Exploring Open Source Intelligence(OSINT) Techniques
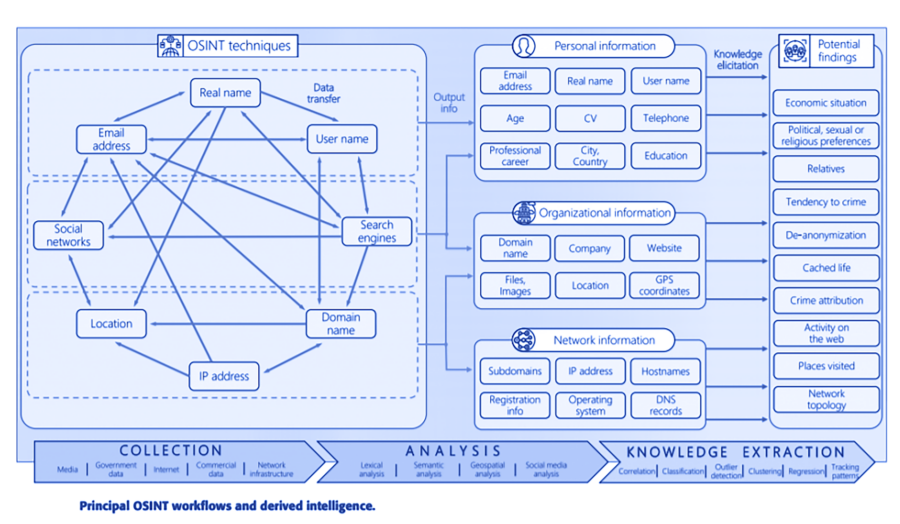
Open Source Intelligence (OSINT) involves the process of collecting, analyzing, and utilizing information from publicly available sources. Widely used by government agencies, military organizations, and private sector companies, OSINT plays a crucial role in threat identification, trend monitoring, and decision-making. By mastering a variety of OSINT techniques, intelligence professionals can efficiently extract valuable data from the vast expanse of available information. This article delves into the primary OSINT gathering methods, common techniques, and explores the future potential of artificial intelligence in this field.

OSINT Gathering Techniques
Open Source Intelligence (OSINT) relies on diverse methodologies to gather and analyze publicly available information. These techniques vary from passive observation to active engagement, each tailored to extract valuable insights from digital sources.
Passive Collection
Passive collection forms the cornerstone of OSINT, involving the unobtrusive retrieval of data from publicly accessible sources. This method includes scraping websites, utilizing open APIs like Twitter's, and accessing deep web repositories. By aggregating data from these sources, analysts compile and parse information for actionable intelligence. This approach is favored for its non-intrusive nature, minimizing the risk of detection while maximizing data coverage across the web.
Semi-Passive Techniques
Semi-passive techniques demand a higher level of expertise and finesse in information retrieval. They operate by directing traffic to target servers under the guise of normal internet activity, aiming to glean insights about system configurations and vulnerabilities. By mimicking legitimate user behavior, such as browsing patterns or API calls, analysts avoid triggering suspicion while acquiring critical data. This method bridges the gap between passive observation and more intrusive forms of data collection.
Active Collection
In contrast to passive and semi-passive methods, active collection involves direct interaction with targeted systems to extract specific information. This approach utilizes advanced technologies to probe open ports, scan server infrastructures, or assess web application security. While highly effective in uncovering detailed insights, active collection increases the risk of detection. Activities such as port scanning or intrusive probing may trigger alarms in target systems, alerting administrators to potential security breaches or unauthorized access attempts.
Active OSINT also encompasses social engineering tactics, where analysts manipulate human interactions to extract sensitive information. By exploiting psychological vulnerabilities or leveraging trust relationships, social engineering aims to bypass technical defenses and gather intelligence through interpersonal means. This method underscores the multifaceted approach of OSINT, integrating technical prowess with behavioral understanding to achieve comprehensive intelligence objectives.
