How to Navigate the World of Cyber Threat Intelligence: Essential Insights and Strategies
In the ever-evolving landscape of cybersecurity, staying ahead of potential threats is paramount for organizations. This is where threat intelligence comes into play. Threat intelligence is not just about gathering data; it's about deciphering the intentions, objectives, and attack patterns of potential threat actors. By doing so, organizations can make informed, proactive decisions, shifting from reactive defense to strategic offense in the ongoing battle against cyber threats.

What is Threat Intelligence?
Threat intelligence represents the compilation, refinement, and examination of data to gain insights into the intentions, objectives, and attack patterns of potential threat actors. This intelligence allows for quicker, more knowledgeable, and data-driven security decisions, shifting the organization's response from a reactive stance to a proactive one in the ongoing battle against cyber threats.
The Importance of Cyber Threat Intelligence
As defined by NIST, cyberthreat intelligence is a pivotal aspect of an organization's cyber resilience, encompassing its capacity to foresee, withstand, recover from, and adapt to various threats, assaults, or system compromises.
Threat intelligence is a crucial driver for cybersecurity programs, providing strategic insights that enable organizations to accurately identify and respond to cyberattacks. Additionally, the process of acquiring this intelligence helps with risk management by uncovering weaknesses in cybersecurity systems. This allows security teams to allocate resources more efficiently to address the most pressing cyberthreats specific to their industry, thus safeguarding valuable data, assets, and intellectual property.
Advantages of Cyber Threat Intelligence
An effective Cyber Threat Intelligence (CTI) program backed by skilled analysts can significantly bolster cybersecurity and resilience in numerous ways:
· Establishing proactive cyber defense: Unlike traditional reactive approaches that focus on responding to known threats, CTI enables organizations to gain insights into potential threat actors and anticipate future attacks.
· Improving risk management plan: CTI offers actionable insights into the motivations, tools, and techniques used by potential threat actors. Chief Information Security Officers (CISOs) and Security Operations Centers (SOCs) can leverage these insights to assess risk profiles and allocate cybersecurity resources efficiently, maximizing threat detection and protection capabilities.
· Improving incident response: Beyond supporting preventative measures, CTI provides insights that enhance an organization's preparedness for responding to and recovering from cyberattacks. A thorough understanding of the breach's circumstances can significantly minimize its impact.
· Increasing employee awareness: Organizations can leverage CTI to educate employees on cyber threats and establish security-oriented operating procedures and training, thereby enhancing their overall security posture.
The Challenges of Cyberthreat Intelligence
As the importance of collecting cyberthreat intelligence (CTI) grows in today's digital world, it is accompanied by a set of unique challenges. Here are a few noteworthy ones:
· Information overload: In the realm of cyberthreat intelligence (CTI), teams are confronted with the task of not only collecting but also processing and analyzing vast amounts of data. Among this vast array of information, it's crucial for them to discern between ordinary and malicious activities. Furthermore, the evaluation of threats involves determining the relevance of the information to the specific industry, size, and risk profile of the organization, taking into account various other factors.
· Information updates: The success of a CTI program hinges heavily on the promptness of the information being scrutinized. Decisions formulated based on outdated CTI can hinder an organization's ability to detect threats, thereby increasing its vulnerability to cyberattacks.
· Compliance: A significant aspect of CTI involves the handling of personally identifiable information (PII). It's imperative for organizations to ensure that all CTI systems adhere to the applicable data protection regulations, thus safeguarding the privacy of individuals.
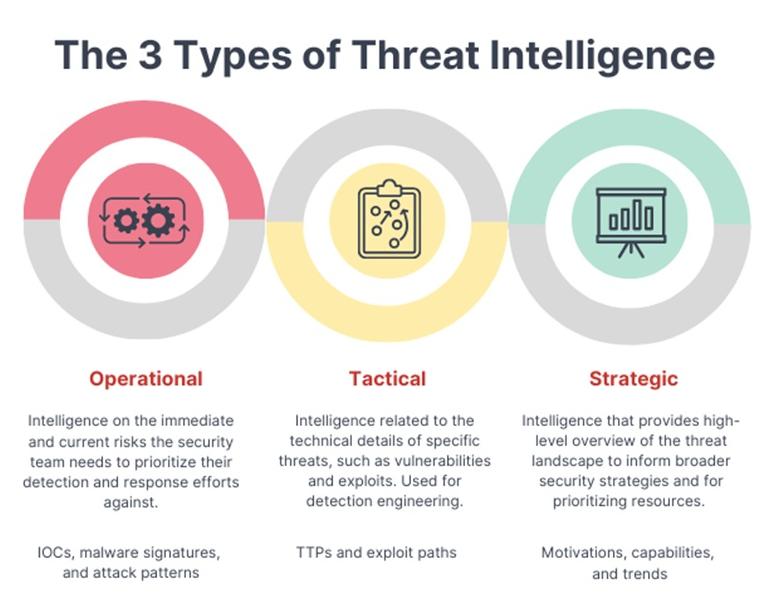
Types of Cyber Threat Intelligence
Cyber Threat Intelligence encapsulates the compilation and analysis of multi-source cybersecurity data, utilizing advanced analytical algorithms. By collecting large amounts of data about current cybersecurity threats and trends and performing analytics on this data, threat intelligence providers are able to extract actionable insights that empower their clients to detect and preempt cyber threats more effectively.
