The Ultimate Guide to the OSINT Framework
This article will guide you step-by-step to understand and master the OSINT (Open Source Intelligence) framework. First, we will explain the basic concepts of OSINT to set the foundation for your learning. Then, we will take you on an in-depth exploration of the components of the OSINT framework to give you a comprehensive understanding of its operational mechanisms and potential.
After that, we will discuss different types of open source data in detail and show you how to identify and utilize these valuable information resources. We will then look at how to effectively use the OSINT framework and outline the types of information that can be gathered through it.
Finally, we will focus on practical applications of the OSINT framework, revealing how to utilize these tools for various investigative and analytical purposes. With this guide, you will be able to master the core skills of the OSINT framework and enhance your expertise in the field of cybersecurity.
What is OSINT?
Open Source Intelligence (OSINT) encompasses the collection of legally obtainable information from public online sources, providing insights into individuals, businesses, and their internet activities. While the definition of OSINT can include offline resources, the term predominantly refers to online information due to the proliferation of internet users and the wide range of online tools available for various purposes.
The significance of intelligence gathering extends to both ethical penetration testers and malicious threat actors. OSINT involves leveraging websites and software that enable users to extract valuable insights about individuals, organizations, or any online entity. The rise of social media platforms and the abundance of online resources have facilitated global communication and information sharing. Unfortunately, this ease of access also exposes such information to potential misuse.
Although OSINT is accessible to ill-intentioned users, it is equally available to testing teams and IT administrators. Malicious actors may exploit OSINT to gather information and cause harm, but organizations can utilize these tools to gain a comprehensive understanding of their digital footprint, proactively preventing future cybersecurity incidents.
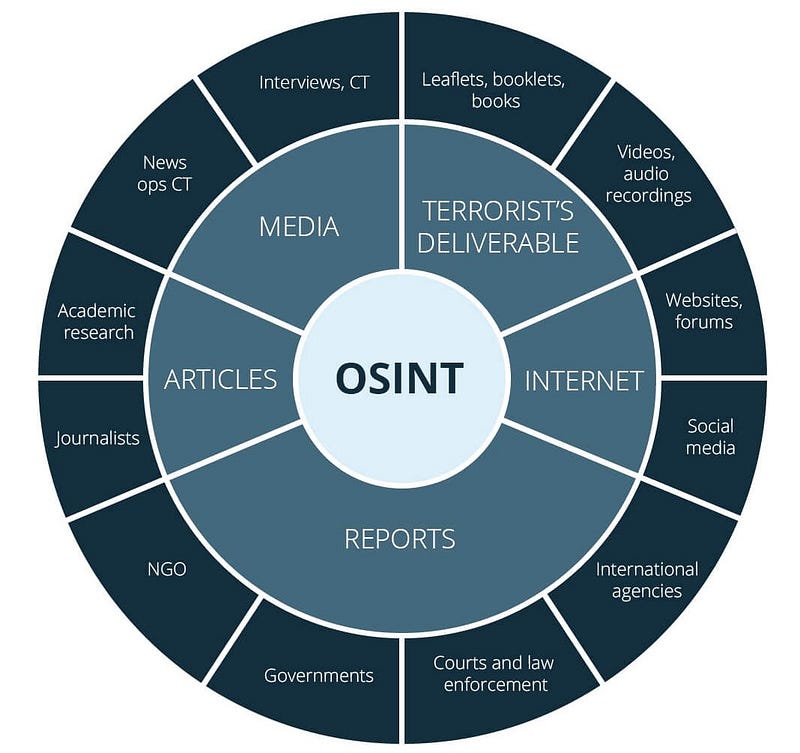
Exploring the OSINT Framework: A Comprehensive Overview
Open source intelligence (OSINT) involves gathering publicly available data from diverse sources, including but not limited to:
News articles
Social media posts
Government reports
Online forums
Other OSINT resources
Originally rooted in military intelligence, OSINT was primarily utilized for espionage and strategic purposes through traditional media channels like newspapers and radio broadcasts.
