How to Build a Robust Cyber Threat Intelligence Framework?

A Cyber Threat Intelligence (CTI) Framework is an essential component of modern cybersecurity strategies. It encompasses a set of processes, tools, and practices designed to collect, analyze, and respond to information regarding potential cyber threats. This proactive approach aims to identify and mitigate risks before they can inflict damage.
Cyber threat intelligence frameworks represent a strategic methodology, equipping organizations with vital insights to recognize and combat emerging cyber threats. These frameworks are continuously evolving, leveraging advanced technologies like artificial intelligence, machine learning, and big data analytics to enhance their effectiveness and adapt to the ever-changing threat landscape.
Core Components of a Cyber Threat Intelligence Framework
A cyber threat intelligence framework is built on three essential components:
Threat Intelligence Collection
This involves gathering data from diverse sources to identify potential cyber threats, including techniques like ITDR (Incident, Threat, and Data Response).
Threat Intelligence Analysis
The collected data is then analyzed to understand the threat landscape and pinpoint potential vulnerabilities within the organization.
Threat Intelligence Dissemination
Finally, the analyzed threat intelligence is translated into a comprehensible format and communicated to relevant stakeholders to inform decision-making and defensive strategies.
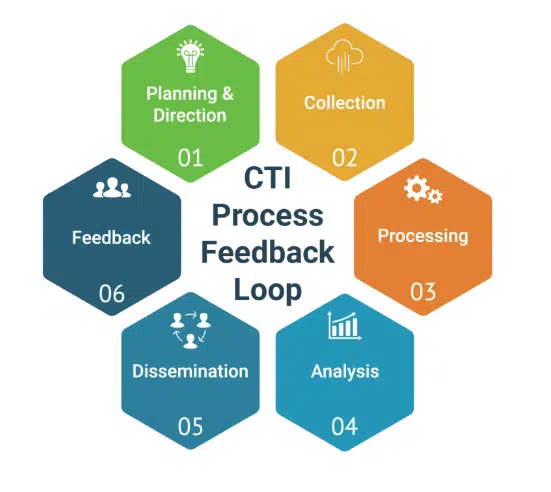
The Evolution of Cyber Threat Intelligence Frameworks
The cyber landscape is continually changing, prompting organizations to adopt robust measures to safeguard their digital assets. Cyber threat intelligence (CTI) frameworks have become essential in this defense, providing critical insights and strategies to preempt and counteract cyber threats.
The Journey of Cyber Threat Intelligence
Initially, cyber security was reactive, addressing threats only after breaches occurred. However, as cyber threats became more sophisticated, a proactive approach was needed. Cyber threat intelligence emerged to identify, understand, and prepare for threats before they could exploit vulnerabilities.
Early cyber threat intelligence frameworks relied heavily on manual analysis and were limited by the availability of data. As technology advanced, these frameworks began to incorporate big data analytics and machine learning, allowing for the automated collection and analysis of vast data sets. This evolution enabled security teams to efficiently identify potential threats amidst large volumes of information.
Modern Advancements in Cyber Threat Intelligence
In recent years, cyber threat intelligence frameworks have been enhanced by advancements in artificial intelligence, predictive analytics, and cloud computing. Modern frameworks can now provide real-time intelligence, detect patterns, and predict future threats, significantly strengthening organizational defenses. For example, AI algorithms can analyze patterns in cyber attack data, offering insights that were previously unattainable through manual methods. Predictive analytics allows organizations to foresee potential threats based on historical data, while cloud computing enables scalable and flexible cyber threat intelligence solutions that can be easily integrated with existing security infrastructure.
Integration and Future Directions
The trend in 2023 focuses on creating cyber threat intelligence frameworks that are more automated, real-time, predictive, and integrated. Integrating cyber threat intelligence with risk management and incident response strategies is crucial, paving the way for a unified and comprehensive cybersecurity approach. This holistic integration ensures that organizations can anticipate threats and respond effectively, minimizing potential damage. Additionally, collaboration between different sectors and sharing of threat intelligence data has become a key strategy, enhancing the collective defense against sophisticated cyber threats. As cyber threat intelligence frameworks continue to evolve, they are increasingly becoming the backbone of a proactive and resilient cybersecurity posture.
