Essential Threat Intelligence Tools for Modern Cybersecurity
In today's rapidly evolving cyber landscape, threat intelligence tools have become indispensable for organizations striving to safeguard their digital assets. These tools offer critical insights into potential cyber threats, enabling security teams to identify, assess, and mitigate risks before they can cause significant damage. By providing real-time data on emerging threats and vulnerabilities, threat intelligence tools empower organizations to make informed decisions, proactively defend against attacks, and maintain a robust security posture.

What is Threat Intelligence?
Threat intelligence involves gathering, refining, and analyzing data to reveal the intentions, goals, and methods of potential cyber adversaries. This intelligence plays a crucial role in cybersecurity by helping organizations identify who their attackers are, how they operate, and what their objectives might be. With this knowledge, security teams can make informed, data-driven decisions, allowing them to transition from a reactive to a proactive defense strategy. This proactive approach significantly improves an organization's ability to manage and mitigate cyber threats effectively.
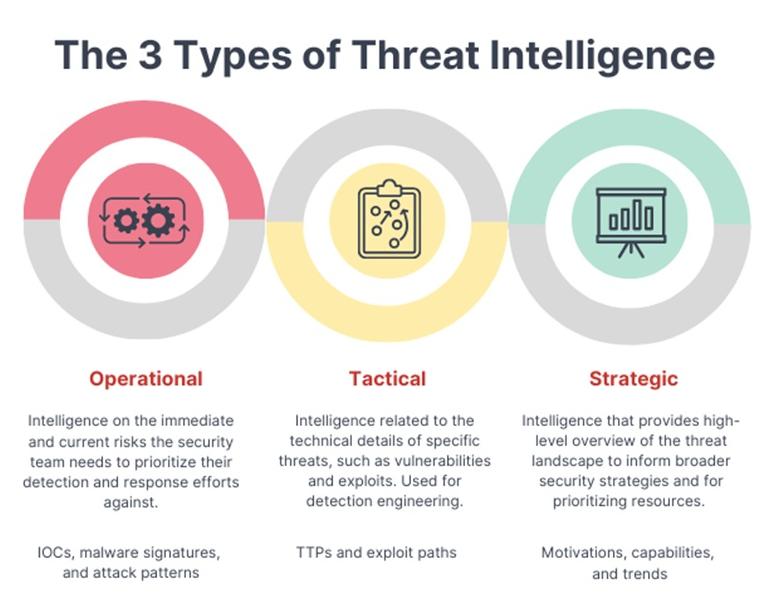
Types of Threat Intelligence
Strategic Intelligence
Strategic threat intelligence offers a high-level overview of the threat landscape, aiding key stakeholders and executives in decision-making. Presented through reports and briefings, it highlights major risks, overall attack patterns, and relevant political or environmental trends impacting the organization.
Tactical Intelligence
Tactical threat intelligence details the specific tactics and techniques used by threat actors. This information is crucial for security analysts, system architects, and network administrators to understand and defend against attacks. It includes data on the technology environment, vulnerabilities, and tools used by attackers.
Operational Intelligence
Operational threat intelligence focuses on specific cyber incidents, providing actionable insights for incident response teams. It includes technical details like attack vectors, exploited vulnerabilities, and command and control servers. This intelligence is often derived from threat intelligence feeds, which offer curated information on specific threat indicators such as malware hashes or suspicious domains.
What Are Threat Intelligence Tools?
Threat intelligence tools equip organizations with crucial information on the latest cyber threats, such as zero-day vulnerabilities, new malware strains, and exploits. These tools enhance security by identifying specific threats targeting networks, infrastructure, and endpoint devices.
They offer detailed insights into threat actors, their tactics, techniques, and procedures (TTPs), and recommended prevention and remediation methods. Security professionals use this intelligence to better safeguard systems and prepare for potential breaches.