With the advent of the internet and digital communications, the scope and impact of OSINT have significantly expanded. The OSINT Framework offers a structured approach to perform open-source intelligence tasks, benefiting security researchers, government agencies, and cybersecurity professionals in their information-gathering endeavors.
The OSINT Framework serves as an extensive repository of tools designed to assist businesses in information gathering and cybersecurity investigations. Categorized resources encompass public records, images, archives, the dark web, business records, people searches, and more. Each category presents a wide array of options to fine-tune searches, simplifying the process of locating the desired intelligence source with just a few clicks.
By exploring elements such as usernames, domain names, and email addresses, users gain access to a wealth of information presented in a sub-tree format on their screens. The unified interface ensures a user-friendly experience, enabling effortless searches for relevant details tied to usernames, email addresses, domain names, and other pertinent information. This invaluable repository empowers organizations engaged in OSINT for cybersecurity purposes, facilitating proactive threat detection and mitigation.
Here is OSINT Framework.
The OSINT Framework goes beyond a mere compilation of tools and techniques; it presents a comprehensive and structured approach that serves as a guiding compass for navigating the intricate realm of open-source intelligence. Developed and refined by industry experts, this framework empowers analysts and investigators with a roadmap to optimize their efforts, ensuring no valuable insights remain concealed.
Key Components of the OSINT Framework:
The OSINT Framework consists of essential building blocks that synergistically contribute to the intelligence-gathering process:
1. Information Sources and Domains:
At the foundation of the framework lies a curated collection of diverse information sources and domains. These encompass social media platforms, search engines, websites, and specialized databases, providing analysts with a rich array of starting points for data collection.
2. Techniques and Tools:
The framework encompasses an arsenal of techniques and tools that facilitate efficient and targeted data extraction. From web scraping and social media analysis to geolocation and image recognition, each technique enriches the intelligence-gathering journey.
3. Methodologies and Guidelines:
The OSINT Framework offers established methodologies and guidelines that promote structured analysis. By following these proven approaches, analysts can transform raw data into meaningful insights, enhancing the quality and relevance of the extracted intelligence.
4. Training and Skill Development:
Recognizing the dynamic nature of the digital landscape, the OSINT Framework emphasizes continuous skill development and learning. It provides resources for honing technical proficiency and staying updated with the latest tools and techniques in the field.
The OSINT Framework serves as a structured methodology for performing open-source intelligence tasks, benefiting security researchers, government agencies, and cybersecurity professionals in their information-gathering endeavors. Accessible through its official website, the framework's primary function is to compile publicly available information from various online sources. Users can easily navigate the framework by clicking on relevant categories related to their investigation, such as Username, Email Address, or Domain Name. This grants them access to a plethora of tools tailored to their research needs.
Structured with a systematic approach, the OSINT Framework categorizes gathered information based on its source, relevance, type, and context. By focusing on free tools and resources, the framework empowers users to collect valuable intelligence from the vast realm of publicly available online data. It provides a comprehensive range of tools and techniques for open-source data analysis, enabling analysts to extract actionable insights efficiently.
Classification of the OSINT framework
The OSINT framework provides a systematic classification of resources and tools for open-source intelligence gathering. To access these valuable assets, start by visiting the OSINT framework website. There, you will find a comprehensive list of categories branching off from the main OSINT framework.
By exploring these categories, you can discover a wide range of tools and resources tailored to specific types of intelligence gathering. Whether you need search engines, specialized resources, or practical tools, the OSINT framework serves as your ultimate go-to resource for publicly available information on the internet.
With 22 different categories, the OSINT framework covers a comprehensive range of topics. Each category is represented as a primary node branching out from the central "OSINT Framework" node. Furthermore, within each primary node, you'll find secondary nodes or subcategories that delve into more specific types of information sources or tools.
