Enhancing Intelligence Gathering: Advanced OSINT Tactics
In today's interconnected world, the art of intelligence gathering has transcended traditional boundaries, leveraging diverse sources and advanced technologies to uncover critical insights. Open Source Intelligence (OSINT) stands at the forefront, offering a wealth of publicly accessible data that, when properly harnessed, provides a strategic advantage in both public and private sectors. From corporate espionage prevention to geopolitical analysis, OSINT techniques play a pivotal role in shaping informed decisions and mitigating risks.
Definition of Intelligence
Intelligence involves gathering, evaluating, analyzing, integrating, and interpreting information to produce specialized data that supports national interests. It helps reduce ambiguity in observing external activities. For example, adversaries might seek intelligence on military capabilities, diplomatic strategies, economic programs, or corporate information to gain a strategic edge.
Types of Intelligence
Strategic Intelligence
Informs long-term policy and integrates data on politics, military, economics, and technology. It evolves over time, resulting in comprehensive studies and estimates.
Operational Intelligence
Focuses on current or near-term events, assessing the ongoing capabilities of programs or operations without long-term projections.
Five Core Disciplines of Intelligence Gathering
Intelligence gathering encompasses five primary disciplines, often referred to as "intelligence collection disciplines" or "the INTs."
Human Intelligence (HUMINT)
This involves the collection of information from human sources. It can be conducted openly, such as when FBI agents interview witnesses or suspects, or covertly through espionage. Within the U.S., the FBI handles HUMINT collection, while the CIA and other U.S. components manage it abroad. Although HUMINT is crucial, the FBI also relies on other methods, including SIGINT, MASINT, and OSINT.
Signals Intelligence (SIGINT)
SIGINT involves the interception of electronic transmissions, which can be collected by ships, planes, ground sites, or satellites. A subset of SIGINT is Communications Intelligence (COMINT), focusing on the interception of communications between parties. U.S. SIGINT satellites are designed by the National Reconnaissance Office, but the primary responsibility for SIGINT activities lies with the National Security Agency (NSA).
Imagery Intelligence (IMINT)
Sometimes called photo intelligence (PHOTINT), IMINT involves the collection of images, historically starting with balloon reconnaissance during the Civil War and expanding significantly during World Wars I and II with aerial photography. Today, the National Reconnaissance Office designs and operates imagery satellites, while the National Geospatial-Intelligence Agency processes and utilizes the imagery. Geospatial Intelligence (GEOINT) involves the analysis and visual representation of security-related activities on Earth, integrating imagery and geospatial information.
Measurement and Signatures Intelligence (MASINT)
This less well-known discipline focuses on weapons capabilities and industrial activities, using advanced processing of data from IMINT and SIGINT systems. It includes telemetry intelligence (TELINT) and electronic intelligence (ELINT), both of which contribute to MASINT. The Defense Intelligence Agency’s Central MASINT Office (CMO) is the principal user of MASINT data. With the growing concern over weapons of mass destruction, MASINT's role has become increasingly vital, helping to identify chemical weapons or unique features of unknown weapon systems. The FBI’s forensic work, such as the Chem-Bio Sciences Unit’s analysis of chemical, biological, or nuclear materials, supports the prevention and investigation of terrorist activities and is an example of MASINT.
Open Source Intelligence (OSINT)
OSINT involves collecting information from publicly available sources, such as media outlets, academic papers, professional conferences, and government reports. Unlike other INTs, OSINT is not confined to a single agency but is gathered by the entire U.S. Intelligence Community. Its accessibility is an advantage, though the vast amount of available data can make determining valuable information challenging. OSINT requires careful review and analysis to ensure its usefulness and reliability for policymakers.
Information Gathering vs. Intelligence Gathering
Information gathering is the initial phase of intelligence, involving the collection of data from diverse sources such as the internet (OSINT), government records, the dark web, newspapers, personal contacts (HUMINT), and covert surveillance. However, information alone is not sufficient for intelligence. The transformation of raw data into actionable intelligence involves several critical steps:
Step 1: Searching and Retrieval
Trained officers initiate the process by knowing where to search and how to retrieve pertinent information efficiently. This foundational step ensures the acquisition of relevant data from a multitude of sources.
