Exploring Digital Forensics
Digital forensics, is a critical field dedicated to the recovery, investigation, and analysis of data from digital devices, particularly in relation to cybercrimes. Initially focused on computers, the discipline has evolved to include a wide range of digital devices, from smartphones and tablets to cloud computing systems. As our reliance on digital technology grows, so does the importance of digital forensics in both criminal and civil investigations.
What is Digital Forensics?
Digital forensics, also known as digital forensic science, is a specialized branch of forensic science dedicated to the recovery, investigation, and analysis of data found in digital devices, primarily in relation to cybercrimes. Initially synonymous with computer forensics, the scope of digital forensics has broadened to encompass the examination of any device capable of storing digital data.
As society increasingly relies on computer systems and cloud computing, digital forensics has become a pivotal aspect for law enforcement agencies and businesses alike. The discipline involves the meticulous process of identifying, preserving, analyzing, and documenting digital evidence. This is carried out using scientifically validated methods to ensure the integrity and admissibility of the evidence in legal proceedings.
Digital forensics plays a critical role in both criminal and civil investigations. For example, cybersecurity teams utilize digital forensics to trace cybercriminals responsible for malware attacks, while law enforcement agencies analyze data from suspects' devices in various criminal cases. The field treats digital evidence with the same rigor as physical evidence, adhering to strict forensic procedures, often referred to as the chain of custody, to prevent tampering and ensure reliability.
An emerging aspect within this field is Digital Forensics and Incident Response (DFIR), which combines traditional computer forensics with incident response tactics to swiftly address and mitigate cyber threats while maintaining the integrity of the associated digital evidence.
Why Digital Forensics is Important?
Digital forensics, or digital forensic science, originated in the early 1980s with the rise of personal computers and gained significant attention in the 1990s. However, it wasn’t until the early 21st century that countries like the United States formalized their digital forensics policies, driven by the increase in computer crimes and the decentralization of law enforcement agencies. This shift towards standardization was essential to ensure that digital evidence could be handled in a manner that made it admissible in court.
The first cybercrimes were recognized with the 1978 Florida Computer Crimes Act, which addressed unauthorized data modification or deletion. As the scope of cybercrimes expanded, additional laws were introduced to cover issues like copyright, privacy, harassment, and child pornography. Federal laws began to incorporate computer offenses in the 1980s, with Canada passing legislation in 1983, followed by the United States in 1986, Australia in 1989, and Britain's Computer Misuse Act in 1990.
The 1980s and 1990s saw significant growth in digital crime, prompting law enforcement agencies to form specialized units for technical investigations. For instance, the FBI launched a Computer Analysis and Response Team in 1984, and the British Metropolitan Police established a computer crime department in 1985. These efforts marked the beginning of digital forensics as a practical field, exemplified by cases like Cliff Stoll's pursuit of Markus Hess in 1986, where forensic techniques were used to identify cybercriminal activities.
The rapid increase in cybercrime in the 2000s further emphasized the need for standardized digital forensic practices. Various bodies and agencies began publishing guidelines for digital forensics, such as the British National Hi-Tech Crime Unit in 2001 and the Scientific Working Group on Digital Evidence in 2002. The international treaty, the Convention on Cybercrime, came into force in 2004, aiming to harmonize national computer crime laws and investigation techniques.
Today, digital forensics is more relevant than ever. The exponential growth of digital data—stemming from the proliferation of devices like computers, mobile phones, tablets, IoT devices, and other connected technologies—provides investigators with a wealth of digital evidence to analyze and understand a wide range of criminal activities, including cyberattacks, data breaches, and both criminal and civil investigations.
Proper collection, handling, analysis, and storage of digital evidence are crucial to prevent data loss, tampering, or inadmissibility in court. Forensics experts play a vital role in performing digital forensics investigations, and as the demand for these skills grows, job opportunities in the field are expected to increase significantly. The Bureau of Labor Statistics predicts a 31 percent rise in computer forensics job openings through 2029.
The Stages of Digital Forensics Investigations
1. Identification
The initial stage in a digital forensics investigation involves pinpointing the devices and resources that hold the pertinent data. This data can reside on organizational hardware such as desktops and laptops, or on personal devices like smartphones and tablets.
Once identified, these devices are secured and isolated to prevent any potential tampering. If the data resides on servers, networks, or in the cloud, it is crucial to restrict access to the investigation team only, ensuring the integrity of the data.
2. Extraction and Preservation
Following the identification and secure storage of the devices, forensic analysts employ specialized techniques to extract relevant data. This stage often involves creating a digital duplicate, known as a "forensic image," of the data. This duplicate is then used for detailed analysis, while the original devices and data are stored in a secure location to prevent any alterations.
