Comprehensive Guide to Cyber Threat Intelligence: Importance, Types, and Integration Strategies
Understanding Cyber Threat Intelligence
Cyber Threat Intelligence (CTI) involves assessing, validating, and reporting on current and potential cyber threats to maintain an organization’s situational awareness. It is a dynamic technology utilizing data collection and analysis from historical threats to block and remediate cyber attacks. CTI isn't a hardware solution but relies on tactics, techniques, and procedures, forming a crucial part of a security architecture. This intelligence helps identify who or what is attacking, why the organization is targeted, and how to detect compromises. Beyond IT teams, the entire organization benefits from a well-implemented CTI system, as it empowers proactive threat prevention and mitigation.

Types of Cyber Threat Intelligence
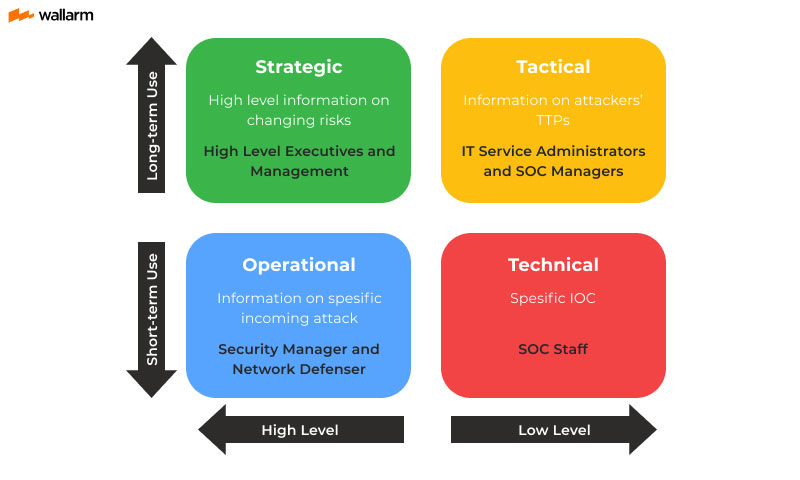
Cyber threat intelligence (CTI) encompasses various categories, each offering distinct levels of technical and non-technical details relevant to understanding and mitigating cyber threats. These categories ensure comprehensive coverage of the threat landscape, tailored to the needs of different stakeholders within an organization.
Strategic Intelligence
Strategic threat intelligence provides a high-level overview of the broader threat landscape, focusing on geographic, political, and organizational trends. This type of intelligence delivers insights into the overarching context of cyber threats, highlighting vulnerabilities and potential impacts on the business. Typically presented to C-level executives and key decision-makers, strategic intelligence helps in assessing the need for new security measures and tools by identifying emerging threats and their potential consequences.
Operational Intelligence
Operational threat intelligence involves analyzing human behavior, threat groups, and real-world activities leading to cyber-attacks. This intelligence is derived from direct sources such as attackers, social media, and chat rooms. Operational intelligence is crucial for predicting the timing, nature, and specifics of planned attacks, enabling cybersecurity professionals to prepare and respond proactively to imminent threats.
Tactical Intelligence
Tactical threat intelligence focuses on the methods and techniques used by attackers. It includes details about attack vectors, infrastructures, tools, and the types of technologies and organizations being targeted. This intelligence helps cybersecurity specialists devise avoidance strategies and understand the likelihood of being targeted by specific types of attacks. Tactical intelligence supports the formulation of defense mechanisms by providing actionable insights into the operational tactics of adversaries.
Technical Intelligence
Technical threat intelligence is centered on concrete evidence of ongoing attacks or indicators of compromise (IOCs). This includes specific details about the tools and resources used by attackers, such as IP addresses, phishing emails, and malicious domains. Technical intelligence allows for immediate responses to detected threats by identifying and mitigating the indicators of active breaches. It is essential for real-time threat detection and response, enabling rapid containment and remediation efforts.
Why is Cyber Threat Intelligence Important?
Cyber threat intelligence (CTI) is crucial because it provides actionable insights derived from detailed threat analysis, enabling organizations to defend against cyber threats proactively. This intelligence automates the identification and blocking of malicious activities across networks, reducing the need for manual intervention. By investing in CTI, businesses can tap into extensive threat databases, enhancing the effectiveness of their security measures. This proactive approach ensures robust defenses against evolving cyber threats, thereby improving the overall security posture of the organization.
Minimizes Cyber Threat Risks
CTI significantly reduces the risk of cyber attacks by increasing visibility into potential threats and emerging attack methods. This knowledge enables security teams to develop effective countermeasures, safeguarding sensitive data and maintaining operational continuity.
Enhances Security Team Efficiency
Integrating CTI solutions, often equipped with automated features like AI, enhances the efficiency of cybersecurity teams. These tools can process and validate data, allowing teams to focus on strategic defense measures and reducing response times and false alarms.
Facilitates Collaborative Knowledge Sharing
CTI fosters collaboration among organizations through information-sharing communities and threat intelligence feeds. By sharing insights on recent attacks, organizations can learn from each other's experiences and improve their defenses.
Provides In-depth Threat Analysis
CTI offers detailed analysis of cyber threats, including tactics, techniques, and procedures used by attackers. This comprehensive understanding helps security specialists anticipate and mitigate future attacks, thereby strengthening the organization’s cyber defenses.