Common OSINT Techniques
OSINT practitioners deploy a diverse array of techniques to dissect and interpret digital information, enriching their understanding of complex environments and scenarios.
1. Crafting Effective Search Queries: The Art of Refinement
Crafting precise search queries is akin to sculpting raw data into actionable insights. By leveraging advanced search operators such as quotation marks for exact phrases, minus signs for exclusions, and site: commands for domain-specific searches, analysts refine their queries with surgical precision. This meticulous approach ensures that search results are tailored to extract pertinent information while filtering out noise. The art of query refinement lies at the core of OSINT, enabling analysts to uncover hidden connections and extract valuable nuggets of data from vast information landscapes.
2. Social Media Monitoring: Beyond Posts to Insights
Beyond monitoring individual posts, OSINT professionals delve into the dynamics of social media interactions. Using specialized scrapers and APIs, analysts track user behaviors, sentiment trends, and viral phenomena across platforms. This comprehensive approach provides a nuanced understanding of public opinion, emerging trends, and evolving narratives. By analyzing follower dynamics, engagement patterns, and trending hashtags, practitioners glean actionable intelligence that informs strategic decision-making and mitigates reputational risks.
3. Metadata Analysis: Decoding Digital Clues
In an era saturated with multimedia content, metadata analysis emerges as a critical OSINT technique. Embedded within digital files, metadata contains valuable clues about their origins, including timestamps, geolocation coordinates, and device information. Tools like ExifTool and Metadata++ enable analysts to extract and interpret these digital fingerprints, unraveling the context and authenticity of multimedia content. This forensic approach enhances data credibility and enriches investigative outcomes by uncovering hidden insights concealed within digital artifacts.
4. Unveiling Hidden Layers: Website and Source Code Analysis
OSINT practitioners extend their scrutiny beyond surface-level web content by analyzing underlying HTML source codes and metadata. By scrutinizing website architecture, embedded comments, and metadata tags, analysts unearth hidden information and contextual clues. WHOIS lookup services further complement this investigative toolkit by revealing domain registration details, ownership histories, and administrative contacts. This meticulous examination of digital footprints enables analysts to reconstruct historical timelines, identify threat actors, and uncover covert activities concealed within web infrastructures.
5. The Visual Odyssey: Reverse Image Search
Visual intelligence plays a pivotal role in OSINT, facilitated by advanced image recognition technologies and reverse image search engines. Platforms like Google Images, Tineye, and Yandex employ sophisticated algorithms to scan and analyze visual content across the internet. This visual reconnaissance enables analysts to trace image origins, verify authenticity, and identify instances of image manipulation or misrepresentation. By conducting a visual odyssey through digital imagery, OSINT practitioners enrich data comprehension and uncover visual narratives that transcend linguistic barriers.
6. Deciphering Digital Trails: Email Header Analysis
Email communications serve as a treasure trove of digital breadcrumbs, revealing crucial metadata embedded within email headers. OSINT analysts leverage online tools and email clients to dissect these headers, extracting valuable information such as sender IP addresses, server routes, and transmission timestamps. This forensic analysis illuminates the origins, pathways, and destinations of email communications, facilitating attribution and verifying the authenticity of digital communications. Email header analysis empowers analysts to trace digital trails, uncover covert communications, and discern patterns of malicious activity within cyberspace.
7. Unearthing Official Chronicles: Public Records Search
Public records represent a foundational resource for OSINT investigations, providing authoritative insights into legal filings, property transactions, and corporate registrations. Government databases, court records, and business directories serve as repositories of official narratives and historical documentation. OSINT analysts navigate these archives to reconstruct factual accounts, validate identities, and corroborate investigative findings. By piecing together fragments of public records, analysts illuminate the legal, financial, and operational landscapes that underpin societal structures and organizational frameworks.