Step 2: Filtering and Analysis
The next phase involves filtering out irrelevant or unreliable data, a process that requires reading between the lines to interpret the underlying context. Additional data is sought to confirm initial findings, ensuring the reliability and comprehensiveness of the information.
Step 3: Prioritization and Relevance
In the final step, the gathered data is prioritized based on its relevance and importance. This assessment determines which pieces of information are most crucial for decision-making and strategy development.
The outcome of intelligence gathering is a comprehensive risk report that provides actionable advice on protecting oneself, family members, and organizational assets. This report is crucial for mitigating potential threats and ensuring security.
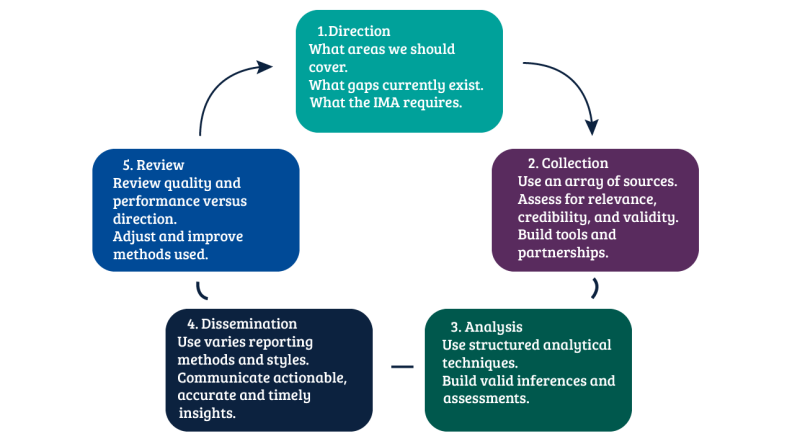
Open Source Intelligence Gathering Techniques
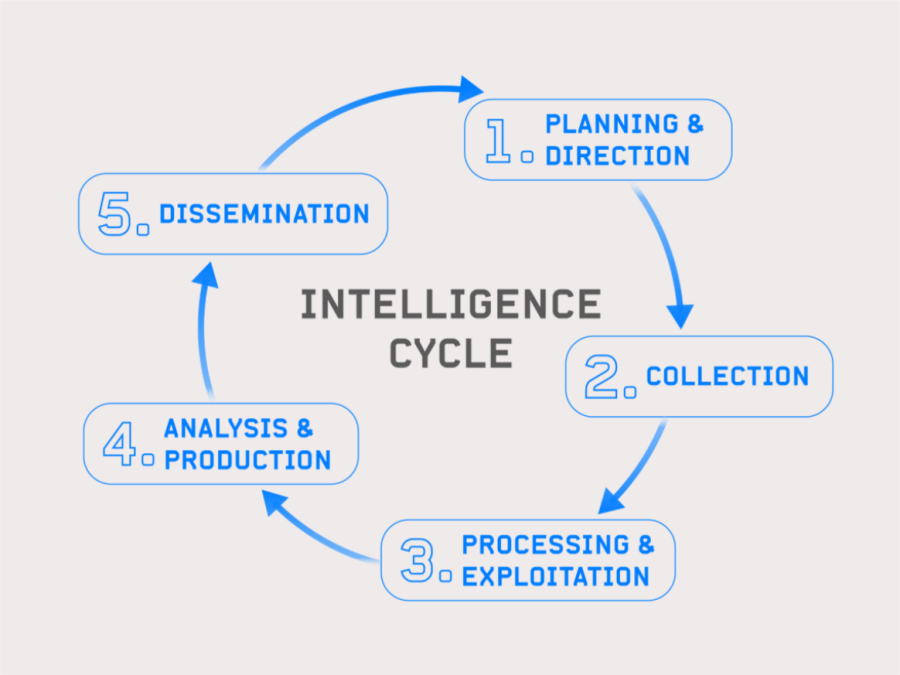
Leveraging the Intelligence Cycle in OSINT
Planning and Direction
This foundational step manages the entire intelligence process, from identifying data needs to delivering the final product. It involves setting priorities, translating requirements, preparing collection plans, and issuing collection requests. Specific collection capabilities are tasked based on the type of information required and the availability of assets. This stage sets the groundwork for a structured investigation, ensuring all subsequent efforts are well-directed and purposeful.