Organizations exhibit a diverse range of intelligence requirements, spanning from basic information on current malware variants employed in attack campaigns to high-level insights aimed at guiding strategic investments and policy formulation. This diversity necessitates the classification of threat intelligence into three distinct types:
· Operational: Operational threat intelligence emphasizes the tools (such as malware and infrastructure) and techniques employed by cyber attackers to achieve their objectives. This understanding aids analysts and threat hunters in identifying and comprehending attack campaigns.
· Tactical: Tactical threat intelligence centers on identifying specific malware types or other cyberattacks using indicators of compromise (IoCs). This intelligence is ingested by cybersecurity solutions and utilized to detect and mitigate incoming or ongoing attacks.
· Strategic: Strategic threat intelligence offers a high-level perspective, focusing on overarching trends within the cyber threat landscape. This type of intelligence caters to executives, often without a cybersecurity background, who require an understanding of their organization's cyber risk as a component of their strategic planning.
Cyber Threat Intelligence Life Cycle
Cybersecurity experts apply the concept of a lifecycle to threat intelligence. A standard lifecycle for cyber threats comprises the following stages: direction, collection, processing, analysis, dissemination, and feedback.
Phase 1: Direction
This phase revolves around establishing the objectives for the threat intelligence program. It might include:
· Identifying the organizational areas that require protection and possibly prioritizing them.
· Determining the specific threat intelligence needed to safeguard assets and respond to potential threats.
· Understanding the potential organizational impact of a cybersecurity breach.
Phase 2: Collection
This phase involves the collection of data to fulfill the objectives set in the orientation stage. Both the quantity and quality of data are essential to avoid missing crucial threats or being misled by false positives. Organizations need to identify their data sources, such as:
· Metadata from internal networks and security devices
· Threat data streams from trusted cybersecurity institutions
· Interviews with knowledgeable stakeholders
· Open source news sites and blogs
Phase 3: Processing
All the gathered data must be transformed into a format that the organization can utilize. Different data collection methods require distinct refinement methods. For instance, data from human interviews might require verification and cross-checking with other data sources.
Phase 4: Analysis
After refining the data into a usable format, it undergoes analysis. Analysis transforms the information into actionable intelligence that can guide organizational decisions. These decisions might encompass increasing investments in security resources, investigating specific threats, taking actions to mitigate imminent threats, and determining the necessary threat intelligence tools.
Phase 5: Dissemination
After conducting thorough analysis, it is crucial to disseminate the pivotal recommendations and conclusions to the pertinent stakeholders within the organization. Each team within the organization possesses unique requirements. To ensure effective dissemination of intelligence, it is advisable to inquire about the specific intelligence needs of each audience, the preferred format, and the frequency of dissemination.
Phase 6: Feedback
Feedback obtained from stakeholders serves as a valuable input for enhancing the threat intelligence program, thereby aligning it with the requirements and goals of every group. The term 'lifecycle' underscores the fact that threat intelligence is not a linear or one-time process. Rather, it is a circular and iterative approach that organizations embrace for ongoing refinement and improvement.
Understanding the Evolution of Cyber Threat Intelligence Frameworks
As the digital world continuously transforms, organizations are constantly on the lookout for ways to safeguard their assets from an unrelenting wave of cyber threats. In this context, cyber threat intelligence (CTI) has become an essential defensive armament.
The significance of CTI frameworks lies in their ability to provide businesses with the knowledge and strategies necessary to foresee and counter cyber attacks. To fully grasp the value of the most recent CTI frameworks, it is imperative to delve into their evolution.
A Brief History of Cyber Threat Intelligence
The inception of CTI frameworks dates back to the early days of the internet, where security measures were predominantly reactive, centered on detecting and containing threats after they had already breached systems.
