OSINT for Criminal Investigation
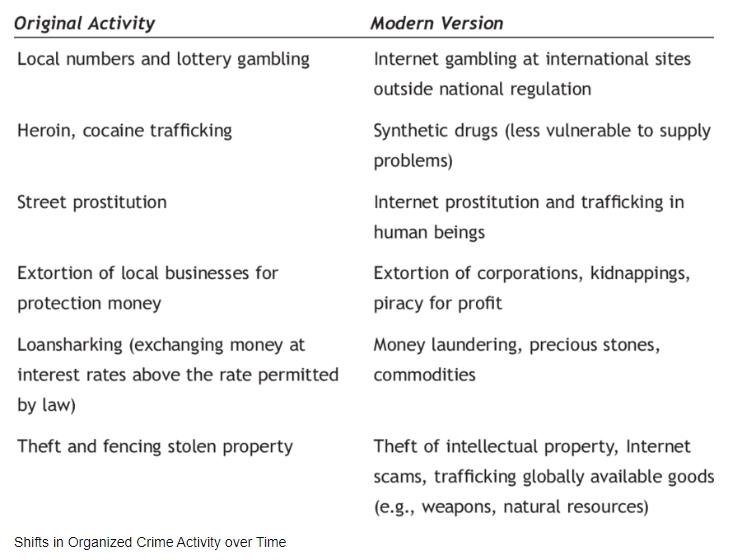
In today's modern age driven by digital innovations, the widespread adoption of technology has transformed criminal activities, leading to the emergence of cybercrime as a significant challenge for law enforcement agencies globally. Cybercrime acts have left a considerable dent on criminal activities and nowadays that we are halfway into the subsequent technological era stands as one of the most crucial issues for law enforcement agencies all around the globe. The aim of this work is to discuss the relationship between cybercrime and organized crime and the importance of OSINT within criminal investigations in supporting law enforcement itself. Particularly, due to the current amount of data available online, law enforcement has access to crucial information concerning important matters in criminal cases, therefore OSINT has offered an advantageous opportunity to law enforcement agencies to investigate criminals.

History of Criminal Investigation
Since the 1900s, innovative developments have revolutionized law enforcement and
forensic science’s ability to tackle the most complex criminal cases. In 1901
fingerprint identification was first accepted as evidence in British courts
following its development throughout the 19th century, bringing more accurate
identification of suspects and the ability to link individuals to crime scenes.
In 1921 John Augustus Larson developed the modern polygraph to measure
physiological responses to determine truthfulness. Forensic pathology emerged in
the 1930s, advancing autopsy techniques to identify the cause and time of death
more accurately, while the 1950s saw improvements in ballistics to link bullets
to specific weapons. By 1984, DNA profiling had come in to play to intrinsically
link criminals to their crimes.
Law enforcement authorities’ attempts to ensure perpetrators are held
responsible for their crimes has seen rapid advancements in the past century,
and it shows no sign of slowing down. Now, with the emergence of digital
technologies gaining momentum throughout the 2000s, police forces around the
world are increasingly looking to utilize the latest and most innovative
technology to ensure justice is delivered. It is an evolution of policing which
investigative technology specialist, Altia, is seeking to lead the charge on.
In an era where information is both abundant and accessible, the role of
open-source intelligence (OSINT) in combating criminal networks has become
indispensable. Holding the ability to collect and analyse publicly available
data, OSINT is inspiring a transformative shift in the way law enforcement
agencies approach crime prevention and investigation, as they look to utilize
comprehensive, real-time insights.
OSINT Criminal Investigation Steps
These are the steps that investigators use to help when investigating a crime
when they are using the OSINT method. This method is still being used today.
Purpose: The primary objective is to detect and respond
to potential cyber threats swiftly by systematically analyzing indicators of
compromise (IoC) and indicators of attack (IoA).
Harvest: A multi-faceted approach is employed to gather relevant
information, including accessing commercial data sources, leveraging insights
from industry-specific Information Sharing and Analysis Centers (ISACs), and
monitoring data streams from social media and other repositories.
Categories: The analysis framework focuses on two main
categories, IoCs and IoAs, which denote specific artifacts or events indicating
system compromise or ongoing attacks, respectively.
Refine: Targeted inquiries are made to refine the
threat assessment, distinguishing between known malware signatures, unauthorized
system modifications (IoCs), and suspicious activities' context (IoAs). This
refined analysis enables prompt and decisive responses to emerging cyber
threats.
