Open Source Threat Intelligence Platforms
What is open source threat intelligence (OSINT)?
Open source threat intelligence (OSINT) involves gathering and analyzing publicly available data to identify and mitigate security threats. It uses information from sources like websites, forums, and social media to provide insights into potential cyber threats.
Pros and Cons of Open Source Threat Intelligence Platforms
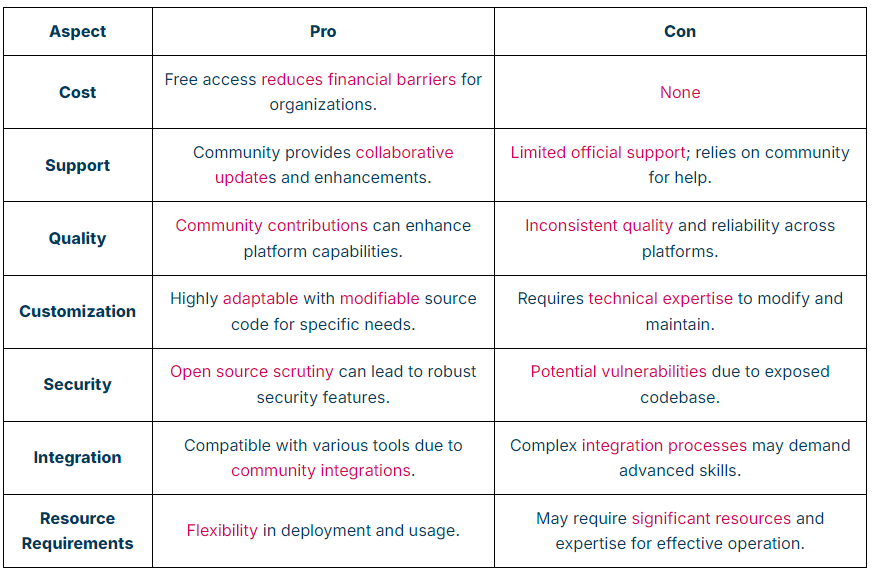
Open-source threat intelligence platforms offer significant benefits such as cost-efficiency with free access, customization through modifiable source code, and a diverse range of integrations due to community-driven enhancements.
However, they also come with challenges, including limited official support which relies heavily on community forums, variable quality and reliability, potential security vulnerabilities from an exposed codebase, and substantial resource requirements for effective customization, integration, and maintenance. These platforms are ideal for organizations that can leverage community resources and expertise but may pose risks for those needing consistent, high-quality support and security.
Here is a comprehensive overview of pros and cons for leveraging an open source CTI platform.
9 Open Source Threat Intelligence Sources
No matter what type of threat intelligence you need, you can find a publicly available resource.
1. Cybersecurity and Infrastructure Security Agency (CISA) News and Events
The CISA News and Events page provides a plethora of threat intelligence information. As the focal point for the US government's cybersecurity information sharing, the News and Events page supplements the CISA Automated Indicator Sharing (AIS) threat intelligence feed by providing additional documents beyond the machine-readable cyber threat indicators.
The News and Events page offers the following Cybersecurity Alerts and Advisories types:
· Alerts
· Analysis Reports
· Cybersecurity Advisories
· ICS Advisories
· ICS Medical Advisories
2. Red Canary
The Red Canary blog provides articles on new activity clusters, malware variants, and threat campaigns. The company publishes several reports including:
· An annual threat detection report
· An annual trends and takeaways report
· Monthly intelligence insights articles
Further, it offers technical deep dives into various threats, including IoCs.
3. SANS Internet Storm Center
The SANS Internet Storm Center provides various resources for security professionals. Run by volunteers, the Internet Storm Center offers:
· Infocon: a color-coded tracker that reflects malicious activity and possible connectivity disruptions
· Podcasts: short daily audio content on various topics with links to additional resources
· Diaries: technical posts discussing various security issues and threats
· Data: list of threat activity including numbers of reports, targets, and sources, world map showing current activity types, and top 10 source IPs at any given time
· Tools: links to additional resources and tools to help
· Dashboard: visualizations showing top activity
4. Microsoft
Microsoft is well-positioned to provide advanced threat intelligence since threat actors target its popular technologies and it has the resources to engage in research. The Microsoft Threat Intelligence blogs contain security research and threat intelligence from the organization's network of security experts.