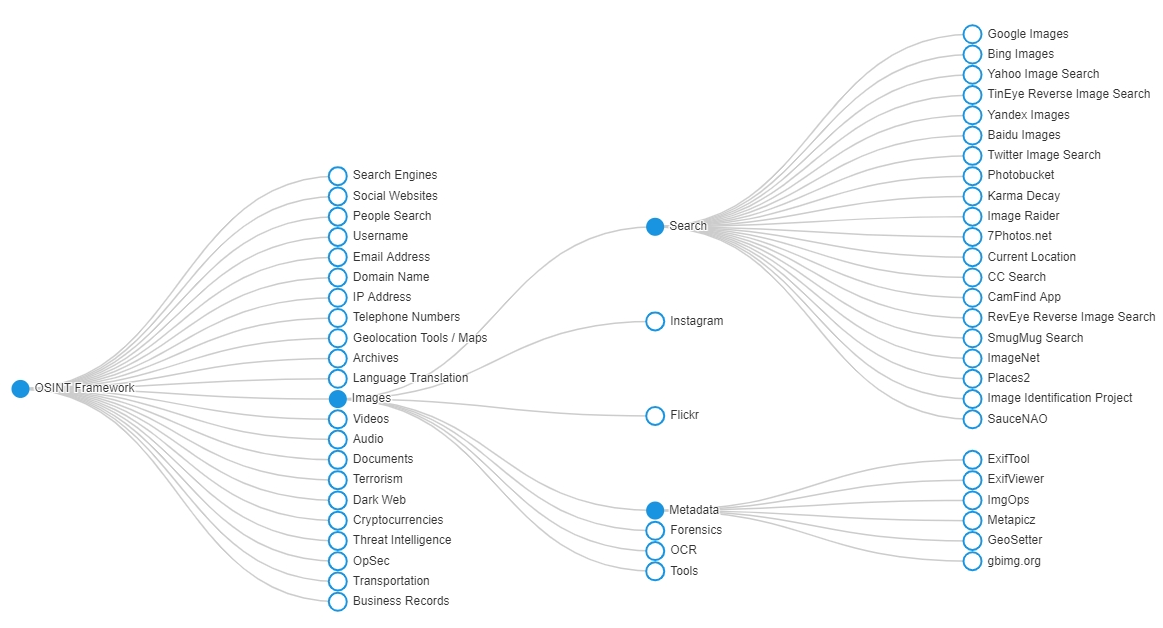
This hierarchical visualization of the OSINT framework ensures a clear and organized view of the various avenues available for obtaining open-source intelligence data. It allows you to start with a broad category and then navigate deeper into more specific areas of interest. This tree-like structure facilitates a direct approach to data collection, enabling you to focus on the most relevant and targeted information.
Each tool will be listed within a “Tool Classification Indicator”:
(T) - Indicates a link to a tool that must be installed and run locally
(D) - Google Dork
(R) - Requires registration
(M) - Indicates a URL that contains the search term, and the URL itself must be edited manually
Different Types of Open Source Data
When it comes to extracting valuable insights from data, knowing where to look is crucial. Open source data encompasses a wide range of forms, with a significant portion already accessible to the public, while the rest can often be obtained through specific requests. Let's explore some of the key types of open-source data commonly utilized in OSINT:
Media reports, newspapers, and magazine articles: These sources offer valuable insights into ongoing events, public sentiment, and emerging trends. For instance, companies can stay informed about security breaches within their industry through these channels.
Academic papers and published research:
These scholarly works provide in-depth knowledge about specific topics, making them invaluable resources for cybersecurity professionals seeking information on new cyberattacks or vulnerabilities.
Social media activity:
The vast landscape of social media platforms can reveal personal information, affiliations, behavior patterns, and even unintentional disclosures of sensitive data. Hackers, for example, may identify potential phishing targets through social media analysis.

Census data:
Demographic details obtained from census data can be utilized in threat modeling or understanding potential target audiences for social engineering attacks. Companies can gain valuable insights into groups likely to be targeted in future attacks.
Telephone directories:
These directories may contain contact information that could be exploited for spear-phishing or other targeted attacks, highlighting the importance of protecting such data.
Court filings and arrest records:
Information found in legal filings and arrest records can provide insights into legal disputes and criminal activities, potentially indicating vulnerabilities or targets.
Public trading data:
This data offers insights into a company's financial health, which can inform motivations behind potential attacks.
Public surveys:
Surveys offer valuable data on trends and public opinion. However, if not properly anonymized, they may inadvertently expose sensitive information.
