What You Need to Know About the Dark Web: Access, Risks & Content Overview
The dark web is a hidden part of the internet that isn't indexed by traditional search engines and requires special software to access. Known for its anonymity, it has both legitimate and nefarious uses, offering a unique browsing experience that is shielded from typical internet surveillance. This article explores the distinctions between the deep web and dark web, explains how the dark web works, and highlights the types of threats and content one might encounter in this obscure digital realm.

What is the Dark Web?
The dark web is a segment of the internet that is intentionally hidden and requires special software to access. Unlike the surface web, which is easily searchable via standard search engines like Google, the dark web uses "onion routing" technology to ensure anonymity and protect users from surveillance and tracking. This technology routes user information through multiple encrypted relay points, making it nearly impossible to trace their activities. Originally developed by the United States Department of Defense for secure communication, the dark web is now used for both legal and illegal purposes.
Deep Web vs. Dark Web: What's the Difference?
The terms "deep web" and "dark web" are often confused, but they refer to different parts of the internet.
Deep Web
The deep web encompasses all online content that is not indexed by traditional search engines. This includes anything behind a paywall, requiring login credentials, or intentionally blocked from search engine indexing. Examples of deep web content are:
· Medical records
· Fee-based content
· Membership websites
· Confidential corporate web pages
· Databases
· Social media apps
· Online banking
· Email
· Intranets
· Forums
· Paywall-protected content
In everyday life, whenever you access your email, check your online banking, or use social media, you are interacting with the deep web. It accounts for approximately 96-99% of the total internet content, vastly surpassing the amount of content accessible through standard web browsers, known as the "clear web."
Dark Web
The dark web is a small subset of the deep web that requires specific software, such as the Tor browser, to access. It is intentionally hidden and offers a high degree of anonymity. Although it has a reputation for being a hub for illegal activities, not all content on the dark web is illicit. The dark web's size isn't exactly known, but people estimate it makes up around 5% of the whole internet.
How the Dark Web Works?
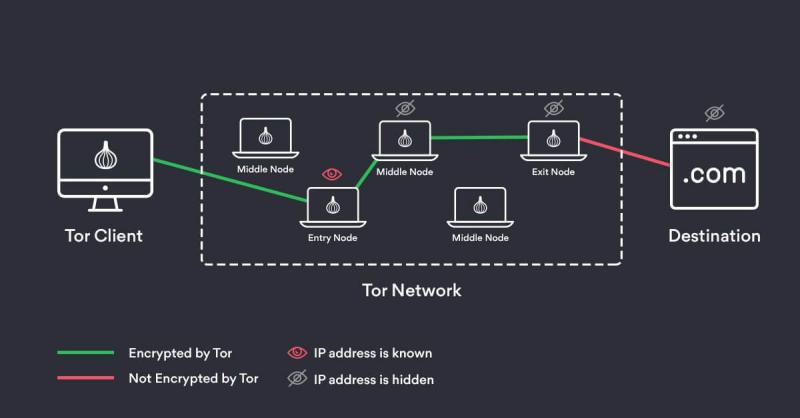
Originally developed by the United States Department of Defense for anonymous communication, the dark web has evolved into a global hub for users seeking privacy. It serves both legal and illegal purposes, employing "onion routing" technology to protect users from surveillance and tracking. This technology, used by the Tor (The Onion Router) browser, routes user data through a complex, random path of encrypted servers. Each time data passes through a relay point, a layer of encryption is removed, making it nearly impossible to trace the original source.
When you connect to the internet, your device is assigned a unique IP address, which can be used to track your online activities. On the dark web, sophisticated methods hide users' real IP addresses, adding another layer of anonymity. Tor's network of nodes ensures that each message bounces from node to node, shedding layers of encryption at each step, until it reaches its destination in a fully decrypted form. This multi-layered encryption process makes tracking the user's activity extremely difficult, if not impossible.
What Can You Find on the Dark Web?
The dark web hosts numerous illegal marketplaces and forums where cybercriminals conduct their activities. These hotspots are rife with various illicit products and services, including:
Personal Data
Full names, home addresses, phone numbers, birth dates, Social Security numbers (SSNs), and hacked email addresses.
Financial Data
Stolen credit card details, online banking usernames and passwords, cryptocurrency account credentials, and banking and insurance records.
Online Account Login Data
Username-password combinations for social media, ride-sharing, video streaming services, professional services, and even genetic testing and antivirus products.