The range of topics include:
· Deep divs into threat actors and their current activity
· New phishing attack types
· Threats based in different types of environments, like DevOps or Android phones
· Attack trends and insights reports
5. Pulsedive
Pulsedive is a free threat intelligence platform where users can search, scan, and enrich IPs, URLs, domains, and other IoCs that they obtain from their threat intelligence feeds.
Users can search by indicator based on any combination of:
· Value
· Type
· Risk
· Last seen timestamp
· Threat
· Feed
· Attribute
· Property
They can also search threats based on any combination of:
· Threat name
· Alias
· Category
· Risk
· Last seen timestamp
· Feed
· Threat attribute
6. PhishTank
Operated by the CISCO Talos Intelligence Group, PhishTank is a collaborative project that collects data and information about phishing. Users can
· Submit suspected phishes
· Track their submissions
· Verify other users submissions
They can also search the Phish Archive by targeted brand or ASN to determine whether an suspected phishing attack
· Valid
· Invalid (not a phish)
· Unknown
Further, they can filter the results by:
· Online
· Offline
· Unknown
PhishTank also provides an API and RSS feed options to make data sharing easier.
7. VirusTotal
VirusTotal aggregates data from antivirus tools and online scan engines so that users can check for malware that their antivirus tool may have missed. VirusTotal updates the malware signature frequently to provide the best data possible.
Additionally, users can analyze:
· Files
· Domains
· IPs
· URLs
VirusTotal notifies users when an antivirus solution determines a submitted file is malicious, and displays the detection label. Most of the URL scanners will distinguish between website type as well, including malware, phishing, and suspicious.
VirusTotal offers the following tools:
· API scripts and client libraries
· YARA rules
· Desktop apps
· Browser extensions
· Mobile apps
8. torBot
torBot is a tool that automates crawling and identifying different services on the Tor network, helping researchers and developers overcome the network's complexity and anonymity. According to the OWASP website, torBot currently contains the following completed features:
· Onion Crawler
· Get emails from site
· Save crawl information to JSON file
· Crawl custom domains
· Check if the link is live
· Built in updater
9. IntelligenceX Telegram Search Engine
The IntelX Telegram search engine enables users to type in search terms or a series of related phrases. The search returned information from Telegram:
· Channels
· Users
· Groups
· Bots
Top 7 Open Source Threat Intelligence Platforms in 2024
Open source threat intelligence platforms make use of threat intelligence data obtained from publicly available open sources. Security forums and national and international security announcement lists are examples.
Here are the best 7 threat intelligence platforms that you can choose to enhance your company's cybersecurity:
Free Open Source Threat Intelligence Platforms
AIS
AIS (Automated Indicator Sharing) is linked to the Department of Homeland Security (DHS). The AIS service facilitates the Federal Government and the private sector to quickly exchange cyber threat indicators.
AIS employs two open standards:
– the Structured Threat Information Expression (STIXTM) for cyber threat indicators and defensive measures information, and
– the Trusted Automated Exchange of Indicator Information (TAXIITM) for machine-to-machine communications.
These standards allow sharing of threat activity details (techniques, methods, processes, vulnerabilities, action plans) via a communications protocol.
Pulsedive
The free community threat intelligence database Pulsedive compiles open source feeds (examining huge numbers of IPs, domains, and URLs gathered from feeds and user submissions around the world), enriches IOCs and runs them using a risk-scoring algorithm that enhances data quality.
Users can use Pulsedive to submit, find, correlate, and update IOCs, as well as list risk factors as to why IOCs are considered threats.
TypeDB CTI
TypeDB Data – CTI is an excellent open source threat intelligence platform that enables companies to store and manage their cyber threat intelligence (CTI) knowledge.
It helps professionals gather fragmented CTI information into a single database and discover additional cyber threats insights. MITRE ATT&CK is an example dataset in its repository.
