Comprehensive Threat Intelligence Solutions for Cybersecurity

In today's cyber landscape, understanding and mitigating threats requires more than just basic tools; it demands a robust threat intelligence solution. Unlike individual tools that focus on specific areas like malware detection or vulnerability scanning, a threat intelligence solution offers a comprehensive system designed to gather, analyze, and disseminate information about potential cyber threats. This holistic approach ensures organizations can anticipate and respond to threats effectively, enhancing their overall cybersecurity posture.
What is a Threat Intelligence Solution?
A threat intelligence solution is a comprehensive system designed to gather, analyze, and disseminate information about potential cyber threats. Unlike individual tools that may focus on specific aspects such as malware detection or vulnerability scanning, a threat intelligence solution integrates multiple functionalities to provide a holistic view of the threat landscape. It combines data from various sources, employs advanced analytics to identify patterns, and offers actionable insights for preventing and mitigating cyber threats.
The key difference between a threat intelligence solution and individual tools lies in its integration and scope. While individual tools might excel in specific areas like endpoint protection or network monitoring, a threat intelligence solution brings these capabilities together, ensuring that security teams have a unified platform to track, analyze, and respond to threats. This integrated approach enhances the ability to predict and prevent attacks, supports strategic decision-making, and improves overall cybersecurity posture.
Furthermore, threat intelligence solutions often include features such as automated threat feeds, collaboration platforms for information sharing, and comprehensive reporting capabilities. These solutions are designed to adapt to the evolving threat environment, continuously updating and refining their databases to provide the most current and relevant threat information. This adaptability and breadth of coverage make threat intelligence solutions essential for modern cybersecurity strategies.
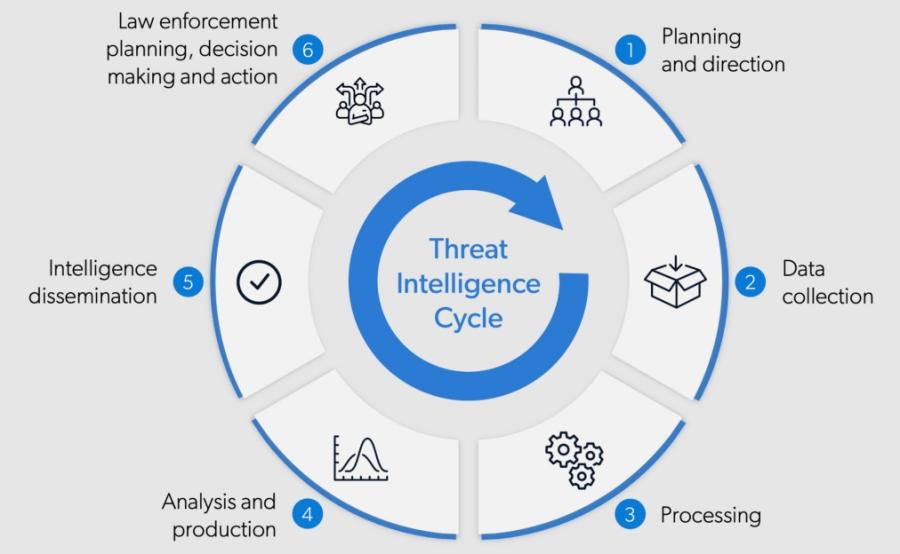
Components of Threat Intelligence Solutions
A comprehensive threat intelligence solution consists of several key components that work together to provide a holistic view of the cyber threat landscape. These components include data collection, analysis, reporting, and response.
Data Collection
Data collection is the foundational component of any threat intelligence solution. It involves gathering information from a wide array of sources such as open-source intelligence (OSINT), social media, dark web forums, and threat feeds. This data can include indicators of compromise (IOCs), vulnerability information, and details about threat actors and their tactics, techniques, and procedures (TTPs). Effective data collection ensures that the intelligence is up-to-date and relevant to the organization's specific threat environment.
Analysis
Once data is collected, it must be analyzed to extract meaningful insights. This involves using advanced analytics, machine learning, and artificial intelligence to identify patterns, correlations, and anomalies within the data. The analysis component helps to classify and prioritize threats based on their potential impact, allowing security teams to focus on the most critical issues. By transforming raw data into actionable intelligence, this component enables proactive threat detection and prevention.
Reporting
Reporting is essential for communicating the findings of the threat analysis to key stakeholders within the organization. This component includes generating detailed reports, dashboards, and visualizations that summarize the threat landscape, highlight emerging threats, and provide recommendations for mitigation. Effective reporting ensures that the information is accessible and understandable to both technical and non-technical audiences, facilitating informed decision-making at all levels.