Effective threat intelligence solutions must provide updates on emerging threats, detailed remediation guidance, and support threat analysis across various IT environments. Many integrate with existing security tools like SIEM, security testing, and vulnerability management software to enrich their functionality.
Top Threat Intelligence Tools
Effective threat intelligence tools are essential in today's complex cybersecurity landscape. Here are some popular tools, each with unique features and benefits:
ThreatConnect
ThreatConnect offers a comprehensive threat intelligence platform, incident response tools, and malware analysis capabilities. Its platform allows for streamlined threat data collection, analysis, and sharing, enhancing organizational threat detection and response. Additionally, ThreatConnect provides extensive resources such as training materials and a blog to keep security professionals informed and educated.
Recorded Future Fusion
Recorded Future Fusion delivers real-time threat intelligence, offering instant access to the latest global cyber threats. This tool helps organizations make informed decisions by providing actionable data on emerging threats, enabling proactive defense strategies. Its integration with other security tools enhances the overall security posture by enriching existing datasets with current threat information.
SolarWinds
SolarWinds offers a holistic view of an organization's security environment. It identifies potential threats across the network and provides tools to mitigate them effectively. SolarWinds' comprehensive monitoring and alerting capabilities ensure that organizations can promptly address vulnerabilities, thereby strengthening their cybersecurity defenses.
CrowdStrike
CrowdStrike provides instant visibility into network activities, facilitating rapid identification and response to threats. Its cloud-native Falcon platform uses AI and machine learning to detect sophisticated threats in real-time. CrowdStrike's robust endpoint protection, threat hunting, and incident response features help organizations stay ahead of cyber adversaries.
Real-World Applications of Threat Intelligence Tools
Finance
In the finance sector, threat intelligence tools help identify and counteract phishing attacks, fraudulent transactions, and data breaches. For example, banks use these tools to monitor for signs of credential theft and suspicious account activity, protecting customer data and maintaining trust.
Healthcare
Healthcare organizations use threat intelligence to safeguard sensitive patient information from ransomware attacks and data breaches. These tools help detect vulnerabilities in medical devices and IT systems, ensuring compliance with regulations like HIPAA.
Government
Government agencies leverage threat intelligence to protect national security infrastructure from espionage, cyber-terrorism, and hacktivism. These tools provide insights into potential state-sponsored attacks and help secure critical infrastructure and sensitive information.
Future Trends in Threat Intelligence
The future of threat intelligence is poised to be shaped by several key trends that will enhance the effectiveness and efficiency of cybersecurity measures.
Artificial Intelligence and Machine Learning
AI and machine learning are set to revolutionize threat intelligence by enabling faster and more accurate detection of cyber threats. These technologies will automate the analysis of large datasets, identifying patterns and anomalies that might be missed by human analysts. This will allow for real-time threat detection and response, significantly reducing the time it takes to mitigate risks.
Integration with Advanced Analytics
Future threat intelligence platforms will increasingly integrate with advanced analytics tools. This integration will provide deeper insights into threat patterns and attacker behaviors, allowing organizations to predict and prevent potential attacks more effectively. By leveraging big data analytics, these platforms will offer a comprehensive view of the threat landscape, enabling more strategic decision-making.
Collaboration and Information Sharing
As cyber threats become more sophisticated, collaboration between organizations will become crucial. Future threat intelligence efforts will emphasize the sharing of threat data across industries and borders. This collective approach will help build a more robust defense against cyber threats, as organizations can learn from each other's experiences and strategies.
Conclusion
In the ever-evolving landscape of cybersecurity, threat intelligence tools are indispensable for identifying, assessing, and mitigating risks. By offering real-time insights into potential threats and vulnerabilities, these tools empower organizations across various sectors—such as finance, healthcare, and government—to make informed decisions and proactively defend against cyber attacks. As technology advances, the integration of AI, machine learning, and advanced analytics will further enhance the effectiveness of these tools, enabling organizations to stay ahead of increasingly sophisticated cyber threats.