Location context data:
Information such as geotags can unveil the location of individuals or devices, revealing patterns or valuable details.
Breach or compromise disclosure information:
Organizations can learn from others' mistakes and understand how breaches occur through disclosure information, while attackers may use it to replicate successful attacks.
Publicly shared cyberattack indicators:
IP addresses, domains, and file hashes shared publicly can help organizations identify potential threats and proactively protect their systems.
Certificate or domain registration data:
This data reveals an organization's online assets, enabling the monitoring of potential security issues.
Application or system vulnerability data: Public databases or forums often contain information about known vulnerabilities. Attackers can exploit these weaknesses, while defenders can use them to patch vulnerabilities.
How to use the OSINT framework?
The OSINT framework provides a structured and comprehensive approach to conducting open source intelligence activities. It enables practitioners to gather and analyze a wide range of information from various sources. Here are some key aspects of the OSINT framework and the insights it can uncover:
Establishing the Digital Footprint of a Known Threat:
One of the primary applications of an OSINT framework lies in its ability to discern and analyse the digital footprint of a known threat. By systematically scouring online platforms, forums, and digital repositories, practitioners can compile a comprehensive dossier of the threat's online activities, interactions, and patterns. This detailed analysis serves as a crucial foundation for threat assessment, allowing for the development of targeted and effective countermeasures.
Gathering Comprehensive Intelligence about an Adversary:
In the realm of intelligence gathering, the OSINT framework excels in providing a holistic view of adversaries. It delves deep into their activities, interests, techniques, motivations, and habitual patterns. Through rigorous data collection and analysis, practitioners construct a comprehensive profile, affording invaluable insights into the strategic landscape. This knowledge forms the basis for strategic planning, enabling organisations to anticipate and respond to adversarial actions effectively.
Categorisation for Precision Analysis:
The OSINT framework places significant emphasis on the meticulous categorisation of acquired data. Each piece of information is classified based on its source, relevance, type, and contextual significance. This systematic categorisation streamlines the subsequent analysis process, allowing for the swift retrieval of specific data points. This approach ensures that practitioners can distill meaningful insights from the extensive pool of information amassed.
Identifying Opportunities for Security Enhancement:
Another critical facet of the OSINT framework lies in its ability to identify opportunities for bolstering existing security postures. By scrutinising online activities, discussions, and emerging trends, practitioners can pinpoint potential vulnerabilities and risks. This proactive approach empowers organisations to fortify their defenses and implement preemptive measures, thereby safeguarding assets and interests.
As practitioners engage with the OSINT framework, it is imperative to approach each task with the utmost ethical consideration. Respecting privacy, adhering to legal boundaries, and refraining from any actions that could be perceived as invasive or harmful is paramount. This ethical foundation not only upholds professional standards but also ensures that the pursuit of information remains within the bounds of lawful and morally upright conduct.
In the ever-evolving landscape of open source intelligence, the OSINT framework serves as a beacon of guidance. Its structured methodology, ethical underpinnings, and rich array of tools and techniques equip practitioners with the means to navigate this dynamic terrain effectively. By incorporating the principles and practices outlined in the framework, individuals and organisations alike empower themselves to make informed, strategic decisions based on a solid foundation of intelligence and insights.
Continuous Learning and Adaptation:
In the dynamic field of open source intelligence, continuous learning and adaptation are imperative. The OSINT framework underscores the need for practitioners to stay abreast of the latest tools, techniques, and information sources. This commitment to ongoing education ensures that individuals remain equipped with the most effective resources to navigate the evolving landscape of open source intelligence. By embracing a culture of continuous improvement, practitioners enhance their proficiency and effectiveness in intelligence-gathering endeavors.
Integration into Decision-Making Processes:
The insights derived from OSINT activities play a pivotal role in shaping informed decision-making across various domains. Whether in the realms of cybersecurity, business strategy, risk management, or policy formulation, the wealth of information garnered through OSINT activities provides a valuable foundation. This intelligence empowers decision-makers to make choices grounded in a thorough understanding of the prevailing environment. By integrating OSINT-derived insights into their decision-making processes, organisations optimise their strategic approaches and enhance their overall effectiveness.