As cyber threats multiplied and grew more sophisticated, reactive approaches proved insufficient. This led to the advent of CTI, offering a proactive, strategic approach that involved:
· Identifying
· Understanding
· Preparing for potential threats before vulnerabilities were exploited
Initial CTI frameworks were relatively basic and often hampered by limited data sources and reliance on manual analysis. However, as technology advanced, organizations gained the ability to collect large amounts of data from different sources. This led to the integration of big data analytics and machine learning into CTI frameworks. This shift has facilitated automated data collection and analysis, enabling security teams to more effectively sift through large amounts of data to identify imminent threats.
In recent years, CTI frameworks have undergone significant advancements, driven by the evolution of AI, predictive analytics, and cloud computing. Today's frameworks harness these technologies to:
· Deliver timely and accurate threat intelligence
· Recognize patterns and trends
· Forecast potential threats in the future
These advancements have strengthened organizational defenses to unprecedented levels. Furthermore, the integration of CTI with other security domains, such as risk management and incident response, has become crucial, fostering a more holistic and cohesive approach to cybersecurity.
6 Steps to Building a Cyber Threat Intelligence Framework
Looking to establish a cyber threat intelligence framework for your organization? Here's a step-by-step guide to help you along the way:
Step 1: Identifying Potential Threat Vectors
Before mounting a defense, understanding the potential sources of cyber threats is crucial. Identifying threat vectors and actors gives your business a clearer picture of its digital weaknesses. Collaborate with your security teams and utilize cybersecurity platforms to uncover patterns and trends that indicate potential attack avenues. Recognizing risks like phishing campaigns, malware distribution networks, website impersonation, and even malicious insiders can significantly strengthen your defense posture.
Step 2: Gathering Intelligence
Once you've identified potential threats, it's time to gather actionable intelligence on them. Leverage a combination of open-source intelligence (OSINT) tools, industry feeds, and proprietary platforms to gather comprehensive data. Your information security team should have the latest insights to support this stage and provide timely intelligence.
Step 3: Analyzing the Data
After gathering intelligence, the next step is to analyze and interpret the data. Collaborate closely with fraud detection teams, as they can offer unique insights into potential financial vulnerabilities and anomalies. Utilize advanced analytics tools to sift through the data and uncover patterns or irregularities. This stage aims to transform raw data into actionable insights, ensuring that threats are understood in their proper context and scope.
Step 4: Developing a Strategy
With the insights gained, it's crucial to craft a comprehensive security strategy. The cornerstone of an effective strategy lies in devising countermeasures against identified threats. This could involve strengthening authentication protocols, tightening access controls, or employing cutting-edge encryption techniques to establish a robust initial defense line.
However, no defense is foolproof. This necessitates the development of incident response plans. These contingency plans detail the steps to be taken in case of a breach, aiming for swift action and minimizing potential damage. Everything from immediate threat neutralization to communication protocols informing stakeholders of the breach is crucial.
Given the constantly evolving nature of cyber threats, a static strategy is insufficient. It's vital for the security strategy to remain adaptable, with provisions for periodic reviews and updates. Regular consultations with security and IT teams are essential to achieve this. Their practical experience and expertise provide invaluable feedback, ensuring the strategy remains comprehensive, updated, and capable of addressing the latest threats.
Step 5: Executing the Strategy
A strategy is only effective if it's implemented correctly. The next step involves executing the devised plans. This could involve patching software vulnerabilities, deploying advanced intrusion detection systems, and more. At this stage, seamless collaboration between digital business teams, fraud teams, and security personnel is paramount to ensure strategies are implemented precisely and vulnerable systems are fortified against potential attacks.
Step 6: Continuous Monitoring and Improvement
The digital threat landscape is constantly evolving. What works today might be obsolete tomorrow. Therefore, it’s essential to implement a cyber threat intelligence framework and continuously monitor and improve upon it. Regular audits, system checks, and feedback loops can ensure your defenses remain impenetrable. Comprehensive, structured responses become imperative as cyber threats grow in complexity. Incorporating these steps into developing your organization’s cyber threat intelligence framework will pave the way for a robust and dynamic defense system.
Conclusion
In conclusion, threat intelligence is the cornerstone of modern cybersecurity. It empowers organizations to anticipate, prepare for, and mitigate cyber threats effectively. From establishing proactive defense strategies to enhancing incident response capabilities, threat intelligence plays a pivotal role in safeguarding valuable data, assets, and intellectual property. By embracing the power of threat intelligence, organizations can navigate the complex cybersecurity landscape with confidence and resilience.