Digital Forensics in Modern Investigations
Digital forensics is often perceived as being limited to digital and computing environments. However, its influence extends far beyond these realms, significantly impacting society at large. As computers and digital devices permeate nearly every aspect of daily life, the role of digital evidence has become indispensable in resolving various crimes and legal disputes, whether they occur in the digital or physical world.
Every connected device generates an enormous amount of data, recording user activities and autonomous device functions, such as network connections and data transfers. This applies to a wide array of devices, including cars, mobile phones, routers, personal computers, traffic lights, and other systems within both private and public sectors.
Digital evidence plays a crucial role in investigations and legal proceedings for various issues, such as:
· Data Theft and Network Breaches: Digital forensics is essential for determining how a breach occurred and identifying the perpetrators.
· Online Fraud and Identity Theft: It helps assess the breach's impact on organizations and their customers.
· Violent Crimes: In cases like burglary, assault, and murder, digital forensics retrieves evidence from mobile phones, vehicles, or other nearby devices.
· White-Collar Crimes: It aids in gathering evidence to identify and prosecute crimes such as corporate fraud, embezzlement, and extortion.
Within an organization, digital forensics is crucial for investigating both cybersecurity and physical security incidents. Most commonly, digital evidence forms a core part of the incident response process, helping to detect breaches, identify root causes and threat actors, eradicate threats, and support legal teams and law enforcement.
To effectively enable digital forensics, organizations must centrally manage logs and other forms of digital evidence, ensuring that they are retained for a sufficient period and safeguarded against tampering, unauthorized access, or accidental loss.

Types of Digital Forensics
Computer Forensics
Involves the analysis of data stored on computers and other digital devices. It is commonly used to investigate cybercrimes, data breaches, and intellectual property theft.
Network Forensics
Focuses on monitoring and analyzing network traffic to detect and investigate security incidents, such as network intrusions, data exfiltration, or malware infections.
Mobile Device Forensics
Concerned with extracting and analyzing data from mobile devices like smartphones and tablets. This is crucial for criminal investigations and legal cases involving mobile data.
Database Forensics
Examines databases to uncover evidence related to data breaches, unauthorized access, or data manipulation.
Cloud Forensics
Involves investigating data stored in cloud environments. It’s essential for cases involving cloud-based services, such as data leaks or account compromise.
Digital Forensic Techniques
Digital forensics involves creating copies of a compromised device and then using various techniques and tools to examine the information. Digital forensics techniques help inspect unallocated disk space and hidden folders for copies of encrypted, damaged, or deleted files. Here are common techniques:
Reverse Steganography
Cybercriminals use steganography to hide data inside digital files, messages, or data streams. Reverse steganography involves analyzing the data hashing found in a specific file. When inspected in a digital file or image, hidden information may not look suspicious. However, hidden information does change the underlying has or string of data representing the image.
Stochastic Forensics
Stochastic forensics helps analyze and reconstruct digital activity that does not generate digital artifacts. A digital artifact is an unintended alteration of data that occurs due to digital processes. Text files, for example, are digital artifacts that can content clues related to a digital crime like a data theft that changes file attributes. Stochastic forensics helps investigate data breaches resulting from insider threats, which may not leave behind digital artifacts.
Cross-drive Analysis
Cross-drive analysis, also known as anomaly detection, helps find similarities to provide context for the investigation. These similarities serve as baselines to detect suspicious events. It typically involves correlating and cross-referencing information across multiple computer drives to find, analyze, and preserve any information relevant to the investigation.
Live Analysis
Live analysis occurs in the operating system while the device or computer is running. It involves using system tools that find, analyze, and extract volatile data, typically stored in RAM or cache. Live analysis typically requires keeping the inspected computer in a forensic lab to maintain the chain of evidence properly.
Deleted File Recovery
Deleted file recovery, also known as data carving or file carving, is a technique that helps recover deleted files. It involves searching a computer system and memory for fragments of files that were partially deleted in one location while leaving traces elsewhere on the inspected machine.
Case Studies of Digital Forensics
Corporate Embezzlement Investigation
In a corporate embezzlement case, a financial institution suspected an employee of illicitly transferring company funds into personal accounts. A digital forensics expert was brought in to examine the suspect's PC, including hard drives, emails, and chat logs. Through meticulous analysis, the investigator discovered that the suspect had attempted to cover their tracks by deleting incriminating files and conversations. However, using advanced recovery tools, the investigator successfully retrieved the deleted data. The recovered files included spreadsheets documenting unauthorized transactions, as well as chat logs where the employee discussed these activities with an accomplice. This digital evidence was crucial in building a strong case against the employee, ultimately leading to a conviction for embezzlement.
Cybercrime Investigation
In a large-scale cybercrime investigation, law enforcement agencies targeted a sophisticated criminal network involved in distributing illegal content online. The suspects operated in multiple locations, using encrypted laptops and dark web platforms to evade detection. Digital forensics teams were deployed to analyze the seized digital devices, including computers, servers, and external storage. Through network forensics, investigators traced the origins of the illicit content and uncovered communication logs that linked the suspects to various dark web marketplaces. Forensic experts were able to decrypt the files and identify the methods used to anonymize the network, leading to the identification of the key members of the criminal group. The digital evidence collected was instrumental in prosecuting the suspects, resulting in multiple convictions and the dismantling of the criminal network.