Response
The response component involves implementing measures to mitigate or neutralize identified threats. This can include automated actions such as blocking malicious IP addresses, updating firewall rules, or deploying patches for known vulnerabilities. Additionally, it encompasses incident response plans and procedures that guide the organization's actions in the event of a cyber attack. By integrating response capabilities, threat intelligence solutions enable organizations to quickly and effectively address threats, minimizing their impact on operations.
Popular Threat Intelligence Solutions
Cyware Threat Intelligence Platform
Cyware's Threat Intelligence Platform (TIP) emphasizes the automation of the entire cyber threat intelligence lifecycle, enabling immediate threat analysis and proactive responses. This platform collects multi-format threat intelligence from various internal and external sources, including open-source and commercial feeds, and internally-deployed response tools. It enriches and analyzes threat data for long-term storage, allowing for predictive scrutiny and providing additional context and severity assessments.
Cyware's TIP standardizes threat data for streamlined analysis and integrates it in real-time with security technologies like SIEM, EDR, MDR, and vulnerability management. This integration facilitates automated actions such as updating allowlists, blocklists, and threat blocking based on predefined rules. The platform also supports information sharing both internally and externally.
Additionally, Cyware offers customizable threat intelligence dashboards that help security teams track and manage the flow of threat data within their organization, improving security outcomes and defense processes. This centralized, automated, and dynamic platform is ideal for sharing tactical and technical intelligence from multiple sources, enabling real-time threat action based on high-confidence data.
IBM Security X-Force
IBM Security X-Force offers a comprehensive suite of offensive and defensive cybersecurity services provided by a team of expert researchers, analysts, hackers, and responders. Their offerings include threat intelligence services, incident response, offensive security, cyber range training, adversary simulation, and vulnerability management services, aimed at helping organizations prevent, detect, respond to, and recover from cyber incidents.
The IBM Security X-Force Exchange and Threat Intelligence Insights features collect global threat intelligence, including early warning indicators, malware activity, and threat group data. This intelligence is shared with organizations to inform their security decisions. Additionally, IBM X-Force provides strategic threat assessments to identify potential attackers, and conducts reverse engineering of malware and other threats from various web layers to pinpoint threat actors.
Cisco Talos
Cisco Talos is one of the largest threat intelligence and research groups globally, providing crucial insights into ransomware and emerging vulnerabilities. By leveraging telemetry data, Cisco Talos identifies new threats and powers Cisco's security solutions while sharing intelligence with the broader cybersecurity community.
Their Intel on Demand service offers direct access to the latest threat intelligence and custom research from Talos analysts. Cisco Talos also provides 24/7/365 emergency incident response services, including emergency assistance, planning, playbooks, readiness assessments, and proactive services to strengthen security postures.
Organizations can refine or develop incident response plans with Cisco’s experts through assessments and cyber range training, preparing staff for real-world threats. Cisco products, powered by Talos intelligence, ensure organizations are equipped with the latest threat detection and response techniques. Cisco Talos’ incident response services are recommended for organizations with SOC teams aiming to proactively manage cyber risks.
Knowlesys: Elevating Threat Intelligence
Integrate With Existing Security Tools
However, it is critical to integrate threat intelligence with existing security tools to maximize its effectiveness. Threat intelligence does not work in isolation, but becomes valuable when combined with other security technologies.
Integrating threat intelligence into automated security systems enhances their ability to detect suspicious events and behavior patterns. A common integration is with Security Information and Event Management (SIEM) systems, which allows for proactive alerting, prioritization, and enriched contextual data for alerts to facilitate investigation. Additionally, endpoint security solutions, next-generation firewalls (NGFW), and web application firewalls (WAF) also greatly benefit from threat intelligence data.
Knowlesys: A Superior Solution
While other solutions offer notable features, Knowlesys distinguishes itself with a comprehensive and advanced approach to threat intelligence. Knowlesys provides a comprehensive view of the threat landscape through data collection from diverse sources. Utilizing advanced analytics and machine learning, it predicts threats effectively. With an intuitive interface and seamless integration with existing security tools, Knowlesys enhances overall security measures and reporting capabilities.
Real-World Application
Consider a large financial institution combating sophisticated phishing attacks. Knowlesys not only identifies indicators of compromise but also correlates data from multiple sources to pinpoint the attack's origin and scope. Its machine learning algorithms predict future targets, providing actionable intelligence for both immediate responses and long-term strategies. Customized reports ensure all stakeholders, from IT teams to executives, remain informed, significantly enhancing the organization's security posture and response time.
Conclusion
Selecting the right threat intelligence solution is crucial for modern cybersecurity strategies. Comprehensive systems that integrate data collection, advanced analytics, and seamless integration with existing security tools are essential for effectively managing and mitigating cyber threats. Knowlesys stands out with its sophisticated approach, providing organizations with actionable insights and enhanced security measures. Investing in such a solution ensures a proactive and resilient defense against the ever-evolving cyber threat landscape, keeping your organization protected and well-prepared for future challenges.