Collection
The collection phase involves acquiring information from various sources and providing it to processing elements. Collection activities are guided by specific taskings and often involve redundant efforts using multiple intelligence disciplines to ensure reliability and confirm assessments. Secure, rapid, and reliable communications are crucial for effective data exchange and coordination during this stage. The goal is to gather comprehensive and accurate raw data.
Processing and Exploitation
Once collected, the information is converted into formats suitable for analysis. This may include translating intercepted messages, producing videos, processing photographs, and correlating technical intelligence data. The objective is to prepare the raw data for detailed analysis by organizing it into a comprehensible and usable format. This step ensures that the data is ready for thorough examination and interpretation.
Analysis and Production
In this phase, analysts evaluate, interpret, and integrate raw data into finished intelligence products tailored to specific needs. The production process emphasizes accuracy, timeliness, and relevance, often requiring additional collection to fill information gaps. Analysts aim to provide a clear understanding of the subject, supported by analytical conclusions drawn from the data. This step transforms raw data into actionable intelligence.
Dissemination
The final phase involves conveying the intelligence to consumers in usable forms, such as verbal reports, written documents, imagery products, and databases. Dissemination can occur through physical data exchanges or interconnected networks, ensuring that the intelligence reaches the relevant stakeholders efficiently. This step is critical for enabling informed decision-making based on the gathered and analyzed intelligence.
Utilizing Diverse Data Sources
Effective OSINT relies on accessing a wide array of data sources:
Corporate Records
Extracting information from corporate filings, financial reports, and business registries provides insights into organizational structures and activities.
Blogs and Forums
Monitoring discussions on blogs, forums, and social media platforms uncovers public sentiment, emerging trends, and informal communications.
Publicly Accessible Databases
Utilizing publicly available databases, such as government records, legal documents, and academic repositories, enriches investigative data.
Deep Web and Dark Web
Delving beyond the surface web into the deep web and dark web reveals obscured information, including illicit activities and underground networks.
Expanding Search Horizons
Incorporating the dark web into OSINT strategies offers crucial intelligence on clandestine activities:
Dark Web Insights
Tools designed for secure and anonymous browsing enable investigators to navigate the dark web safely. This access unveils critical details about criminal operations, illegal markets, and threat actors.
Risk Mitigation
Employing specialized technologies ensures ethical data collection and compliance with legal frameworks while mitigating potential risks associated with dark web exploration.
Implementing Intelligent Automation
The volume and complexity of open-source data necessitate the use of intelligent automation tools:
Data Collation
Automated processes gather information from multiple sources simultaneously, accelerating data aggregation and analysis.
Relationship Mapping
Algorithms identify connections between entities, facilitating the visualization of networks and hierarchies.
Visualizations
Generating maps, charts, and timelines enhances data interpretation, enabling investigators to discern patterns and anomalies effectively.
Choosing the Right Software
Selecting appropriate OSINT tools optimizes investigative efficiency and efficacy:
Comprehensive Search Capabilities
Robust tools enable targeted searches across diverse datasets, ensuring thorough coverage and accuracy.
Anonymity and Security
Secure protocols safeguard investigators' identities during sensitive inquiries, particularly in dark web environments.
Integration and Automation
Platforms that integrate data from various sources streamline workflows, automating repetitive tasks and enhancing productivity.
Conclusion
By integrating these sophisticated OSINT techniques, investigators can uncover valuable insights crucial for decision-making and strategic planning. Harnessing the power of diverse data sources, intelligent automation, and secure technologies not only enhances operational efficiency but also ensures ethical and compliant intelligence gathering practices. As digital landscapes continue to evolve, mastering OSINT techniques remains indispensable for staying ahead in the realm of information security and strategic analysis.