Open Source Intelligence: How to investigate domain names
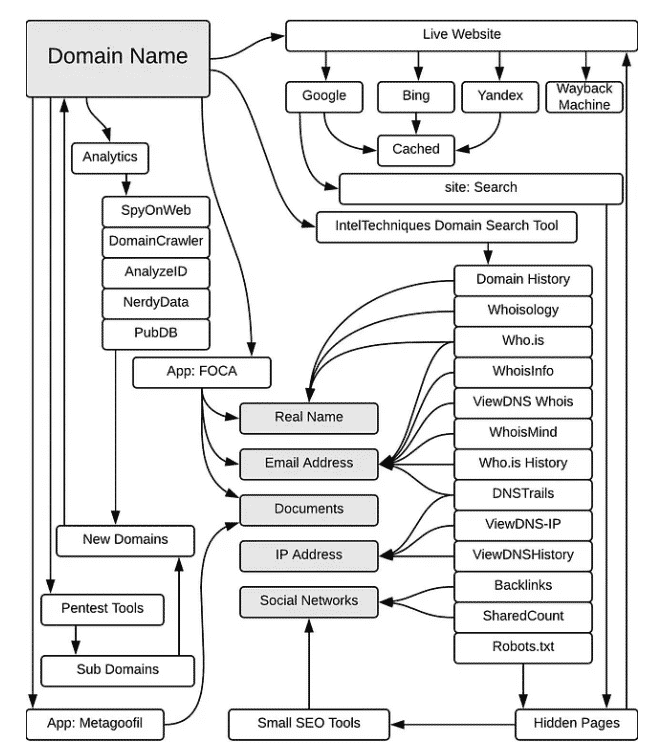
If an individual or organization owns a website, you should know how to access
information about that website. The investigation may reveal the operating system
used, software version, personal contact information, etc. It is recommended to
investigate without "touching" the target's environment, a technique called passive
reconnaissance - which involves using a footprint of tools and resources that can
help obtain more information about the target without having to interact with it
directly. Below I describe methods for obtaining information while remaining hidden.
Google Dorks
Google Dorks is a passive information
gathering method that was already mentioned above. Here I’m going to show what
queries might be useful during domain investigation.
·
site:example.com — limits search to a particular website or domain.
·
filetype:DOC — returns DOC files or other specified types, such as PDF, XLS
and INI. Multiple file types can be searched for simultaneously by separating
extensions with “|”.
· intext:word1 — search for pages & websites
that contain the specific word that you are searching.
· allintext: word1
word2 word3 — search for all the given words in a page or website.
·
related:example.com — will list web pages that are “similar” to a specified
web page.
· site:*.example.com — show all subdomains. Asterisk acts
as a substitute for a whole word or words in search queries.
Whois
Whois provides information about the
registered user or assignee of an Internet resource, such as a domain name, IP
address block, or autonomous system. There are many Whois resources, and these are
good ones: whois.icann.org and
whois.com.
Reverse
Whois
Reverse Whois gives you a list of domains that have the
same organization name or email address in their Whois record. For example, if you
are investigating a company with the name “John Doe Inc.” you can see all the other
domains registered under the “John Doe Inc.” One of my favorite websites
is viewdns.info as it has an extensive toolkit,
including reverse whois lookups.
Same IP
Often discovering which site is running on
the same server as the target site will reveal valuable information. For example,
you may find subdomains or development sites. Often, the service provider hosting
this site is also responsible for other services - use
www.atsameip.intercode.ca and
www.sameip.org to check.
Passive
DNS
Using only DNS records, you can see which IP resolves to a
name or which name resolves to an IP. Sometimes this is not enough, and this is
where passive DNS records come in handy. They allow checking all names that resolved
to the IP under study, so you can build a useful resolution history. My favorite
product is RiskIQ Community Edition
because it provides information beyond just passive DNS.
VirusTotal or
SecurityTrails can also be used for this
purpose.
Reputation, malware and referrals analysis
Reputation is important to know who you are dealing with and whether the
site is trustworthy. If there is any doubt, a malicious activity check using a free
online tool may save you the trouble of opening the site in a VM or performing other
preventive measures. The recommended analysis is a search for internal and external
HTML links. While testing alone will not provide you with accurate results, it is
still one of the methods that can show you connected domains.
·
www.siteworthtraffic.com - Analyzes
website traffic (users, page views) and estimates how much revenue it can generate
through advertising.
· www.alexa.com -
Analyzes website traffic and competitors, shows what they are doing better, and
provides suggestions for SEO improvements.
·
www.similarweb.com - Analytical tool that
provides in-depth information about website or mobile rankings, performance, traffic
sources, etc. Most importantly, it performs referral analysis.
·
https://sitecheck.sucuri.net - Scans
websites for known malware, blacklist status, website errors and outdated software.
· www.quttera.com - Provides free malware
scanning and comprehensive reports including malicious files, suspicious files,
blacklist status and more.
· www.urlvoid.com
- helps you detect potentially malicious websites. In addition, it provides more
information about domains (IP addresses, DNS records, etc.) and cross-references
them with known blacklists.
IoT Search Engine
The
IoT (Internet of Things) search engine shows you devices connected to cyberspace -
think Google search, but it's for connected devices. Why is this useful?
For
example, instead of using Nmap to actively scan for ports and services, you can
request existing available information about open ports, applications and protocols.
Shodan.io is a popular Internet scanner
with a public API and integration with many security tools. For marketers, it
provides data about product users and their locations. Security researchers use it
to discover vulnerable systems and access various IoT devices.