Hackers use ChatGPT to hijack Facebook accounts
Threat actors are exploiting the widespread popularity of OpenAI's ChatGPT
since its release late last year to create fake versions of artificial intelligence
chatbots and lure unsuspecting users into installing them.
The Dark
Reading website revealed that at least 2,000 people downloaded the malicious "Quick
access to ChatGPT" Chrome extension from the Google Play app store every day from
March 3 to March 9, 2023. It is believed that a threatening attacker may have used
the malicious extension to compromise thousands of Facebook accounts, including
business accounts.
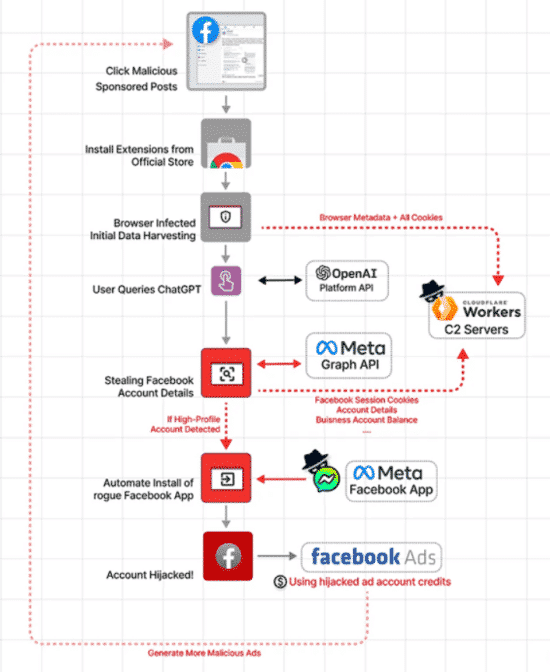
The malicious "Quick access to ChatGPT" Chrome extension
promises users the ability to quickly interact with ChatGPT, the recently mega-hit
artificial intelligence chatbot. In fact, however, the extension surreptitiously
steals cookies from the browser for all authorized active sessions and installs a
backdoor that allows malware operators to easily gain super-administrator access to
a user's Facebook account.
It is worth noting that this extension is just
one of the many ways threat attackers are using ChatGPT to distribute malware and
infiltrate systems.
In recent months, as ChatGPT continues to catch fire,
phishing emails featuring its subject matter have increased dramatically, and more
attackers are using fake ChatGPT apps to distribute Windows and Android malware.
A "Bot Army" targeting Facebook business accounts
The
"Quick access to ChatGPT" extension actually implements quick access to ChatGPT by
connecting to the chatbot's API. But during the access, the extension also collects
a list of all cookies stored in the user's browser, including Google, Twitter and
YouTube, as well as any other activity.
If a user has an active,
authenticated session on Facebook, the malicious extension plugin gives the
developer access to Meta's Graph API. API access allows the extension to obtain all
data related to the user's Facebook account and even take various actions on behalf
of the user.
Even more unfortunately, one component of the malicious
extension's code allows for the hijacking of a user's Facebook account by
registering a malicious application on the user's account and obtaining Facebook's
approval. In response, Guardio said that an application under the Facebook ecosystem
is usually a SaaS service that is approved to use its particular API. Thus, by
registering the application in the user's account, a threat attacker can gain full
administrative access to the victim's Facebook account without having to obtain a
password or attempt to bypass Facebook's dual authentication.
If a malicious
extension encounters a business Facebook account, it quickly obtains all information
associated with that account, including current active promotions, credit balances,
currencies, minimum billing thresholds, and more.
A financially motivated cybercriminal campaign
Before
Facebook can grant access through its Meta Graph API, it must first confirm that the
request is from an authenticated and trusted user. To circumvent this precaution,
the threat actors added code to a malicious browser extension that ensured that all
requests sent from the victim's browser to the Facebook website were modified with
headers so that they also appeared to be trusted. This allowed the extension to
freely browse any Facebook page (including making API calls and actions) using the
infected browser without leaving any traces.
Finally, Guardio evaluated that
threat actors may sell the information they harvest from the campaign to the highest
bidder. Attackers could potentially create an army of bots with hijacked Facebook
business accounts, using money from victims' accounts to post malicious ads.