The Role of Advanced Technologies in Enhancing Cyber Threat Intelligence Frameworks
In the dynamic world of cybersecurity, advanced technologies play a pivotal role in the enhancement of cyber threat intelligence (CTI) frameworks. Leveraging these technologies is crucial for driving efficiency, precision, and proactive threat mitigation. Here's how some of these technologies are transforming cyber threat intelligence frameworks:
AI and Machine Learning
AI and machine learning have revolutionized threat intelligence. AI automates data collection, parsing through vast quantities of information from diverse sources to identify potential threats. Machine learning algorithms excel at identifying patterns and anomalies within this data, detecting unusual network behaviors, code abnormalities, or specific attack signatures that indicate potential cyber threats. These algorithms continuously learn from past incidents, enabling cyber threat intelligence frameworks to predict and prepare for future attacks.
Machine learning models also provide real-time monitoring, swiftly identifying irregularities and potential threats as they occur. This real-time capability is crucial in dealing with rapidly evolving cyber threats, reducing the time it takes to detect and respond to incidents. Additionally, predictive analysis models can forecast potential threats based on historical data and trends, allowing organizations to proactively strengthen their defenses before an actual threat materializes.
Big Data Analytics
The sheer volume of data generated by digital activities is immense. Big data analytics technology enables cyber threat intelligence frameworks to process this data effectively, providing insightful analyses that can identify subtle patterns and correlations. These insights help organizations anticipate threats and adopt proactive defense strategies.
Cloud Computing
Cloud computing provides the flexibility and scalability needed to manage large datasets and deploy resource-intensive tasks. Cyber threat intelligence frameworks leverage cloud computing to integrate with other cloud-based systems, ensuring a seamless flow of intelligence across various security apparatuses. This integration allows for efficient data management and robust threat intelligence capabilities.
Natural Language Processing (NLP)
NLP enhances cyber threat intelligence frameworks by analyzing unstructured data, such as social media posts or blogs, to extract relevant threat intelligence. NLP can identify potential threats concealed in text data, broadening the scope of threat detection and providing deeper contextual understanding of threats.
Internet of Things (IoT) Security
With the proliferation of IoT devices, which often serve as entry points for cyber threats, cyber threat intelligence frameworks are increasingly incorporating IoT-focused threat intelligence. This integration helps identify and mitigate threats specific to these devices, enhancing overall cybersecurity.
Automation
Automation technology is a core component of modern cyber threat intelligence frameworks. It automates repetitive tasks such as data collection and preliminary analysis, accelerating the threat intelligence process and allowing security teams to focus on strategic decision-making. Automation also aids in refining machine learning models, reducing false positives and ensuring that security teams can concentrate on genuine threats.
By integrating these advanced technologies, cyber threat intelligence frameworks are becoming more sophisticated, efficient, and proactive. This amalgamation of technology and cybersecurity paves the way for a safer and more secure digital ecosystem, empowering organizations to protect their digital assets and stay ahead of emerging threats.
Why Organizations Should Implement a Cyber Threat Intelligence Framework?
A cyber threat intelligence framework integrates technology, processes, and human expertise to gather and analyze threat intelligence. Its main purpose is to proactively identify and counteract cybersecurity threats by consistently interpreting data about potential cyber adversaries and their tactics. This allows organizations to anticipate and mitigate threats before they escalate.
In today's environment, where cyber attacks are becoming more frequent and sophisticated, having such a framework is crucial. Even minor vulnerabilities can lead to significant data breaches, making a proactive stance essential for maintaining security.
Organizations lacking a robust cyber threat intelligence framework often operate reactively, constantly addressing breaches and vulnerabilities after they occur. This reactive approach not only results in immediate financial losses but also damages customer trust and the organization's reputation. The consequences of neglecting proactive threat intelligence can be severe and long-lasting, including financial damage, legal issues, regulatory fines, and potentially even business failure.
Building a Cyber Threat Intelligence Framework
Step 1: Assessing and Identifying Threat Vectors
To effectively build a robust cyber threat intelligence framework, start by cataloging all critical hardware, software, and data within your organization to identify potential vulnerabilities. Next, prioritize these assets and collaborate with security experts to gain a comprehensive understanding of both external threats (such as hackers and malware) and internal threats (like employee negligence or malicious actions). Utilize advanced cybersecurity tools to analyze patterns and trends, recognizing potential attack vectors such as phishing campaigns, malware sites, and insider threats. Set clear, evolving goals with your security teams to ensure continuous protection and preparedness.