Intellectual Property (IP) Theft
In a case involving intellectual property (IP) theft, a software company discovered that proprietary source code had been leaked and was being used without authorization by a competitor. The company hired certified forensic investigators to track down the stolen IP. The investigation involved analyzing the digital assets of current and former employees, including mobile devices, cloud storage accounts, and company servers. Forensic experts employed advanced decryption techniques to access encrypted data and traced the movement of the stolen files through various digital channels. They were able to pinpoint the source of the leak to a disgruntled ex-employee who had transferred the source code to personal cloud storage before leaving the company. The digital evidence gathered not only led to legal action against the individual responsible but also facilitated the recovery of the stolen IP, safeguarding the company's competitive advantage.
The Challenges of Digital Forensics
Digital forensics comes with its own challenges, including:
Encryption
Better encryption makes data retrieval more challenging for forensic investigators conducting digital forensics research.
Data volume and complexity
Digital forensic investigators need time and resources to search gigabytes of data. Data types and architectures, from traditional computer media to complicated database systems and cloud storage, complicate investigations.
Rapid technological changes
Technology changes quickly, and digital forensic tools and methodologies must adapt to those changes. Digital investigations require frequent OS, software, and device updates for successfully extracting data. Ideally, investigators must invest in cutting-edge forensic methods and technology and participate in continuous learning.
Legal and ethical considerations
The database forensics framework operates within strict ethical and regulated boundaries. Officers and certified forensic practitioners must be familiar with national computer crime laws and privacy legislation. When legislation changes, practitioners might face search and seizure and data privacy issues and need to change their methods.
Remote and decentralized data locations
Accessing digital forensic data in remote locations can be difficult because of cloud platforms and decentralized data storage servers. As a result, investigators need exceptional data imaging, data recovery, and remote data security and analysis skills.
Advances in technology makes digital forensics more crucial. Digital forensic consultants and practitioners must adapt to each trend and difficulty, as well as change their ways to keep up with crime and technology. Our increasingly linked world requires digital forensics for criminal investigations and ensure digital security.
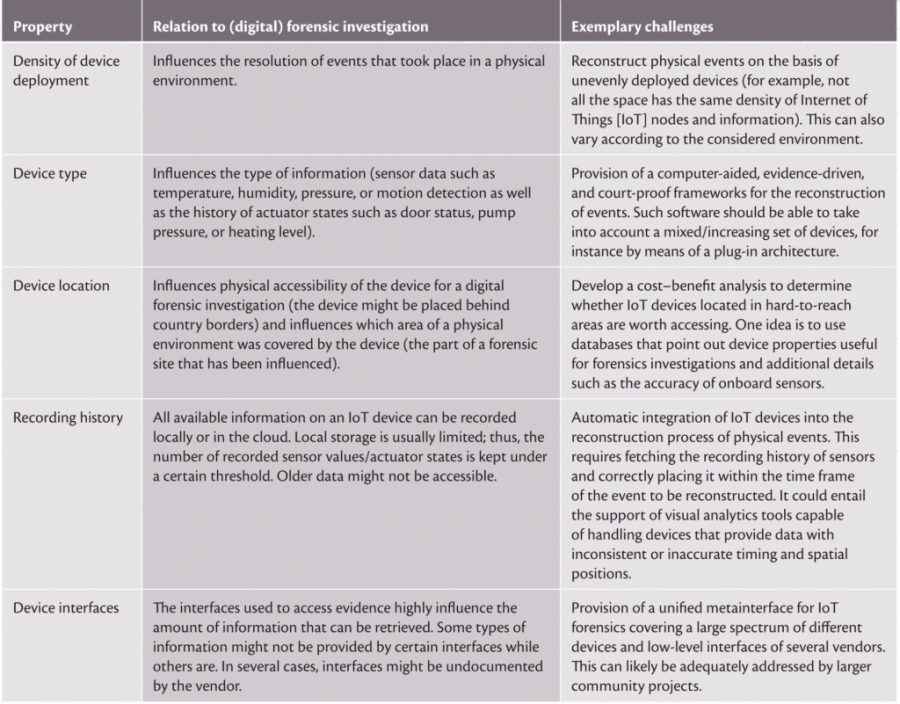
The Future of Digital Forensics
Technical advances and the ever-changing world of digital offenses have led to several cybercrime forensics forecasts.
Artificial intelligence (AI), the cloud, and IoT devices will transform digital forensics. AI will increase data analysis in digital forensic investigations, particularly for investigations involving significant data volumes. Cloud infrastructure will require novel methods of data extraction to exploit forensic information and create forensic analysis issues.
Digital forensics may move beyond phones and PCs. As the field of electronic evidence analysis grows, the use of database, network, and mobile device forensics will increase.
Conclusion
As technology continues to advance, the field of digital forensics must evolve in tandem to address the growing complexities of digital crimes. From leveraging artificial intelligence to navigating the challenges of cloud-based data storage, digital forensic practitioners are at the forefront of ensuring justice and security in an increasingly connected world. The future of digital forensics is poised to expand beyond traditional devices, offering new tools and methodologies to meet the demands of an ever-changing digital landscape.