Collaborative Intelligence Gathering:
One of the key strengths of the OSINT framework lies in its capacity to facilitate collaborative intelligence gathering efforts. By leveraging a diverse array of sources and tools, practitioners can work together to compile a comprehensive understanding of a given subject or situation. This collaborative approach fosters a synergistic exchange of insights and expertise, resulting in a more holistic and accurate intelligence assessment.
Multi-Disciplinary Approach:
The OSINT framework embraces a multi-disciplinary approach, recognising that intelligence-gathering efforts often require expertise spanning various domains. It encourages practitioners to draw on a range of skills and knowledge areas, including but not limited to information technology, social sciences, cybersecurity, and geopolitics. This broad spectrum of expertise ensures that intelligence assessments are comprehensive and well-rounded, taking into account various facets of a given subject.
Safeguarding Reputations:
In addition to security concerns, the OSINT framework also plays a crucial role in safeguarding reputations. By monitoring online discussions, mentions, and sentiments, practitioners can proactively address potential reputation risks. This proactive approach allows organisations to mitigate negative publicity or misinformation, preserving their brand image and credibility in the digital sphere.
Societal Impact Assessment:
The OSINT framework extends its reach beyond individual organisations and threats, encompassing assessments of broader societal impacts. Practitioners can use OSINT to analyse trends, sentiments, and emerging issues within the public domain. This societal insight can inform policy decisions, crisis management strategies, and public relations efforts, ensuring that organisations are attuned to the pulse of the wider community.
Influence Mapping:
OSINT can be leveraged for influence mapping, a strategic process that involves identifying key individuals, organisations, or entities that wield significant influence within a given context. By analysing their online presence, affiliations, and activities, practitioners can gain valuable insights into the power dynamics at play. This information can be pivotal in devising effective communication and engagement strategies.
Predictive Analytics and Trend Forecasting:
By analysing patterns and trends derived from open source information, the OSINT framework can facilitate predictive analytics and trend forecasting. This forward-looking approach enables organisations to anticipate potential developments and adapt their strategies accordingly. It empowers decision-makers with the foresight needed to stay ahead of emerging challenges or opportunities.
The OSINT Framework offers a comprehensive and structured approach to open source intelligence activities. It encompasses methodologies for data collection, categorisation, and analysis, supported by a diverse array of tools and techniques. Additionally, it emphasises ethical considerations, continuous learning, and the integration of intelligence into decision-making processes. By adhering to the principles outlined in the OSINT Framework, practitioners equip themselves with the knowledge and skills to navigate the complex landscape of open source intelligence effectively and responsibly.

Overview of the information that can be gathered from the OSINT framework:
● Gather person's full names, job roles, phone numbers, photos, etc.
● Various data from search engine information from Google, Bing, Yahoo, and others.
● Data from personal and corporate blogs, as well as evaluating user activity on digital forums.
● Identify various social networks used by the person.
● Evaluate content available on social networks like Facebook, Instagram, WhatsApp, Linkedin, or Twitter.
● Accessing old cached data from Google.
● Recognize mail addresses, mobile phone numbers from social media networks, or Google results.
● Look for photographs & videos on common social photo-sharing sites, like Google Photos, & more.
● Utilize Google Maps and other open satellite imagery sources to retrieve images of users' geographic location.
Conclusion
The OSINT Framework is not only a powerful tool for collecting and analyzing information from open sources in support of a variety of intelligence-gathering missions, but it is also an integral part of the modern cybersecurity landscape. By learning and practicing the OSINT framework, you can better understand the risks and vulnerabilities of your environment and thus make more informed security decisions.
Finally, remember that while OSINT provides a wealth of information and resources, it is important to use this information in an ethical and legal manner. Only by using OSINT legally and responsibly can we ensure that our actions have a positive impact on others and society.
OSINT will continue to evolve and become even more important as technology continues to advance and new data sources become available. We encourage you to stay up-to-date on the latest trends and developments in OSINT and to continually improve your skills and capabilities to better respond to increasingly sophisticated cyber threats.