As exclusiveness of attribute values is a database guarantee, TypeDB allows links between hash values, IP addresses, or any other shared data value to be formed automatically.
Any data type's unique values are stored only once when attributes are added, and all future applications of those values are linked through associations.
Yeti
Yeti is a repository for cyber threat intelligence that is open, distributed, machine- and analyst-friendly, created by and for incident responders. The platform compiles threat intelligence, TTPs, indicators of compromise, and observables into a single, centralized repository while also automatically enriching the observables (e.g. resolve domains, geolocate IPs).
Conveniently enough, it has a user interface for humans and a web API interface for endpoints, allowing for simple integration with other tools that businesses may use.
Paid Open Source Threat Intelligence Platforms
Anomali ThreatStream
Anomali ThreatStream uses 140 open source feeds. Users can also buy more intelligence feeds from the Anomali App store. This extra information gives context to threats, which cuts down on false positives.
Anomali ThreatStream gathers many threat indicators to find new attacks. It uses a machine-learning algorithm to score IoCs, helping security teams maximize mitigation tasks.
LookingGlass Cyber Solutions
LookingGlass collects both structured and unstructured data from more than 87 feeds. It also buys extra commercial feeds.
By providing relevant data, LookingGlass helps multinational organizations and governments with unified threat protection against complex cyberattacks.
Additionally, a global team of security analysts adds value to the data feeds on the Looking Glass threat intelligence platform.
AT&T Cybersecurity
AlienVault Labs and its extensive Open Threat Exchange (OTX), the largest crowd-sourced collaborative threat exchange in the world, provide cyberthreat intelligence to AT&T Cybersecurity's Unified Security Management (USM).
USM updates every 30 minutes and provides centralized threat detection, incident response, and compliance management for cloud and on-premises environments.
Evaluating the Effectiveness of Open Source Threat Intelligence Resources
While there are numerous open source threat intelligence tools and feeds available, not all resources are created equal. To make the most of these resources and ensure that your organization is receiving the most valuable and relevant intelligence, it's essential to evaluate their effectiveness. In this section, we'll discuss several factors to consider when assessing the quality and usefulness of open source threat intelligence resources.
Timeliness: The rapidly evolving nature of cyber threats demands real-time or near-real-time updates on new vulnerabilities, malware, and threat actors. When evaluating a resource, consider the frequency of updates and ensure that the information provided is current and relevant.
Relevance: The value of threat intelligence is directly tied to its relevance to your organization and industry. Focus on resources that offer insights into threats and vulnerabilities specific to your sector, as well as those that provide actionable intelligence, such as Indicators of Compromise (IOCs).
Accuracy: Accurate threat intelligence is essential for effective decision-making and response. Assess the quality and reliability of the data provided by a resource, considering factors such as the source of the information and the process used for data validation.
Completeness: Comprehensive threat intelligence should cover various aspects of cyber threats, from vulnerabilities and exploits to malware and phishing campaigns. When evaluating resources, ensure that they provide a holistic view of the threat landscape, addressing multiple dimensions of cyber risk.
Ease of Integration: The ability to seamlessly integrate threat intelligence into your existing security infrastructure is crucial for maximizing its value. Look for resources that offer standardized formats, such as STIX or TAXII, which facilitate smooth integration with security tools and platforms.
Community Involvement: Resources that promote collaboration and information sharing among security professionals can provide valuable insights and perspectives. Engaging with active, knowledgeable communities can enhance the quality of the threat intelligence you receive.
By considering these factors when evaluating open source threat intelligence resources, organizations can identify the most valuable and effective tools and feeds for their needs. This enables them to make more informed decisions and develop robust strategies to mitigate emerging cyber threats and protect their digital assets.
Conclusion
Threat actors will never stop creating ways to carry out their attacks, so cybersecurity technology must keep up too.
Businesses can benefit from the full depth of knowledge of the global cybersecurity community by using cyber threat intelligence platforms, particularly open source ones.
These tools' data feeds get real-time updates from international professionals and enterprises, keeping you up to speed with every potential attack variation.