Step 2: Collecting Intelligence
To advance your cyber threat intelligence framework, gathering actionable intelligence is crucial. Leverage a combination of open-source intelligence (OSINT) tools, industry feeds, and proprietary platforms to collect comprehensive data. The Knowlesys Intelligence System (KIS) is particularly effective for this purpose, as it excels in collecting extensive and detailed data. By utilizing such robust tools, your InfoSec team can ensure they have up-to-date insights, allowing them to stay ahead of evolving cyber threats and enhance overall security measures.
Step 3: Analyzing Data
Once intelligence has been gathered, analyzing this data becomes crucial. Collaborate closely with fraud teams, who can provide insights into potential financial vulnerabilities and anomalies. Employ advanced analytics tools to sift through the collected data, identifying patterns or unusual activities. The goal at this stage is to transform raw data into actionable insights, ensuring that threats are contextualized and understood in their full scope and impact. This thorough analysis helps in making informed decisions and fortifying security measures.
Step 4: Formulating and Adapting Strategies
With insights in hand, it's crucial to develop a comprehensive security strategy. Effective countermeasures should be established for identified threats, such as enhanced authentication protocols, stricter access controls, and advanced encryption methods. These measures serve as the first line of defense.
However, recognizing that no system is entirely impervious, incident response plans are equally vital. These plans detail the steps to take in the event of a breach, ensuring rapid response and minimal damage. This includes immediate threat neutralization and clear communication protocols to inform stakeholders of any breach.
Adaptability is key in cybersecurity. Given the dynamic nature of cyber threats, a static strategy will not suffice. Regular consultations with security and IT teams are necessary to keep the strategy current and effective against the latest threats. Continuous adaptation based on derived insights ensures that the security measures remain robust and capable of handling evolving threats.
Step 5: Executing and Integrating
Effective execution and integration are crucial components in the development of a robust Cyber Threat Intelligence (CTI) framework. Seamless coordination between security teams, IT departments, and business units is essential to ensure that innovative solutions are effectively integrated and potential vulnerabilities are addressed.
Risk mitigation involves the implementation of security controls and continuous monitoring of network traffic to detect potential threats. Real-time execution of incident response plans is vital to effectively manage and respond to security breaches. Advanced technologies, such as machine learning algorithms and artificial intelligence, play a significant role in detecting and preventing cyber attacks through data analysis. These technologies help identify patterns and anomalies in network traffic, allowing for proactive threat detection and prevention. Additionally, the integration of blockchain technology can secure data and transactions, minimizing the risk of sensitive information theft.
By coordinating efforts across different teams and leveraging advanced technologies, organizations can enhance their cybersecurity strategies, ensuring precise execution and robust protection against evolving threats.
Step 6: Continuously Monitoring and Enhancing
Maintaining an effective Cyber Threat Intelligence (CTI) framework requires continuous monitoring and enhancement. The digital threat landscape is always changing, making it essential for organizations to regularly assess and update their defenses. This involves constant surveillance of network traffic, detailed analysis of gathered intelligence, and vigilant identification of new vulnerabilities. Collaboration across various teams ensures comprehensive coverage.
Using advanced technologies like AI and machine learning aids in detecting and responding to emerging threats. Regular audits, feedback loops, and system checks are vital. By doing so, organizations can ensure their security measures remain robust and adaptive, safeguarding sensitive information from potential cyber attacks.
Conclusion
Implementing a Cyber Threat Intelligence (CTI) Framework is crucial for modern organizations to protect their digital assets. By continuously assessing and identifying threat vectors, collecting intelligence, analyzing data, and formulating adaptable strategies, organizations can preemptively counter cyber threats. Effective execution and integration of these strategies, along with continuous monitoring and enhancement, ensure robust defense mechanisms. Leveraging advanced technologies and fostering seamless coordination across teams further fortifies an organization's cybersecurity posture, safeguarding against the ever-evolving landscape of cyber threats.