Medical Data
Medical history, prescriptions, biometric data, test results, billing information, and other personal health information (PHI).
Confidential Corporate Data
Classified information such as intellectual property, patents, competitive intelligence, and other sensitive operational details.
Forged Data
Fake passports, stolen driver’s licenses and IDs, bank drafts, and counterfeit money.
Additionally, the dark web offers services like hiring hackers to attack computers, software for breaking into other people's computers, and access to hacked accounts such as Netflix and other subscription services.
Types of Threats on the Dark Web
The dark web, initially created for anonymous communication by the U.S. Department of Defense, is now a hotspot for a variety of threats. While it provides privacy, it can also be a dangerous place to navigate. Here are some common threats you might encounter:
Malicious Software
Malware is rampant on the dark web. It not only provides tools for cyberattacks but also infects unsuspecting users. Common types include:
· Keyloggers
· Botnet malware
· Ransomware
· Phishing malware
Using the dark web exposes you to these threats, making your device and network vulnerable to attacks despite the anonymity offered by tools like Tor.
Government Monitoring
Authorities monitor the dark web, targeting illegal activities. Sites like Silk Road have been seized, and user identities exposed through advanced surveillance software. Simply visiting certain sites can put you under scrutiny, especially in countries with strict internet regulations, like China, where accessing banned content can lead to severe consequences.
Scams and Fraud
The dark web is filled with fraudulent services. Alleged offerings like hitmen services or illegal trafficking often turn out to be scams designed to exploit users financially. Cybercriminals also use stolen personal data for various fraudulent activities, including:
· Financial fraud and identity theft
· Extorting companies and individuals by threatening to leak stolen confidential information
· Making unauthorized transactions with stolen financial information
· Using stolen credentials to access more accounts and sell the data
Infected Devices and Ransomware
Cybercriminals infect devices with malicious software to harvest additional data or extort victims for money. Ransomware, in particular, locks users out of their systems until a ransom is paid.
Operational Disruption
Criminals can disrupt organizational operations, damaging their reputation and causing long-term financial harm. This includes business email compromises and stealing intellectual property to sell to competitors.
How to Access the Dark Web?
Accessing the dark web requires specific steps and precautions due to its decentralized nature and the risks involved. Here's a consolidated guide on how to safely navigate this hidden part of the internet:
1. Set Up a Virtual Private Network (VPN):
Using a VPN is crucial for maintaining your anonymity and securing your connection. A VPN encrypts your internet traffic and masks your IP address, making it difficult for authorities or malicious actors to track your online activities. This is especially important when accessing the dark web, where privacy is paramount.
2. Download and Use the Tor Browser:
The Tor browser is essential for accessing dark web sites, which have a .onion extension. Tor (The Onion Router) anonymizes your browsing by routing your traffic through multiple encrypted nodes, making it nearly impossible to trace. Before launching Tor, ensure your VPN is active for an added layer of security.
3. Utilize a Virtual Machine (VM):
To further protect your main system from potential malware, use virtual machine software such as Oracle VM VirtualBox, Red Hat Virtualization, or Microsoft Hyper-V. A VM creates an isolated environment that minimizes the risk of malware infecting your actual device. For additional security, consider using disposable operating systems that don’t rely on physical storage devices.
4. Finding Dark Web Resources:
The dark web is not indexed by traditional search engines, so you'll need specific links or directories to navigate. Start with resources like the Hidden Wiki or Grams, which provide directories of .onion sites. Be cautious and ensure you're visiting legitimate sites to avoid scams and illegal activities.
Important Precautions:
· Avoid Using Personal Information: Never use your credit or debit cards for purchases on the dark web. Stick to anonymous payment methods.
· Verify Site Legitimacy: Only visit sites that appear trustworthy and legal. The dark web is known for illicit activities, so proceed with caution.
· Be Aware of Government Monitoring: Law enforcement actively monitors the dark web for illegal activities. Merely visiting certain sites can attract unwanted attention.
By following these steps and maintaining a vigilant approach, you can explore the dark web more safely. However, always remember the inherent risks and the importance of staying within legal boundaries.
Conclusion
Navigating the dark web requires caution and awareness due to the inherent risks and potential threats. While it offers anonymity and access to unique content, users must take necessary precautions, such as using a VPN, Tor browser, and virtual machines, to protect their privacy and security. Whether you are exploring for legitimate reasons or just curious, understanding the dark web's landscape and exercising vigilance can help you avoid its many dangers.