3. Analysis
With the data securely duplicated, investigators utilize various techniques to uncover and analyze relevant information. This stage includes recovering deleted, damaged, or encrypted files using methods such as:
Reverse Steganography: Extracting hidden data by analyzing the underlying hash or character string of an image or data item.
File or Data Carving: Identifying and retrieving deleted files by locating fragments left behind.
Keyword Searches: Employing specific keywords to locate and examine pertinent information, including previously deleted data.
These techniques help forensic investigators unearth crucial evidence.
4. Documentation
After the analysis, the findings are meticulously documented to clearly outline the investigation process and its conclusions. This documentation is crucial for creating a timeline of activities related to the incident, such as data breaches, fraud, or unauthorized data access.
5. Presentation
The final stage involves presenting the findings to relevant authorities, whether in a court of law or to an internal committee. Forensic investigators may serve as expert witnesses, summarizing the evidence and explaining their discoveries to support legal or organizational decisions.
Techniques in Digital Forensics Investigations
Data forensic investigators employ various strategies to extract information from hardware systems, recover lost data, and analyze user behavior on digital devices. Both software and hardware solutions are used to copy evidence without causing damage.
Key techniques in digital forensics include:
Decrypting and Recovering Deleted, Encrypted, or Corrupted Files
Tools like EnCase® and FTK® are highly effective for this complex task. These forensic tools help investigators uncover critical evidence from otherwise inaccessible digital sources, aiding in the resolution of challenging digital cases.
Examining Database Data and Metadata
This technique is crucial for advanced database analysis and uncovering hidden patterns. Modern forensic technology allows investigators to analyze database structure, content, modifications, unauthorized access, and deleted files. Given that databases log user interactions, transactions, and system activity, this type of forensics can be pivotal in solving crimes and identifying security breaches. Investigators must understand database structures and querying languages for this work.
Investigating Network Communications
Security personnel analyze network communications to detect, prevent, and investigate criminal breaches. By examining network traffic, including data packets and logs, they can identify signs of intrusion or malicious activity. Appropriate tools can help detect and mitigate cyberattacks on infrastructure and digital communications.
Checking Mobile Devices
Mobile devices can store and quickly delete data. Investigators examine mobile operating systems and devices to access phone logs, text messages, and emails. These data points can reveal communication patterns and connections that support forensic investigations. Proper recovery and interpretation of this data are essential for building case narratives.
Inspecting Hard Disks
Creating sector-by-sector copies of hard disks provides reliable digital evidence. This method ensures that investigators can analyze an identical clone of the hard disk without compromising the original. Careful reproduction of cyber evidence is necessary to maintain data integrity and reliability.

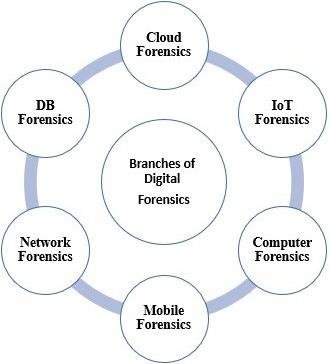
Branches of Digital Forensics
Digital forensics extends beyond computer forensics, covering data from various digital devices, including tablets, smartphones, flash drives, and cloud computing. Here are its main branches:
Computer Forensics
Focuses on finding, preserving, recovering, analyzing, and presenting digital evidence from computers and storage media. It is used in criminal investigations and civil proceedings, following strict guidelines to maintain a legal audit trail.
Mobile Device Forensics
Recovers digital evidence from mobile devices like phones, tablets, GPS devices, and PDAs. This branch addresses the challenges posed by varied devices, operating systems, and storage methods. Forensic examiners must be well-trained to handle the diverse tools and methods required.
Network Forensics
Monitors and analyzes network traffic for information gathering, legal evidence, or intrusion detection. This proactive investigation branch deals with the volatility and dynamism of network data, often used to identify intrusions and support law enforcement investigations.
Forensic Data Analysis (FDA)
Examines structured data to detect and analyze patterns of fraudulent activities, particularly in financial crime. FDA focuses on data from application systems or databases, contrasting with unstructured data typically analyzed by computer or mobile device forensics experts.
Database Forensics
Investigates databases and their metadata, including cached information in server RAM. It involves analyzing timestamps, validating user actions, and identifying transactions that indicate fraud or other wrongdoing.
Conclusion
In an era where digital devices are integral to daily life, the role of digital forensics has never been more crucial. From identifying cybercriminals to solving complex data breaches, digital forensics provides the tools and methodologies necessary to handle digital evidence with precision and integrity. As technology continues to advance, so too will the methods and importance of digital forensics, ensuring that investigators can effectively address and mitigate the growing array of cyber threats. Whether it’s through computer forensics, mobile device analysis, or network investigations, the field remains at the forefront of safeguarding our digital world.