8. Navigating the Digital Geography: Geolocation Techniques
Geolocation techniques enable OSINT practitioners to map digital footprints and pinpoint geographic origins based on IP addresses and digital coordinates. Tools such as MaxMind and IPinfo translate IP addresses into geographic locations, enhancing data granularity and spatial context within investigative analyses. Geolocation techniques empower analysts to correlate digital activities with physical locations, uncovering patterns of behavior, and identifying emerging trends across global landscapes. By navigating the digital geography, OSINT professionals discern spatial relationships, track movement patterns, and contextualize digital interactions within real-world contexts.
9. A Sentinel in the Shadows: Dark Web Monitoring
The dark web represents a clandestine realm of encrypted networks, hidden forums, and illicit marketplaces that evade conventional search engines. OSINT specialists deploy specialized tools and services to monitor dark web activities, surveilling discussions on cyber threats, illicit transactions, and underground operations. Dark web monitoring serves as a sentinel in the shadows, providing early warning signals of emerging threats, nefarious activities, and malicious intent within obscured digital environments. By vigilantly patrolling dark web channels, analysts mitigate risks, preempt vulnerabilities, and safeguard organizational assets against clandestine adversaries.
10. Decoding Events through News Analysis: A Media Odyssey
News media serves as a dynamic repository of current events, evolving narratives, and societal trends that shape public discourse. OSINT analysts conduct systematic news analysis to decipher unfolding stories, extract actionable insights, and discern underlying motivations driving media coverage. By dissecting news articles, press releases, and editorial content, analysts uncover hidden connections, contextualize unfolding events, and anticipate future developments. News analysis empowers OSINT professionals to forecast trends, mitigate risks, and inform strategic decision-making within dynamic socio-political landscapes.
11. Lingual Alchemy: Language Translation Tools
In a globally interconnected world, linguistic diversity presents both a challenge and an opportunity for OSINT practitioners. Language translation tools such as Google Translate and DeepL facilitate multilingual analysis, enabling analysts to decode information from diverse linguistic sources. By translating foreign languages into comprehensible insights, these tools broaden the scope of OSINT investigations, uncovering cross-cultural perspectives, and facilitating cross-border collaboration. Lingual alchemy transforms linguistic barriers into bridges, fostering deeper understanding and enhancing situational awareness within international contexts.
12. Structured Insights: Public API Data Harvesting
Application Programming Interfaces (APIs) serve as digital gateways to structured data repositories, offering access to real-time information on social media trends, financial markets, weather forecasts, and demographic statistics. OSINT analysts harness API data harvesting techniques to retrieve curated datasets, analyze trends, and extract actionable insights. By integrating API-driven analytics into investigative workflows, analysts uncover patterns, forecast trends, and inform evidence-based decision-making across diverse domains. Structured insights derived from public APIs empower analysts to navigate data-rich landscapes, unlock hidden potentials, and drive informed strategies within dynamic digital ecosystems.
Artificial Intelligence: The Future of OSINT?
As OSINT technology evolves, there is growing advocacy for integrating artificial intelligence (AI) and machine learning (ML) into OSINT research processes.
Recent public reports reveal that government and intelligence agencies are already leveraging AI to collect and analyze data from social media platforms. Military organizations are employing AI/ML technologies to detect and address threats such as terrorism, organized cybercrime, misinformation, and other national security issues on these platforms.
With AI/ML technologies becoming increasingly accessible to the private sector, they offer several enhancements:
Enhanced Data Collection: AI/ML can filter out irrelevant data and prioritize crucial information, streamlining the data collection process.
Improved Data Analysis: These technologies can correlate relevant information and uncover valuable patterns, making the data analysis phase more efficient.
Actionable Insights: AI/ML can process significantly larger volumes of raw data than human analysts, providing deeper and more actionable insights from the available data.
Conclusion
As technology continues to evolve, the importance of OSINT in information gathering and analysis will only grow. The integration of artificial intelligence and machine learning further enhances the efficiency and accuracy of OSINT processes. With the increasing availability and application of AI/ML techniques, OSINT is poised to provide deeper insights and more effective solutions for organizations across various sectors. Staying abreast of the latest developments and methodologies in this dynamic field is essential for maintaining a competitive edge and ensuring security.