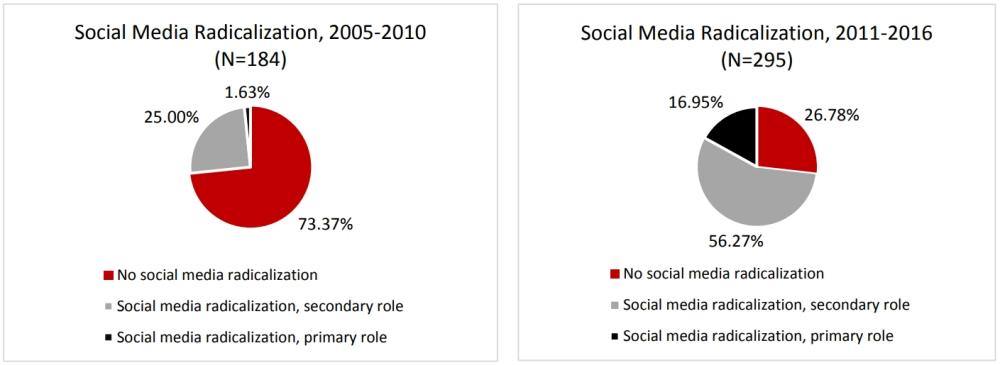
OSINT has become a helpful tool when combating terrorism, OSINT helps investigators create an accurate picture of a terrorist organization. It uses the collection of online databases, local and national newspapers, magazines, and journals. It has been found that internet sites tend to provide the most revealing information about terrorist groups. These sites normally contain propaganda and information on terrorist operations. Oftentimes, terrorists might try and recruit by using social media. Platforms, such as Twitter, often ban these profiles which leads the subject to cyclically create accounts.
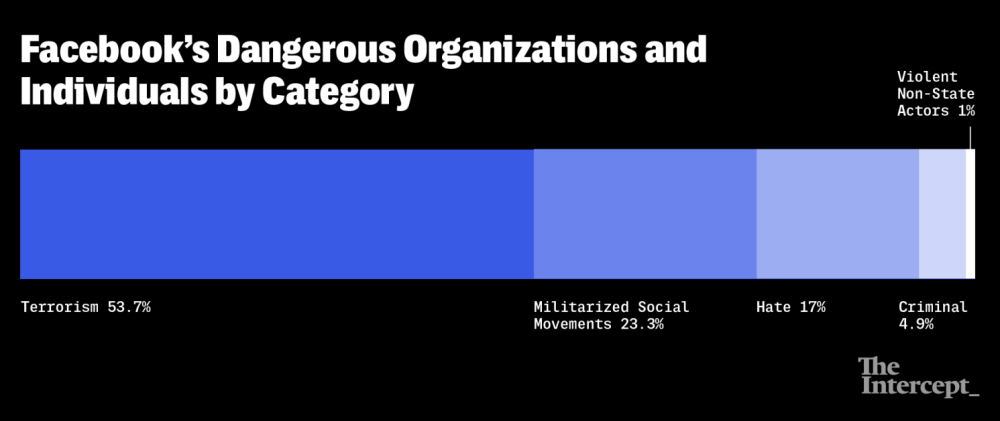
OSINT is used by local and national Law Enforcement Agencies (LEA) and helps confirm and corroborate information that has been found. Due to the vast amount of information that agencies receive on a daily basis, analysis of OSINT is helpful to determine what information is valid. As we know OSINT is special in the sense that the intelligence is collected from publicly available open sources. These open sources are not under the command or control of any government; instead they are sources that are available to the public. While there are many types of other intelligence sources, OSINT is known for being the most accessible. With that being said, the information that is gathered must be further confirmed.
Social Media Resources for OSINT in Counterterrorism
Facebook
Facebook is a hub for community-driven intelligence and can reveal
extremist content through group monitoring. By tracking certain groups or pages,
analysts can identify radicalized individuals or terrorist propaganda.
YouTube
Extremists often post videos to recruit members or share propaganda.
OSINT tools can be used to monitor YouTube channels or videos linked to
terrorist activities.
Twitter
Twitter is often used for real-time communication by terrorist
organizations. Monitoring hashtags and conversations can provide early warnings
of potential attacks or extremist gatherings.
Websites for OSINT in Counterterrorism
Site
Intelligence Group
A private intelligence firm specializing in tracking terrorist
activities online, SITE provides detailed reports on jihadist propaganda,
recruitment efforts, and terror cells.
IntelTechniques
A comprehensive OSINT platform that offers search tools and techniques
for counterterrorism research. Its database includes social media lookup
features and deep web search capabilities.
Cryptome
Cryptome is a repository of leaked intelligence documents and serves as
a valuable resource for understanding the strategies and operations of terror
groups.
UNOCT/UNCCT and INTERPOL launched the CT TECH initiative
In 2022, UNOCT/UNCCT and INTERPOL launched the CT TECH initiative, aimed at
strengthening capacities of law enforcement and criminal justice authorities in
selected partner countries to counter the exploitation of new and emerging
technologies for terrorist purposes, as well as supporting Member States in
leveraging new and emerging technologies in the fight against terrorism. CT TECH
is funded by the European Union and implemented under the UNCCT Global
Counter-Terrorism Programme on Cybersecurity and New Technologies.
The Office also provides expertise in international fora on the use of
unmanned aerial systems (UAS) and delivers capacity-building assistance in
Open-Source Intelligence (OSINT), darkweb, cryptocurrencies, and digital
forensic investigations.
Past UNOCT projects have focused on the use of social media to gather
open source information and digital evidence to counter terrorism and violent
extremism while respecting human rights.
Conclusion
OSINT plays a pivotal role in modern counterterrorism efforts, offering intelligence agencies the ability to gather, analyze, and act on publicly available data. By leveraging a combination of free and paid tools, agencies can effectively monitor and disrupt terrorist activities across digital and physical domains.