By leveraging the benefits of cyber threat intelligence, businesses can maintain a proactive and informed security posture, ensuring better protection against the ever-evolving landscape of cyber threats.
Who Benefits from Cyber Threat Intelligence?
Cyber threat intelligence provides significant advantages to organizations of all sizes and across various industries by transforming raw data into actionable insights about potential attackers and their methods. This intelligence enables organizations to anticipate and respond to threats more effectively, ensuring a robust security posture.
Small to Midsize Businesses (SMBs)
For SMBs, cyber threat intelligence is invaluable because it grants access to comprehensive threat databases that may otherwise be unattainable. This access levels the playing field, allowing smaller organizations to defend against sophisticated cyber threats that they might not have the resources to combat on their own.
Large Enterprises
Larger organizations benefit from cyber threat intelligence by using detailed analysis to understand the tools and tactics of malicious actors. This intelligence helps in creating more effective defense strategies and improving overall security measures.
Security and IT Analysts
Security and IT analysts leverage threat intelligence to enhance their ability to detect and prevent threats. By understanding the nature and methods of potential attacks, they can implement more targeted and effective security measures.
Security Operations Centers (SOCs)
SOCs use threat intelligence to prioritize incidents based on risk assessment and potential impact. This prioritization allows for more efficient allocation of resources, ensuring that the most critical threats receive the necessary attention.
Intel Analysts
Intel analysts benefit from cyber threat intelligence by being able to track and monitor threat actors more effectively. This continuous monitoring helps in understanding attacker behavior and predicting future threats, thereby strengthening the organization's defensive capabilities.
Executive Management
For executive management, cyber threat intelligence provides a clear understanding of the cyber risks facing the organization, their potential impact on operations, and the strategies needed to mitigate them. This strategic insight supports informed decision-making and resource allocation.
Stages of the Cyber Threat Intelligence Lifecycle
Cyber threat intelligence (CTI) is not a linear process but a continuous cycle that converts raw threat data into actionable insights to bolster an organization's security posture. This lifecycle comprises six distinct phases:
1. Requirement Gathering
This initial phase involves collecting the needs and objectives from all stakeholders. Tasks include:
· Defining the organization's attack surface and potential impacts of cyberattacks.
· Identifying areas the CTI program must cover.
· Understanding attackers' motivations and necessary counteractions.
2. Data Collection
Once requirements are set, relevant data is gathered to meet the defined goals. Typical sources include:
· Public data (news sites, forums, blogs).
· Network traffic logs.
· Social media.
· Threat data feeds from cybersecurity firms.
· Expert interviews and cyber counterintelligence sources like passive DNS monitoring and honeypots.
· Malware analysis.
3. Data Processing
Raw data must be processed into a format suitable for analysis. Processing tasks may involve:
· Data normalization, sorting, sampling, validation, and aggregation.
· Extracting relevant terms from network traffic logs.
· Translating foreign language content.
· Validating data from interviews.
4. Data Analysis
In this phase, processed data is interpreted to meet the objectives set in the requirement-gathering phase. Analysis identifies threat patterns and potential impacts using techniques like statistical and hypotheses-based analysis. It results in actionable recommendations such as:
· Necessary investments.
· Immediate threat actions.
· Further investigation of specific threats.
5. Dissemination
The analysis results are shared with stakeholders in an easily understandable format. Best practices include:
· Presenting results concisely.
· Avoiding technical jargon.
· Using charts and graphs for clarity.
6. Feedback
Stakeholders provide feedback on the intelligence report, indicating necessary changes and the frequency of future reports. This feedback is crucial for refining the CTI program.
Integrating Cyber Threat Intelligence with Existing Security Measures
Incorporating cyber threat intelligence (CTI) into existing security frameworks is essential for enhancing an organization’s overall defense capabilities. This process involves several key actions:
Aligning Intelligence with Security Controls
Connect threat intelligence insights to existing security mechanisms like firewalls, IDS, and endpoint protection systems. This alignment ensures that the intelligence is actively used to improve these controls.
Automating Threat Responses
Leverage automation tools to facilitate real-time reactions to detected threats. By integrating CTI with security orchestration, automation, and response (SOAR) systems, routine threat detection and response tasks can be automated, allowing security teams to concentrate on more complex issues.
Continuous Monitoring and Updating
Establish a system for ongoing monitoring and updating of security measures based on the latest threat intelligence. This approach helps the organization remain agile and responsive to new and evolving threats.
Training and Awareness
Conduct regular training sessions and awareness programs to educate security teams and other staff on the application of threat intelligence. This education ensures that CTI insights are effectively utilized in daily operations and decision-making processes.
Collaboration and Information Sharing
Promote a collaborative environment within the organization and with external partners, such as industry groups and threat intelligence communities. Sharing threat intelligence can provide additional insights and enhance the organization's ability to anticipate and mitigate threats.
Conclusion
Cyber threat intelligence (CTI) is a vital component of modern cybersecurity strategies, offering actionable insights to defend against a wide array of cyber threats. By continuously gathering, analyzing, and disseminating threat data, organizations can stay ahead of potential attackers and fortify their defenses. Integrating CTI into existing security measures, automating responses, and fostering a culture of collaboration and continuous learning ensures that organizations are well-prepared to tackle the ever-evolving threat landscape. Embracing CTI not only strengthens an organization's security posture but also empowers it to proactively mitigate risks, ensuring long-term resilience against cyber threats.