Role of OSINT in Criminal Investigations
Expanding the net
OSINT holds a crucial role in dealing with criminal networks. Using
software with a vast reach and ability to capture key information in real-time
empowering investigators to expand their net of operations. Where traditional
intelligence methods relied on covert and classified operations, OSINT allows
authorities to tap into a wide array of sources available to anyone with
internet access, enabling them to build a digital picture of a suspect’s
movements.
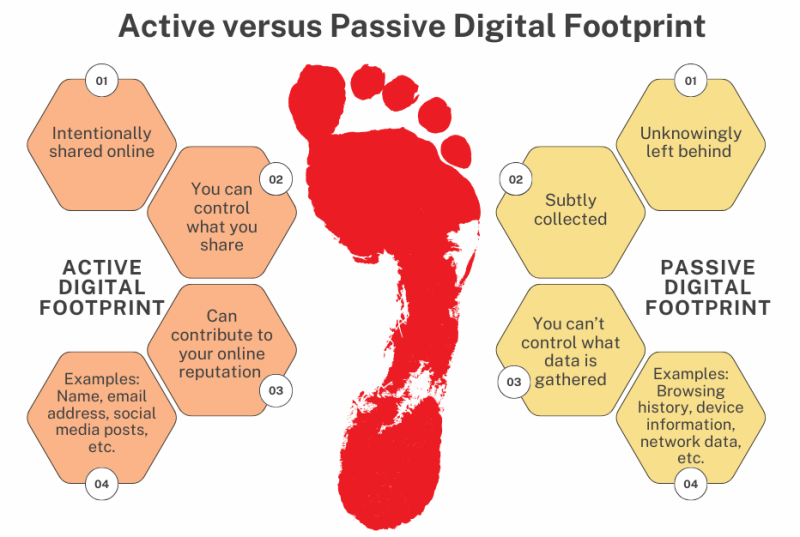
Whether it be on social media platforms, via news reports or online
forums, or even public records, everyone leaves a digital footprint, and where
criminals are concerned, investigators can use these domains to paint an online
picture of their actions. By monitoring these sources, authorities can identify
patterns, track movements, and uncover connections that might otherwise have
remained hidden to the naked eye.
Managing the risks
By leveraging OSINT, police forces can revolutionise how they manage and
respond to criminal risks. By monitoring data, police forces are able to
anticipate, and therefore mitigate, potential threats with unprecedented
precision. As well as helping authorities to identify potential suspects and
understand criminal networks, it also enhances situational awareness.
As a result, authorities can apply a strategic approach to optimize
their resource allocation and bolster public safety. This is further enhanced
with encouraged collaboration and information sharing between different
agencies. As the data is publicly available, and can be shared across regions
and sectors seamlessly, organizations can pool their resources to develop a
coherent, effective approach to tackling criminal investigations.
Speed of information
The speed at which this information can be gathered, analyzed, and
processed adds another weapon to an investigator’s toolbox. In the fast-paced
world of criminal activities, timely information is critical and can often be
the deciding factor in whether a prosecution is successful or not, or even in
ensuring public safety.
OSINT tool brings huge value in this regard, providing police forces
with volumes of organized data. Meanwhile, OSINT tool significantly reduces
costly outputs when they are not necessarily needed. Traditionally, intelligence
operations can be expensive, requiring significant resources for surveillance,
informants, and other covert activities. OSINT, on the other hand, leverages
freely available information, reducing the need for expensive and
resource-intensive operations, making it an attractive option for law
enforcement agencies who are working from a shoestring budget.
Using OSINT (Open Source Intelligence) monitoring system KIS for criminal investigations involves several key steps and techniques
1. Footprinting and Reconnaissance by KIS:
This involves gathering information about the target from publicly available sources. This can include social media profiles, public records, news articles, and other online content .
2. Social Media Monitoring by KIS: Investigators can monitor social media platforms for posts, comments, and interactions that may provide clues or evidence related to the crime.
3. Digital Forensics by KIS: Analyzing digital footprints left by suspects, such as email addresses, IP addresses, and online activities, can help trace their actions and connections.
4. Geospatial Analysis by KIS: Using geospatial data to track movements and identify locations relevant to the investigation. This can include analyzing geotagged photos and posts.
5. Dark Web Monitoring: Specialized tools can be used to monitor the dark web for illicit activities, such as the sale of illegal goods or services, which may be linked to the crime.
