How to access the dark web safely?
The Dark Web, or Darknet, is a
subset of the Internet, a small part of the deliberately hidden deep web that can be
accessed by special means. The terms dark web and darknet are often used
interchangeably.
The most common type of site associated with the Dark Web
is a marketplace for buying and selling illegal goods such as drugs, guns, and
stolen credit card numbers. The darkest corners are used to hire killers, engage in
human trafficking and exchange child pornography.
But more importantly, the
dark web contains content and data that can be accessed anonymously. It can be
blogs, forums, chat rooms or private game servers.
The beauty of the dark
web is the anonymity. As long as the necessary precautions are taken, no one knows
who anyone else is in the real world. Users' identities are safe from government and
corporate prying eyes.
There are many options on how to access the Dark Web.
The chart below lists three options that can be used when connecting to the Dark Web
to provide a more secure level of protection. Each has different barriers to entry
and users will have different requirements, budgets or considerations as part of
their connection method.
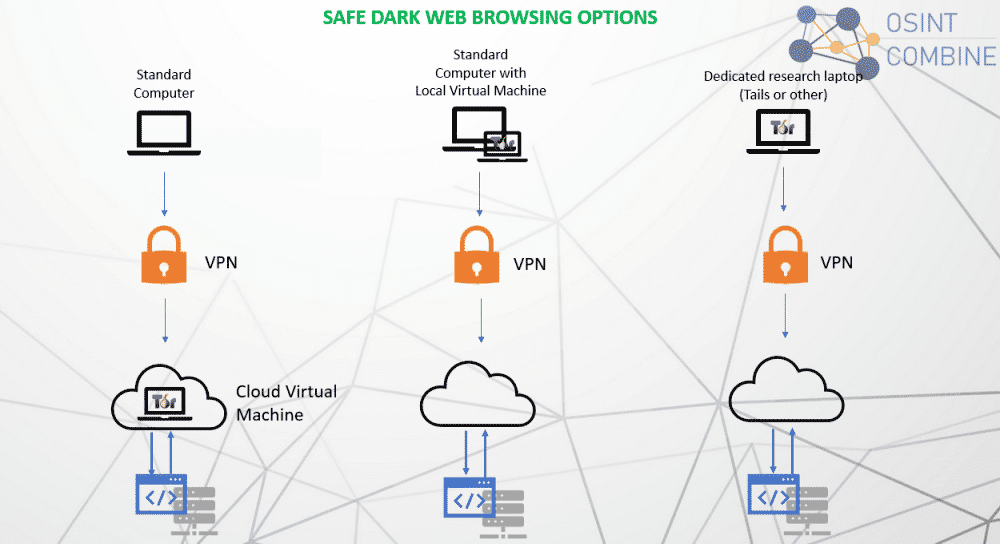
Method 1
· Configure a cloud virtual machine or desktop
using providers such as Amazon Workspaces (https://aws.amazon.com/workspaces/),
Google Cloud (https://cloud.google.com/compute), Microsoft Azure VDI
(https://azure.microsoft.com/en-au/free/virtual-machines) or Paperspace
(https://www.paperspace.com/). There are other providers but these are relatively
cost-effective when used for small periods of time
· Install
Tor/darknet
access on the cloud machine and use that for your research
· Connect to the
darknet from within the cloud virtual machine
· Note: If you want to use Tor
privately, you can use a VPN or Tor Bridge (a Tor node that is not publicly
indexed). Tor users in the U.S. in particular may want to use a VPN because it's
faster and more reliable.
Method 2
· Install and
configure a local virtual machine using a platform such as VirtualBox
(https://www.virtualbox.org/) and downloading pre-configured VM's (such as the TL
VM: https://www.tracelabs.org/initiatives/osint-vm) or installing an operating
system from scratch
· Install Tor/Darknet Access on a Virtual Machine
· Configure VPN on standard workstations
· Connect to the dark web
from inside a virtual machine
Method 3
· Configure
standalone research laptop/computer (consider using a bootable operating system like
Tails to reduce attribution)
· Configure VPN on research laptop
·
Install Tor/darknet access locally on your research laptop
· Connect locally
from your research laptop to the dark web