Essential Digital Forensics Tools for Cybersecurity Investigations
Digital forensics has become a cornerstone in modern cybersecurity, providing critical tools and methodologies to uncover and analyze data from digital devices. As cyber threats and computer crimes continue to rise, the role of digital forensics in investigating these incidents has never been more vital. From tracing the origins of a cyberattack to securing legally admissible evidence, digital forensics serves as a crucial link between technology and justice. The evolution of digital forensics has brought about specialized tools and techniques that allow investigators to handle increasingly complex digital environments.

What is Digital Forensics?
Digital forensics is a specialized branch of forensic science focused on recovering, examining, and analyzing data from digital devices. This process is crucial in investigating cybersecurity incidents and computer crimes. The objective is to identify malicious activities, uncover the sequence of events leading to an incident, and secure legally sound evidence for potential use in legal proceedings. Digital forensics involves various sub-fields, each with its own focus and methodologies.
The Historical Background and Evolution of Digital Forensics
The increasing use of personal computers and law enforcement's need to extract and store digital data from increasingly sophisticated electronic devices inspired digital forensics in the early 1980s. Developments in technology broadened computer forensics beyond computer crime. Smartphones, the internet, and cloud platforms have further expanded digital forensics.
In the early days, cyber forensics was crude, but better data extraction, analysis, and documentation tools expanded this discipline. More cybercrime laws created by authorities also necessitated the collection of digital evidence.
Sub-Fields of Digital Forensics
Digital forensics is divided into several sub-fields, each addressing different aspects of digital evidence:
Computer Forensics
This involves the investigation of computers and storage media. Analysts recover deleted files, examine file systems, and study user and software activities on computers.
Network Forensics
This branch focuses on monitoring and analyzing network traffic to understand attack methods, identify sources, and determine the breach's extent.
Forensic Data Analysis
This area involves examining large datasets from financial or business applications to detect patterns or anomalies indicative of fraudulent activities.
Mobile Device Forensics
With the widespread use of mobile devices, this sub-field has become essential. It involves extracting and analyzing data such as text messages, call logs, and location information from smartphones and tablets.
The Digital Forensics Process
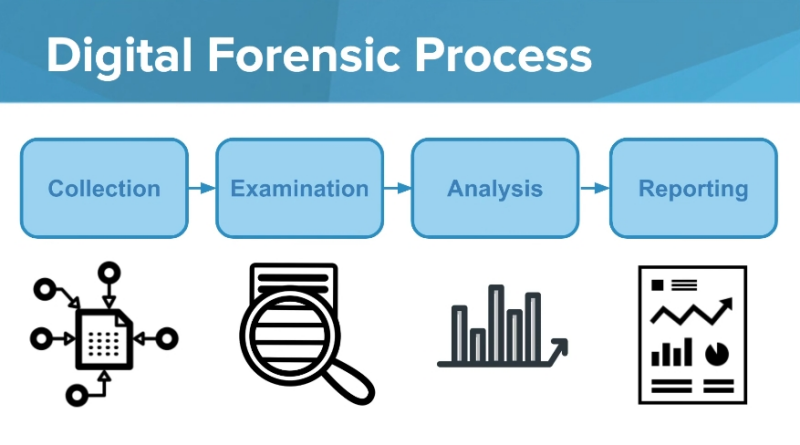
The digital forensics process may change from one scenario to another, but it typically consists of four core steps—collection, examination, analysis, and reporting.
Collection
The collection phase involves acquiring digital evidence, usually by seizing physical assets, such as computers, hard drives, or phones. It is critical to ensure that data is not lost or damaged during the collection process. You can prevent data loss by copying storage media or creating images of the original.
Examination
The examination phase involves identifying and extracting data. You can split this phase into several steps—prepare, extract, and identify.
When preparing to extract data, you can decide whether to work on a live or dead system. For example, you can power up a laptop to work on it live or connect a hard drive to a lab computer.
During the identification step, you need to determine which pieces of data are relevant to the investigation. For example, warrants may restrict an investigation to specific pieces of data.
Analysis
The analysis phase involves using collected data to prove or disprove a case built by the examiners. Here are key questions examiners need to answer for all relevant data items:
· Who created the data
· Who edited the data
· How the data was created
· When these activities occur
In addition to supplying the above information, examiners also determine how the information relates to the case.
Reporting
The reporting phase involves synthesizing the data and analysis into a format that makes sense to laypeople. These reports are essential because they help convey the information so that all stakeholders can understand.
Role of Digital Forensics Tools
Digital forensics tools are essential in assisting investigators and security analysts throughout the forensic analysis process. These tools help gather digital evidence, convert it into standard formats, and filter through large volumes of data to identify relevant information. They are designed to handle the complexities of modern digital investigations, including dealing with various file formats and systems.
Challenges in Digital Forensics
One of the primary challenges in digital forensics is managing the vast amount of data involved in investigations. The variety of formats and devices adds to the complexity, requiring tools that are versatile and compatible with a wide range of systems. Advanced search capabilities, automated analysis, and detailed reporting features are critical in efficiently managing these challenges.
Top Open Source Digital Forensics Tools
Here are some widely used open-source tools in digital forensics:
The Sleuth Kit (TSK)
The Sleuth Kit provides a suite of command-line tools and libraries for data extraction and forensic analysis on Windows and Unix systems. It forms the core of the popular Autopsy tool, allowing users to extract and analyze data from storage devices.
Autopsy
Autopsy is a digital forensics platform that acts as a graphical interface for tools included in The Sle uth Kit. It enables investigators to parse and analyze data, hash files, extract EXIF data, and create comprehensive reports in various formats.
Digital Forensics Framework (DFF)
DFF is a flexible, open-source computer forensics solution used to collect, preserve, and disclose digital evidence. It features a user-friendly GUI and a command-line interface, making it accessible to both professionals and non-experts.
Open Computer Forensics Architecture (OCFA)
Developed by the Dutch police, OCFA is an open-source framework designed for analyzing digital media in forensic labs. It supports integration with other open-source forensics tools and provides modules for extensive forensic analysis.
HashKeeper
HashKeeper is a database application that helps forensic investigators by using MD5 hashing to identify "known-good" and "known-bad" files, streamlining the digital media file scanning process.
Bulk Extractor
Bulk Extractor is an information extraction tool that scans files, directories, or disk images without parsing file systems. It efficiently handles various digital media formats, including hard drives and smartphones, and can perform social network forensics.
Computer-Aided Investigative Environment (CAINE)
CAINE is an open-source, Ubuntu-based distribution for digital forensics that integrates with existing security tools and provides a user-friendly GUI. It can be booted from removable media and run on various systems, including virtual machines.
SANS Investigative Forensics Toolkit (SIFT)
SIFT is a comprehensive suite of open-source tools for digital forensics and incident response, offering high compatibility with various evidence formats and regularly updated features for forensic investigations.
The Volatility Foundation
The Volatility Foundation provides an open-source framework for memory forensics, used for malware detection and incident response. It supports most systems and is written in Python, with the code available on GitHub.
Conclusion
In the ever-evolving landscape of cybersecurity, digital forensics tools play an indispensable role in ensuring that investigators can effectively collect, analyze, and present digital evidence. As cyber threats grow more sophisticated, the continued advancement and accessibility of these tools will be essential in maintaining robust defense mechanisms.