6. Data Correlation and Analysis by KIS: Correlating data from various sources to identify patterns, connections, and potential leads. This can involve using advanced analytics and machine learning algorithms.
7. Verification of Information: Ensuring the accuracy and reliability of the information collected by cross-referencing multiple sources and using verification tools.
8. Real-Time Alerts by KIS: Setting up real-time monitoring and alerts for specific keywords or activities related to the investigation, allowing for prompt responses to new developments.
By leveraging these techniques, investigators can gather valuable intelligence, identify suspects, and build a comprehensive case.
Using Social Media in Criminal Investigations
For online investigators, social media sites like Facebook, Snapchat, Instagram
or TikTok could be a treasure trove of information. But just like traditional
detectives, investigators must be extra careful to maintain anonymity and keep
their identity and intent hidden while researching social media. Not only could
a clumsy move spook the bad guys into going deeper undercover, it could also
trigger retaliation (cyber or material), putting law enforcement agents at risk.
There are several specialized tools out there to help online
investigators browse social media sites without risk. They can be a great
addition to investigators’ portfolios when following suspects and persons of
interest on social media platforms.
Remember to use caution while searching social media where you must log
in to view information. Your target may be able to see who viewed their profile,
or you may pop up in recommended connections due to your interaction with their
profile or posts.
Social
Searcher
Social Searcher is a real-time social media monitoring engine. It allows
you to search for users, keywords, and trends across 11 different social media
platforms. It searches for content in social networks in real time and provides
deep analytics data. Users can search without logging in for publicly posted
information on Twitter, Google+, Facebook, YouTube, Instagram, Tumblr, Reddit,
Flickr, Dailymotion, and Vimeo.
Free users can also save their searches and set up email alerts. Premium
features include saving social mentions history, exporting data, API
integration, advanced analytics, and immediate email notifications.
Inflact
Inflact is a multi-purpose service, including an excellent Instagram
search tool. Influencers, bloggers and regular users can choose tools based on
their needs. It offers free and paid services for building a social media
audience, managing content and communicating with clients. And it’s great for
investigators, too!
TikTok
TikTok has taken off in the last couple of years, and while it’s
generally just good fun and a lucrative platform for some folks to make money,
TikTok is also used by criminal organizations as a platform for their
propaganda, drug sales and a way to connect with potential victims. Searching
TikTok is very straightforward: if you're looking for a specific profile, use
TikTok.com/@ and then a username. If you're looking at a particular hashtag,
enter TikTok.com/tag/ and the keywords or phrases you're searching for. Searches
on TikTok don’t require a login.
Telegago
Telegago is another potent OSINT tool that offers comprehensive data
retrieval, advanced search and filtering, social media analysis and alert
notifications, and can be integrated with other tools. Telegago enhances
efficiency by providing a centralized hub for data collection and analysis,
enabling investigators to track individuals and events across online platforms,
make informed decisions and stay updated in real-time.
Telegago can be employed to track and monitor specific Telegram (popular
among criminals) channels and groups. Investigators can use it to collect data
such as posts, comments, media content and user interactions within these
channels.
Advanced search and filtering capabilities enable investigators to
perform precise queries within Telegram, allowing them to narrow down their
focus and quickly locate specific content or users of interest. Telegago’s data
visualization capabilities can help investigators identify patterns and
connections within Telegram communities, aiding in the analysis phase of the
investigation.
Telepathy
Telepathy is a versatile OSINT tool dubbed the “Swiss Army Knife” for
Telegram. It aids OSINT analysts by archiving Telegram chats, gathering member
lists, finding users by location and mapping forwarded messages. The ability of
this program to perform various data scanning tasks, from basic chat info to
comprehensive history archiving and creating CSV-based edge lists for forwarded
messages, makes it especially useful.
Telepathy also uses asynchronous data handling to ensure data integrity
even when Telegram imposes rate limits. User-friendly output formats simplify
data processing and visualization.
TG
Stat
TG Stat also focuses on Telegram, offering a specialized solution for
extracting valuable information, tracking user activities and monitoring
discussions within Telegram channels and groups. Investigators can leverage TG
Stat to uncover insights and track potential threats, especially in contexts
where Telegram is a prominent communication channel.
TG Stat includes features for data extraction, advanced search,
visualization and user profiling. It provides real-time monitoring so
investigators can stay current on activities within targeted communities.